The term “hackers” might bring to mind visions of dark basements, powerful computers and people with nefarious goals stealing credit card or government data. Most of us, however, don’t associate a hacker with the theft of medical data, but there are a growing number of hackers who are choosing to collect medical data instead of potentially more lucrative information. Why are these hackers so interested in your medical data, and what can you do to make sure you are protected?
Why are so many hackers seeking out medical data instead of their more traditional fare, credits cards and identity data? In a word: profit.
The idea behind stealing data is selling it. If they can’t sell it, there is little to no point in stealing it in the first place. Credit card information, as of right now, goes for about $1/piece. Medical information, which usually includes things like personal information, birth dates, billing information, and medical diagnosis codes, can be sold for between $10-20 each to as high as $60 (As seen in the infographic below discovered via Trend Micro). That’s 10 to 20 times what a hacker can make with the same amount of credit card data.
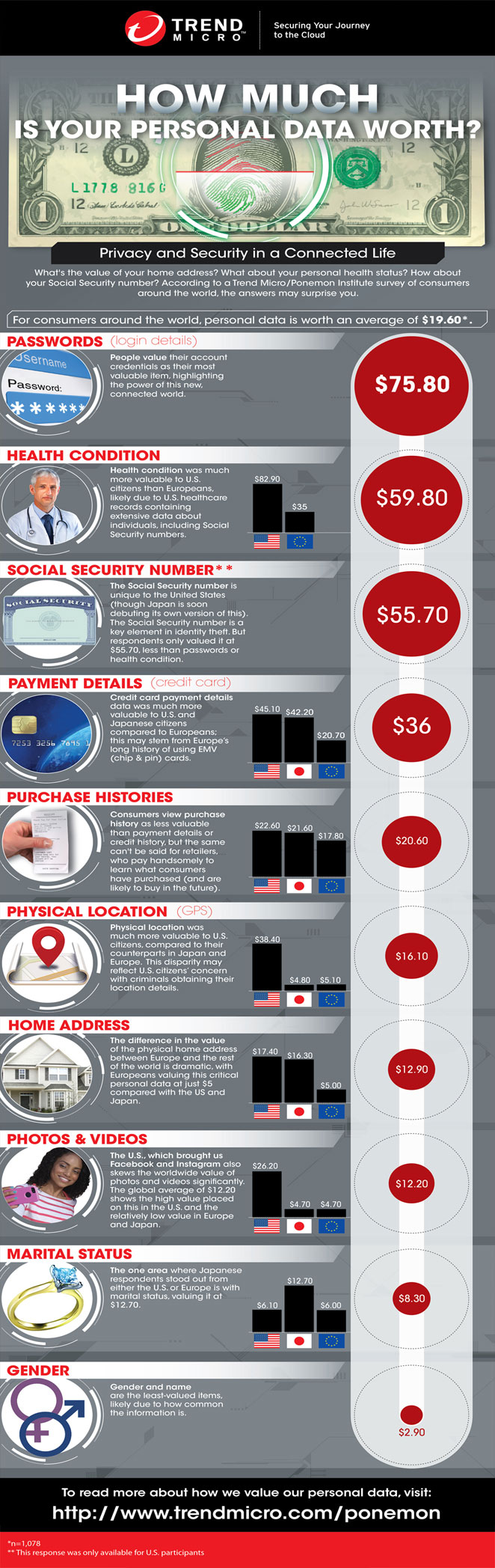
Why is medical data worth so much more than credit card or personal identity data? There are two primary reasons: It’s harder to track and so is less likely to be discovered, and its uses are limitless.
People keep track of their identity and their credit report. There’s an entire industry designed around helping people keep track of their credit scores and protect their identity, and people pay hundreds of dollars into it every single year. Once someone finds something odd on their credit report or history, the stolen data becomes useless.
What most people don’t keep track of is their medical information. No one monitors their medical history to see if someone is using their name or information.
The potential for profit when using stolen medical information is nearly endless. Clever hackers can use an individual’s medical data to obtain fraudulent prescriptions or even purchase medical equipment, which can be later sold for a profit. Depending on the type of information that’s been stolen, these hackers can even trick Insurance Companies into paying for the purchases, increasing the profit threshold exponentially.
How are these hackers making their way into a system that should be otherwise secured? High-tech medical devices and the trend toward IoT-based devices is leaving backdoors for hackers to make their way into otherwise protected systems.
These attacks aren’t malicious. The hackers are not trying to harm patients by shutting down the equipment for compromising its function. Instead, devices that run on older versions of Windows allow hackers to install backdoors in the system so they can walk in and collect any information they might need.
The days of doctor’s offices being filled top-to-bottom with paper medical histories are a thing of the past. In the spirit of expediency and shared information, most medical practitioners have transitioned to electronic data capture (EDC) forms to make your visits more efficient. This also enables doctors and specialists to request data with a couple of keystrokes instead of waiting for hard copies of medical records to be faxed or delivered.
If your medical information is ever hacked or stolen, it can make it hard or even impossible to get proper medical treatment as your medical history is corrupted by whatever diagnosis the hackers think they can use to make the most money. By simply keeping a copy of your electronic medical file, you can restore it to its original state.
About one in 13 people will be affected by a security breach in the medical system at some point over the next five years. So, another thing you can do to protect your medical information is to review your insurance statements and take note of fraudulent activity. Many insurance companies aren’t even prepared for this sort of hack, and it can take them quite a while to discover the breach and take steps to contain it. By going over your insurance statements, you can bring potential breaches to your insurance company’s attention before they may even be aware of it.
Medical data theft may be the next chapter in the ever-growing book on cyber security and information protection, but it’s not the newest and definitely not the first. All we can do is take all the necessary steps to protect ourselves and our information while new security solutions are discovered.
By Kayla Matthews





