One of the most interesting and useful tools that the Cloud has developed are crime maps online. When the Global Positioning System was developed it was envisioned simply as a tool to assist Military leaders to keep track of assets on the battlefield. Mapping has grown so far beyond this relatively simple use that it would be nearly as hard to do without as cell phones.
Of course there is much more to mapping than peeking at your smart phone to locate the nearest latte’ stand or even watching the cops on TV tracking the bad guys on their tablets. Mapping combined with Big Data is useful in everyday and long term risk management, at the personal and corporate levels.
Risk Management, whether as a formal, corporate process or an daily personal evaluation of the safest route to the grocery store, depends on getting all the useful information you can find and process. Knowledge of the potential for criminal activity in an area is useful information, whether we are allocating law enforcement resources or looking for the best place to park our car on a late night.
We are all familiar with the pre-Cloud concept of crime mapping from watching old detective movies. The detectives are sitting in the station, cigarettes dangling from their mouths, staring at a map tacked to the wall which shows all of the bad guy’s hits. If he stares long enough, the detective will figure out where the crook is going to strike next, and then the cops can be there to nab him.
Using crime mapping as a risk management tool is a similar process, except that we can use the resources of the cloud to do the hours of staring at the map for us. The data that goes into a crime mapping application combines a mapping app with crime data from law enforcement. The law enforcement data is usually part of the public record and available to anyone. Google Maps is the most popular mapping application, although app developers are free to use the application whose interface they are most familiar and comfortable with.
Whenever I hear or see a police scanner I think of my old Granddad.
Back in the mid-70’s Granddad got a police scanner which ran all day and night in his bedroom. My grandparents lived on a hill over looking a medium sized city in Oregon. Not a big enough town that there would be constant chatter on the scanner, but enough that when something really exciting happened, Granddad could take his binoculars to the back porch and watch what was going on.
The Crime Maps available online for the general public on mobile devices do not all provide the immediacy that Granddad’s scanner had. The data that the app uses may take minutes or hours to update for the general public. Some of the developers who are building crime mapping are tailoring their services to meet the needs of police departments and other first responders.
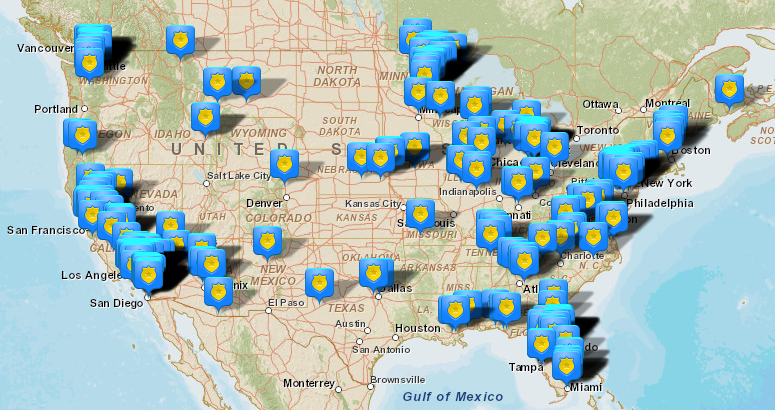
The Omega Group, developers of CrimeMapping.com Mobile app have also developed FireView, an analysis tool for fire departments to facilitate tracking fire and EMS responses. CrimeView and CrimeView NEARme are leading desktop and mobile analytical tools for law enforcement professionals. The CrimeMapping.com Mobile app allows users to view maps of crime activity near their current location, as well as investigating crime history near homes, businesses and schools. Incidents can be filtered by the time of occurrence and date. The map will show the type of crime with a distinctive icon, and the app allows filtering by the type of crime as well.
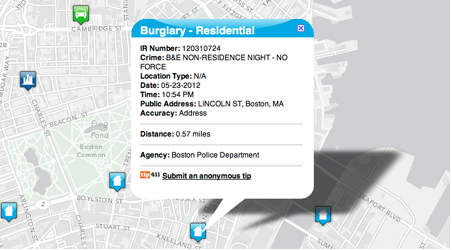
BAIR Analytics has worked with law enforcement agencies around the world for more than 20 years. BAIR stands for Behavioral Analysis & Intelligence Resources, and the company takes a scientific approach to providing public safety, national security and defense industry tools. RAIDS Online is a desktop and mobile tool designed to help law enforcement agencies disseminate crime information quickly to the public they serve. The service combines crime mapping with dashboard analytic tools to enhance public safety. Users are able to filter by date, location, and 27 crime types. Data is displayed with eight layers of limited offense information to protect victim privacy.
Balancing Privacy and Usefulness
One truism of any mapping application is that as more users participate in the service, the better and more accurate the service becomes. Both the Omega Group and BAIR Analytics enjoy the participation of numerous law enforcement agencies in North America and worldwide. Information about an incident may have to go through several administrative layers before the general public gets to see it on their smart phone or tablet. However, if a user discovers that there was a burglary two blocks away from his home within the last few days, he is more likely to pay better attention to the mysterious teenager wandering the neighborhood when he should be in school.
By Peter Knight





