Secure and Scalable CI/CD Pipeline
According to Gartner, a leading research company, worldwide public cloud revenue will grow by 17.3 percent in 2019. Total spending on IT infrastructure products (server, enterprise storage, and Ethernet switches) for deployment in cloud environments is projected to attain a 10.9% year-over-year growth rate, reaching $52.3B this year. Application of cloud services is growing rapidly every year than the rest of the IT. Large scale & highly elastic applications built on any cloud managed services come with a requirement of automatic validation, infrastructure brings up, development and deployment, quality assurance and infrastructure administration. Traditional infrastructure management is being replaced by building CI/CD pipelines for all phases of the product development life cycle.
What is DevOps?
Devops is a union of software development and operations. It is a culture that the company imbibes in the agile development process. The new method of Continuous Integration, Continuous Delivery and Continuous Deployment have come with the rise of DevOps that focuses on:
- Communication, collaboration and cohesion between team
- Applying best practices for change, configuration and deployment automation
- Delivering solution faster
- Monitoring and planning high speed product updates
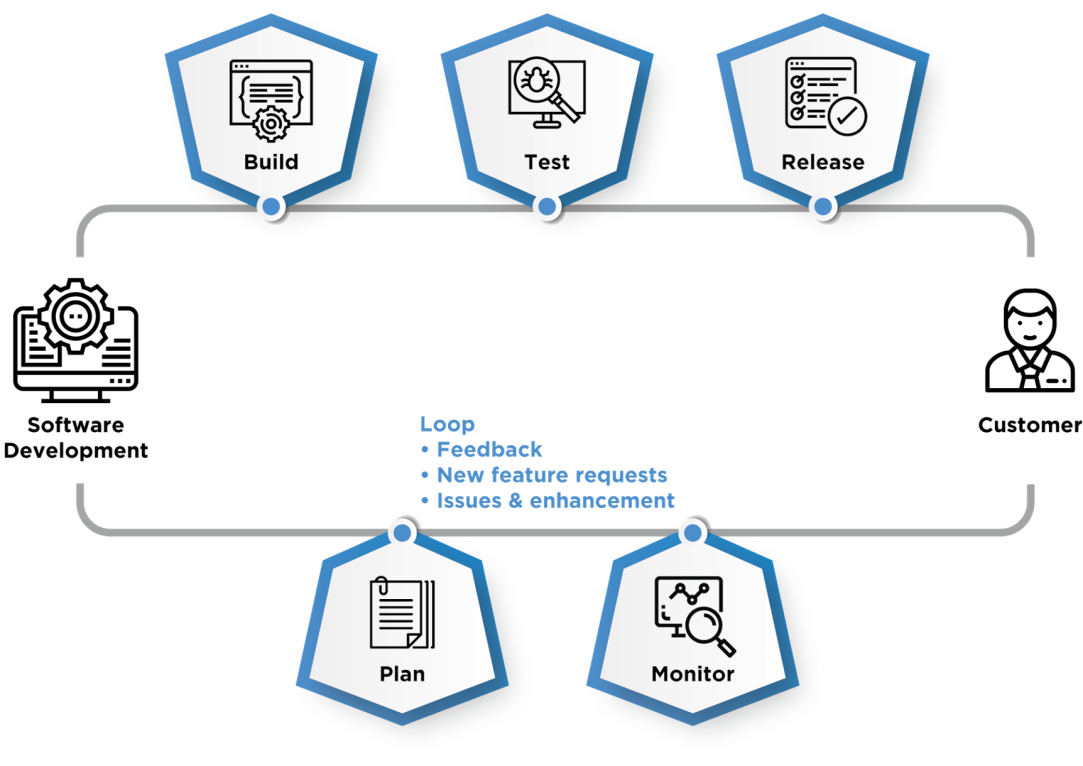
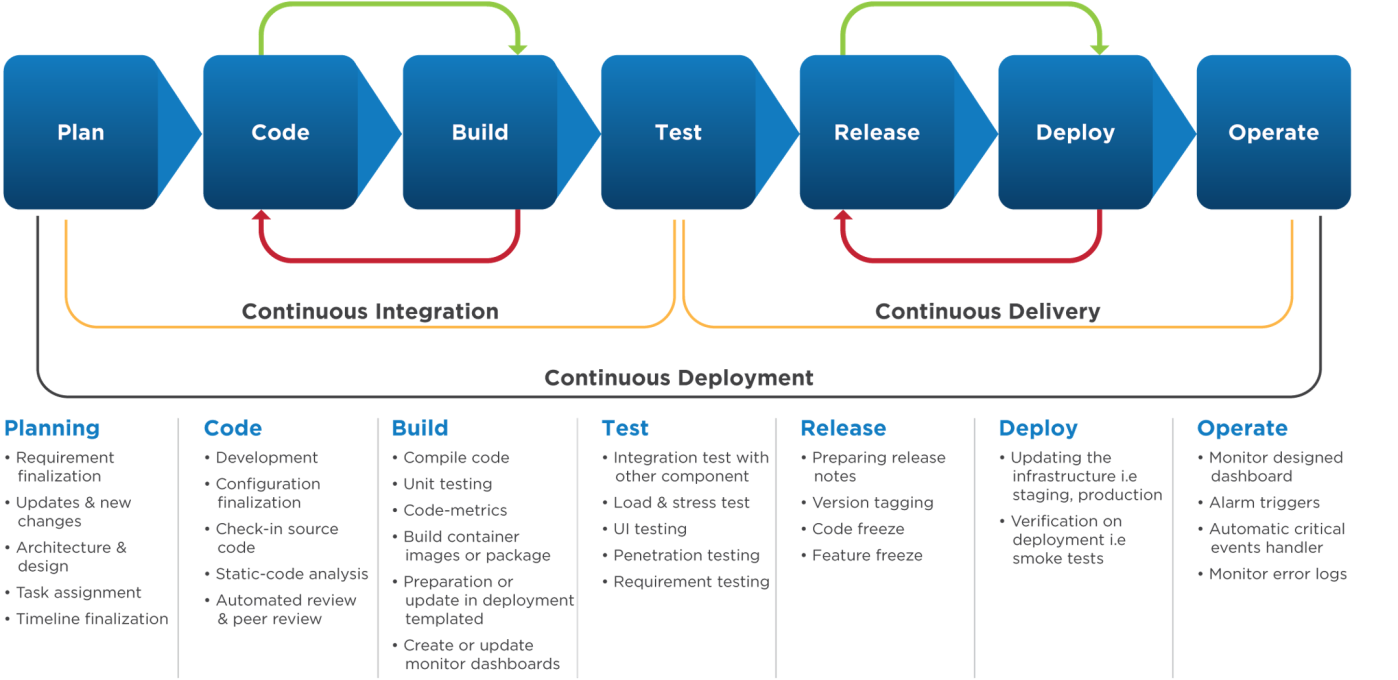
CI/CD gets rid of the manual gate and implements fully automated verification of the acceptance environment to determine whether the pipeline can continue on to production or not.
Continuous Integration focuses on the software development cycle of the individual developer in the code repository. This can be executed multiple times in a day with a primary purpose to enable early detection of integration bugs, tighter cohesion, and more development collaboration. Major activities are like static code analysis, unit tests, and automated reviews.
Continuous Delivery focuses on automated code deployment in testing, staging or production environment, taking the approval of updates to achieve automated software release process, pre-emptively discover the deployment issues.
Benefits of DevOps
- Improved collaboration, operational support and faster fixes
- Increased flexibility, agility and reliability
- Infrastructure security and data protection
- Faster maintenance and upgrades
- Transformation of projects with digitalization strategies
- Increase speed, productivity of business and IT team
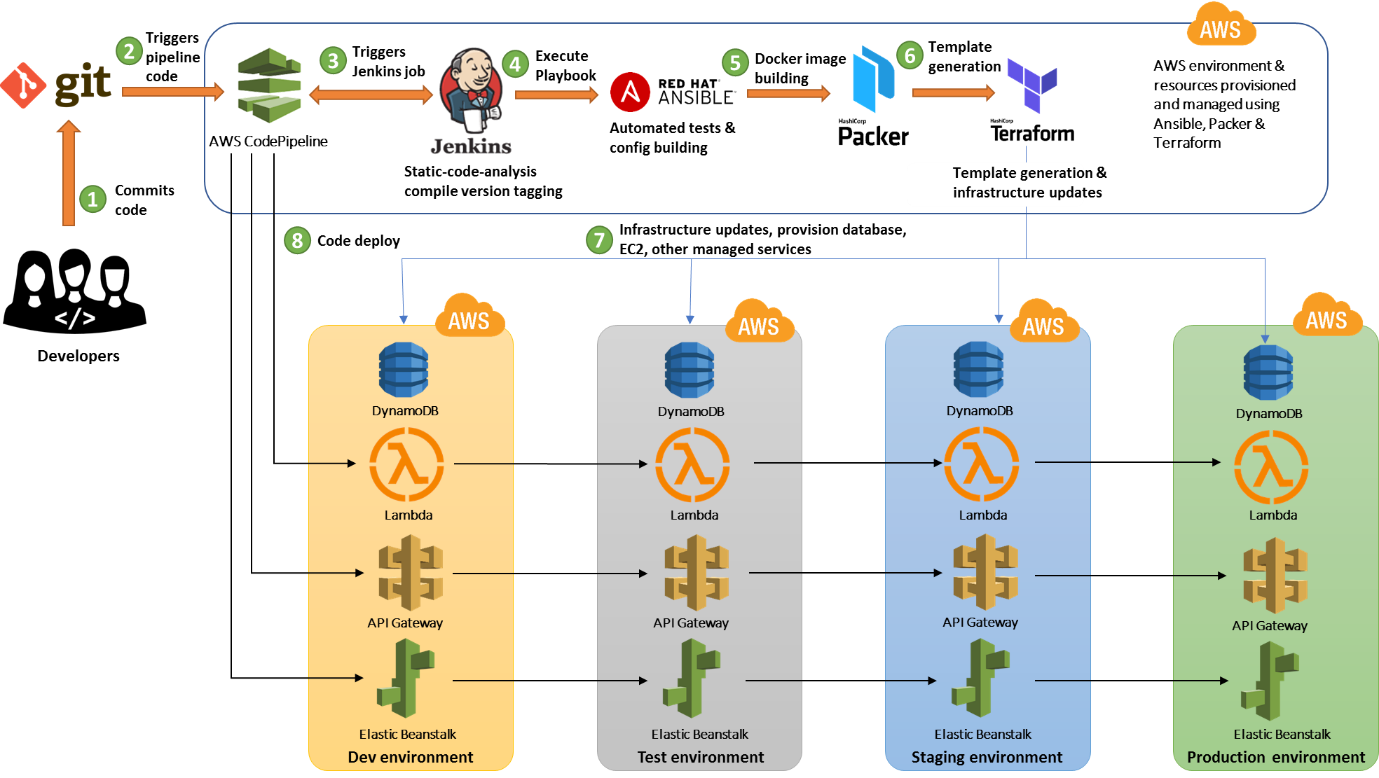
AWS provides the set of developer tools which can be used to achieve DevOps CI/CD in fully secured, scalable, maintainable and easy integration with existing CI/CD tools like Ansible, Chef, puppet, Terraform, etc.
AWS provides CI/CD for Virtual Machine or container-based services, along with options to manage (create, update and delete) all other services like databases, storage, computer, Machine Learning, etc.
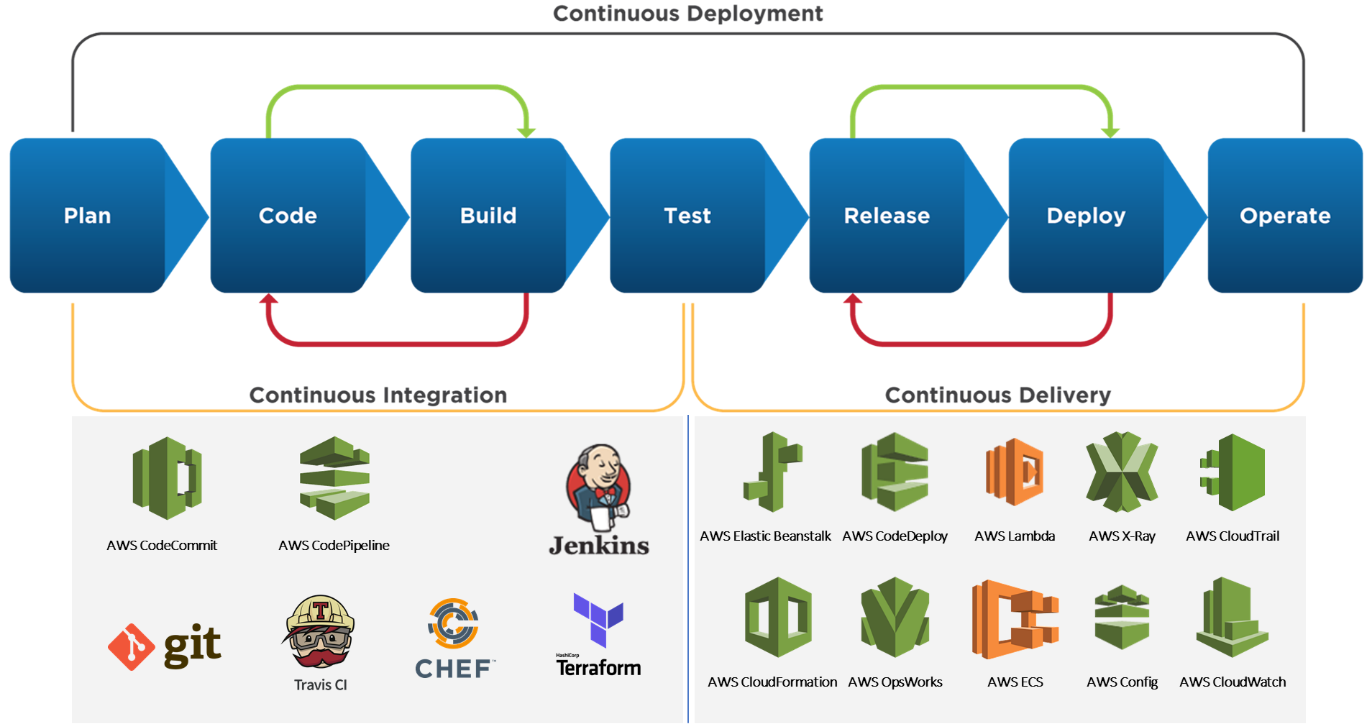
AWS Services for DevOps integration:
- AWS CloudFormation: Provides facility to prepare templates for infrastructure and services. Templates can be written in JSON and YAML and can be managed with versioning. These templates can be executed on Jenkins or any other CI server with AWSCLI. Terraform provides an option for AWS Resource Manager with rich controls and extension with state management.
- AWS OpsWorks: Provides even more levels of automation with additional features like integration with configuration management software (Chef) and application lifecycle management.
- AWS CodePipeline: Continuous delivery and release automation service that aids smooth deployments. Design development workflow for checking in code, building the code, deploying your application into staging, testing it, and releasing it to production.
- AWS CodeCommit: A secure, highly scalable, managed source control service that hosts private Git repositories.
- AWS CodeDeploy: Features provide the ability to deploy applications across an Amazon E2C fleet with minimum downtime, centralizing control and integrating with your existing software release or continuous delivery process. There are third-party tools like Claudia and Serverless which deploys the AWS lambda and elastic beanstalk.
- AWS ElasticBeanstalk: Supports automation and numerous other DevOps best practices including automated application deployment, monitoring, infrastructure configuration, and version management. Application and infrastructure changes can be easily rolled back as well as forward.
- AWS ECS: Highly scalable and secure container service to store docker images.
- AWS XRay: Records and tracks communication between all services and detect the issues in performance and application permission.
- AWS Config: Audit tool to monitor existing AWS account resources and triggers alarm on any change in infrastructure.
- AWS CloudTrail: Enables governance, compliance, operational auditing, and risk auditing.
- AWS CloudWatch: Monitors all AWS resources and applications in real time. Provides bunch of metrics for managed services to design dashboard, alarms and triggers.
Today, traditional function areas are breaking down, with IT and developer roles merging and following a series of systematic principles.
- Infrastructure as a code: Treat infrastructure the same way developer treats the code with all best practices and tests. AWS provides DevOps focused way of creating and maintaining infrastructure.
- Continuous deployment: Core concept of a DevOps strategy. Its primary goal is to enable the automated deployment of production-ready application code.
- Automation: Focuses on setup, configuration, deployment, and support of infrastructure and applications.
- Monitoring: Communication and collaboration is fundamental in a DevOps strategy. To facilitate this, feedback is critical.
- Security: Focus on security is still of paramount importance. Infrastructure and company assets need to be protected, and when issues arises, they need to be rapidly and effectively addressed.
In order to make the cloud software solution journey smooth, efficient and effective, one must follow DevOps principles and practices. DevOps has become an integral part of any cloud solution in today’s technology world and we will continue to see trends related to DevOps Outsourcing and Nearshoring in Europe. Many organizations offer DevOps as a service to automate your product delivery lifecycle to improve collaboration, monitoring, management, and reporting. Services such as It helps to accelerate new services through CI/CD to achieve operational flexibility, cost-effective ways of delivery and avoiding issues in production.
By Chandani Patel









