How To Take Advantage Of “As-A-Service” To Build Business Value
For an IT professional whose status was typically defined by the performance efficiencies of the technology in their data center, it can be a difficult reality to accept that the business value users are able to realize from technology has become the new standard by which all of IT is now being measured. It’s not the technology alone that transforms a business. It’s the way the business accesses and uses that technology that is transformative.
Successful organizations today, as a result, are focusing on transforming their businesses not their technology. For example: “The cloud,” while using enhanced technology at its core, is fundamentally business-model based. For businesses to most effectively harness the power of the cloud, they must change their thinking from how to obtain, manage and pay for technology to how to build, expand and strengthen their business.
Focusing on business outcome instead of acquiring technology is leading savvy CIOs and IT pros to embrace the “as-a-service” model. The business case is compelling: Outsourcing aspects of the IT department’s function by purchasing those functions “as a service” can offload repetitive tasks, reduce capital expenditures and increase the time the IT team has to focus on more strategic work. The key is determining which “as-a-service” functions will be of most benefit to your business.
Here are seven ways to build business value with “as-a-service” solutions:
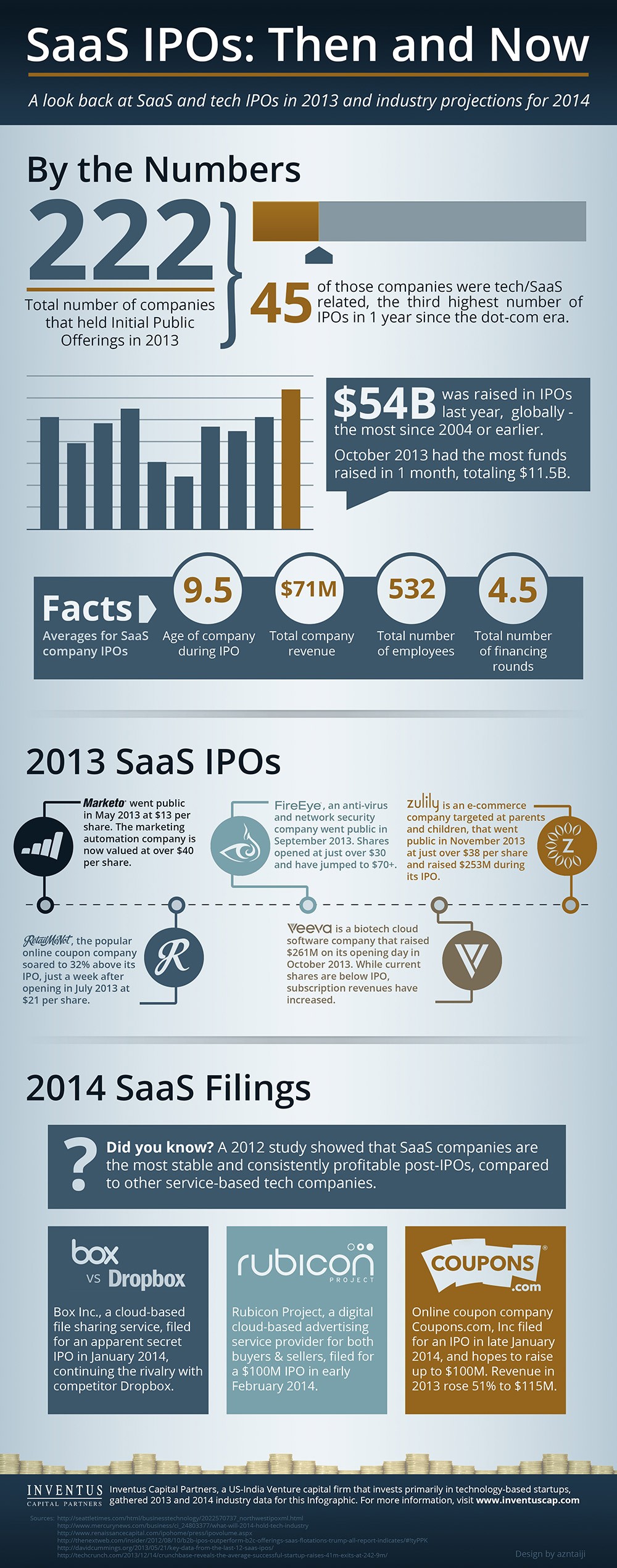
- Software as a Service (SaaS): Software providers excel in designing solutions for vertical markets, but the delivery of that software in an as-a-service model can be challenging. By partnering with a cloud provider who can tailor a SaaS solution to the provider’s product and market, software providers are better able to provide consistent, always-up service to their clients without the cost and hassle of creating and maintaining the in-house infrastructure required to do the job. Likewise, for enterprise organizations that want to access software on a subscription basis, finding a software provider that is going to market in this manner means faster implementations and a subscription fee that can spin up or down with required usage.
- Infrastructure as a Service (IaaS): Need access to additional compute resources from time to time, but not often enough to justify building them in house? Consider an on-demand IaaS offering that is a self-managed, multi-tenant public cloud infrastructure providing the flexible compute resources, memory and storage necessary to complete projects such as test and development, proof of concept, training, bursting or other short-term needs.
- Data Center-as-a-Service (DCaaS): Data centers are typically purpose-built with a 15- to 20-year lifespan, while hardware refreshes must happen every three to four years. So it’s safe to say that, if a data center is between five and 10 years old, there are going to be some major deficiencies. Outsourcing select data center functions to the cloud, co-locating a data center, or deploying an energy-efficient, high-density computing modular data center may be the answer.
- Storage as a Service: Legacy storage simply wasn’t designed with today’s uses in mind. That means there are systemic gaps that may leave an organization exposed to new pressures placed upon it by unpredictable workloads and unrestrained data growth. Most organizations can take advantage of cloud storage, particularly if they have legal requirements to retain large volumes of data for years, including unstructured data like pictures, films and radiology studies, which can result in petabytes of storage and prohibitive costs for media and physical storage. Storage-as-a-service offers affordable monthly terms and the ability to easily increase storage service levels as needed.
- Disaster Recovery as a Service (DRaaS): DRaaS solutions are prepackaged services that provide a standard DR failover to a cloud environment. Customers can buy these services on a pay-per-use basis with varying rates based on required recovery point objectives (RPOs) and recovery time objectives (RTOs). Service Providers either deploy agents to replicate data and applications or use image-based backups to send data to the cloud.
- IT Service Desk-as-a-Service: Certain IT functions contribute to the competitive advantage of an organization, but running a service desk is not usually one of them. If outsourcing an IT service desk can cut costs and increase the level of service to end users without sacrificing quality or impacting competitive advantage, it’s clearly something that IT pros should examine for their organization.
- ITSM – The Mortar in an As-A-Service World: Worried about maintaining control with so many “as-a-service” choices? IT Service Management (ITSM) is a discipline that aligns the delivery of information technology (IT) services with the business at hand. The purpose is to deliver end-to-end services that meet end-user needs. This task has been made more difficult by the introduction of services into the business from providers other than IT, such as cloud services and SaaS, and by the consumerization of service consumption. ITSM is the mortar that holds together the individual components of the new IT delivery model. It’s the solution that maintains order and keeps the reins of control firmly entrenched in the hands of the IT department.
By Kevin Gruneisen






