The semi-annual Bromium Labs Threat Report has just been released providing an analysis of cyber-attacks and threats which have struck enterprise security in the last six months. It’s found an eruption of ransomware usage as well as an increase in app, browser, and plug-in vulnerabilities and notes that while Microsoft strengthens security, nefarious forces are changing tack and concentrating on ‘drive-by download attacks.’
Though it’s clear that criminals are working harder than ever to get their hands on protected data, it’s not all bad news. Bromium Labs Threat Report also notes that although the amount of Vulnerabilities is constantly rising, they aren’t all being exploited. Unfortunately, there have been several high-profile data breaches and ransomware attacks of late, leaving enterprise security in a somewhat precarious position. Commenting exclusively to CloudTweaks, Bromium EVP and Chief Security Architect, Rahul Kashyap, states, “We’re only halfway through 2016, and our analysis shows numbers of vulnerabilities surpassing 2015 rates. But at the same time, there are less exploits across the board with the exception of Flash, which continues to have high ROI for hackers. Security is improving, but old attack techniques like phishing and watering hole attacks are still plaguing enterprises. It goes without question that we can expect attackers to evolve in response to heightened security. We need isolation and instant protection to secure our networks and data.”
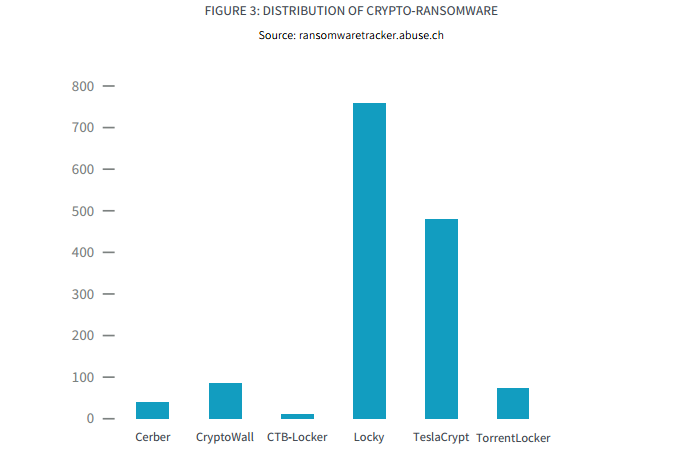
Though the dangers are becoming more sophisticated and insidious, Kashyap believes real efforts are being made to secure networks and IT infrastructure. “As an industry, we’ve always said there’s no one silver bullet to address the complexities of attacks that are affecting our business. However, our latest research shows that enterprises and vendors alike are stepping up to do a better at securing their networks and data. But there’s still work to be done.” It’s expected that over the next 12 months social engineering tactics will continually be exploited by attackers, and “instant protection, detection, and remediation is more critical than ever.”
Bromium Labs finds most AV vendors are executing multiple updates per day in an attempt to keep up with machine timescale attacks but with new Malware observable for less than 60 seconds before it transforms into a victim-specific variant current malicious detection capabilities are found to be lacking. It’s suggested the best strategy is a dramatic reduction of the attack surface, isolating attacks and limiting possible danger and spread. Taking a new approach, Bromium’s unique micro-visualization technology is advancing endpoint security and their solution automatically isolates each user-task in a lightweight, CPU-enforced micro-VM. For all of Bromium Labs security insights and judgements, download the full Bromium Lab Threats Report.
By Jennifer Klostermann





