Last year was a big year for the cloud. Cloud adoption continued to grow at a rapid clip, even as executives from companies such as McDonald’s and ENEL talked about how their organizations are embracing a cloud-first approach to IT with an eye toward a cloud-only future. It was also a year of transition, as the customer base for AWS shifted toward large enterprises running their mission-critical workloads in the cloud.
As we experience firsthand many of these enterprises’ transitions into the public cloud, I share my views on where things are headed. Rather than writing about futuristic predictions about what to expect in 2017, I’m sharing my observations about broad sweeping trends that will continue to shape the direction of cloud security in the years to come.
The major cloud providers such as Amazon Web Services (AWS) and Microsoft Azure have invested heavily in their platforms’ security over the past few years to address customer concerns and earn their trust. The first wave of investment focused on foundational security and governance capabilities to enhance platform visibility, with features such as AWS CloudTrail and VPC flow logs as well as control capabilities such as Identity and Access Management (IAM).
Building on this firm foundation, the cloud providers (mostly AWS) are now turning to advanced security technologies. These technologies, which until recently were offered as dedicated products and services by third-party vendors, are now seamlessly assimilated into the cloud platform as integral features.
This disruption has already happened to a number of products in very focused, IP-heavy areas. A few examples:
We have seen this trend of standalone products becoming features of the underlying platform play out several times before. For example, technologies such as storage compression and WAN optimization were first introduced into the market as standalone products, but over time became features of the underlying storage and networking platforms. This integration of technologies is great for cloud consumers who will enjoy more integrated and affordable security services, but spells bad news for legacy security vendors who will find themselves being marginalized or directed into more focused niche markets.
Cloud consumers have always understood the value proposition of a multi-cloud strategy in principle. But for many years, multi-cloud was just a fluffy buzzword with low correlation to reality. The complexity and pain associated with managing different cloud environments was just too high compared to the benefits. There was also lack of parity between different cloud services in terms of technological capabilities.
In recent years, multi-cloud environments are starting to become more common, either as a deliberate strategic decision by enterprises, or because of acquisitions, leadership changes, etc. So what’s changed to make multi-cloud environments more feasible?
IT governance and compliance management used to be a point-in-time process that companies engaged in periodically (once a quarter, once a year, etc.), but is now transitioning into a continuous process. The forces for this change come from the ‘demand’ side, i.e. the need as well as the ‘supply’ side, i.e. technological feasibility. On the demand side we can see the dynamic, elastic nature of new cloud environment, turbocharged by devops and continuous delivery (CD) practices. The new reality that your core production systems are now in the cloud and being deployed multiple times a day is a real change from the past. On the supply side we can see the technological enhancements that makes continuous security, governance and compliance a reality:
To get a sense of future trends, take a look at how AWS is educating the industry. Here’s the list of the security sessions from last re:Invent:
Yes, almost 40% of the sessions had some sort of ‘automation’ in their title!
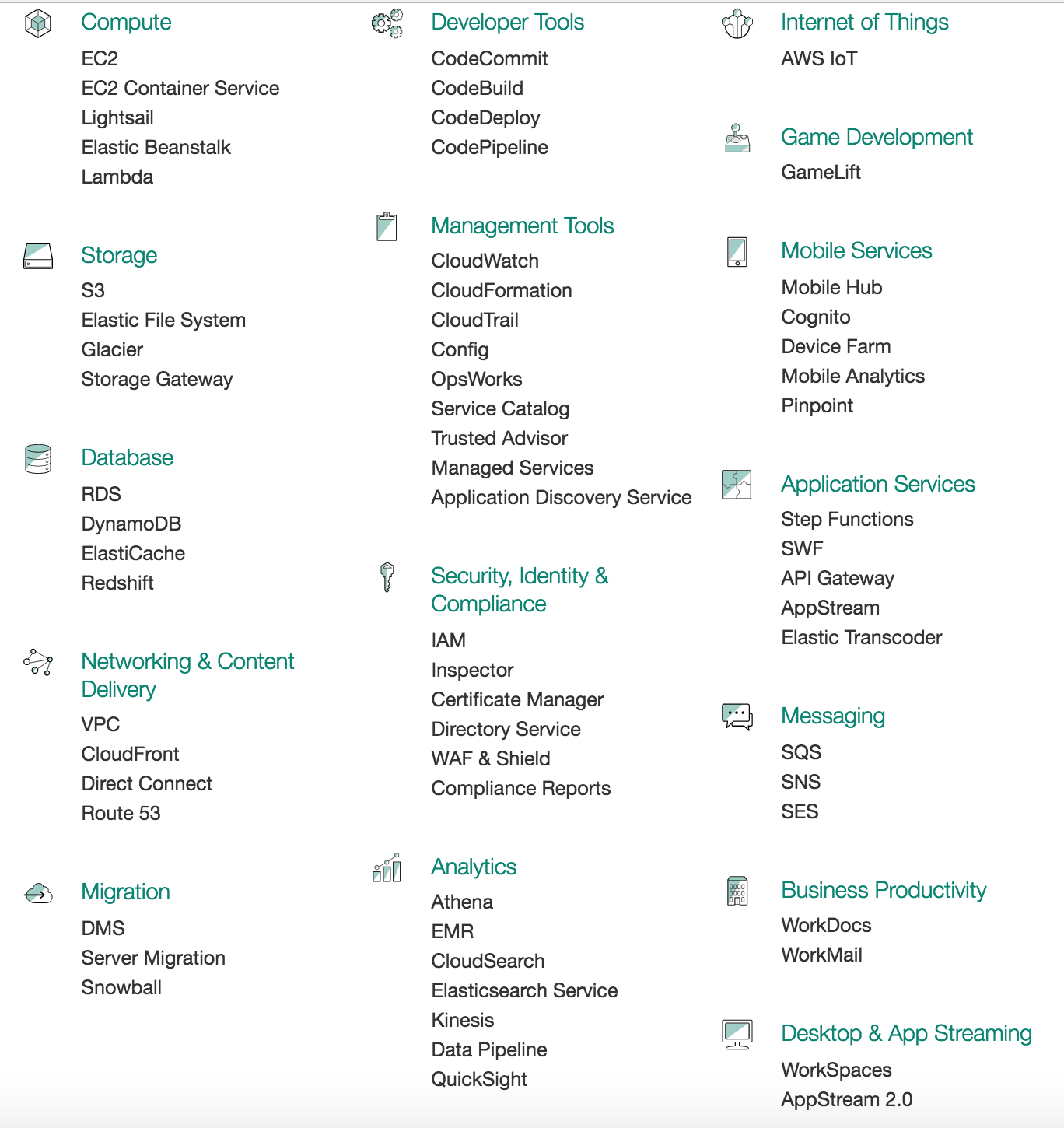
The cloud of 2016 is very different from the cloud of 2006. Public IaaS clouds started out with just compute (virtual machines) and storage services, but now provide dozens of services. The line between IaaS and PaaS is blurring rapidly.
This means that a modern cloud datacenter does not look like an On-Premises deployment. Instead, a typical application has a hybrid architecture that includes traditional virtual machines or instances as well as hosted, managed services such as databases, data warehouses, load-balancers, Lambda / FaaS and so on. Let’s compare 2006-style cloud deployment with a 2016-style deployment.
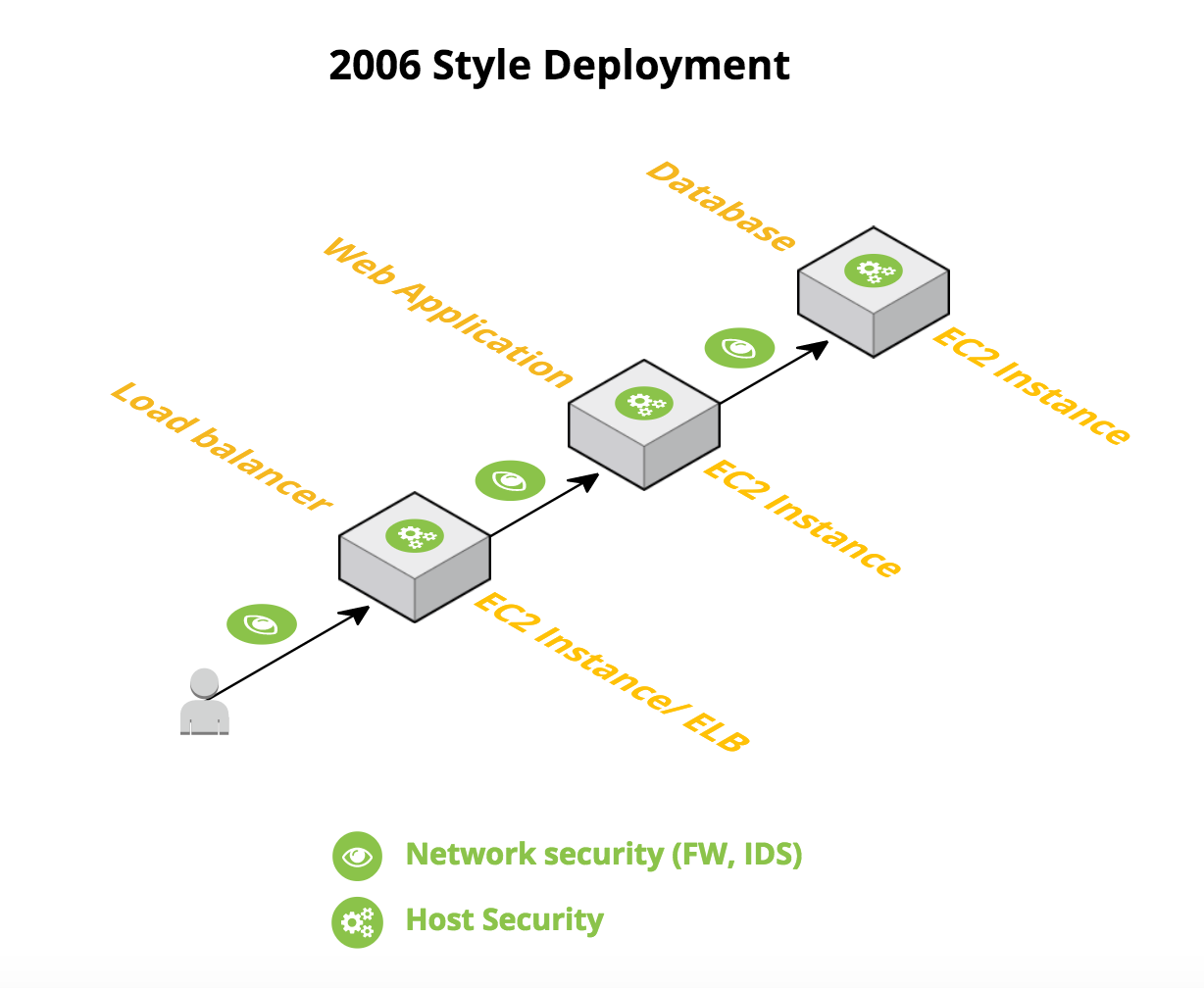
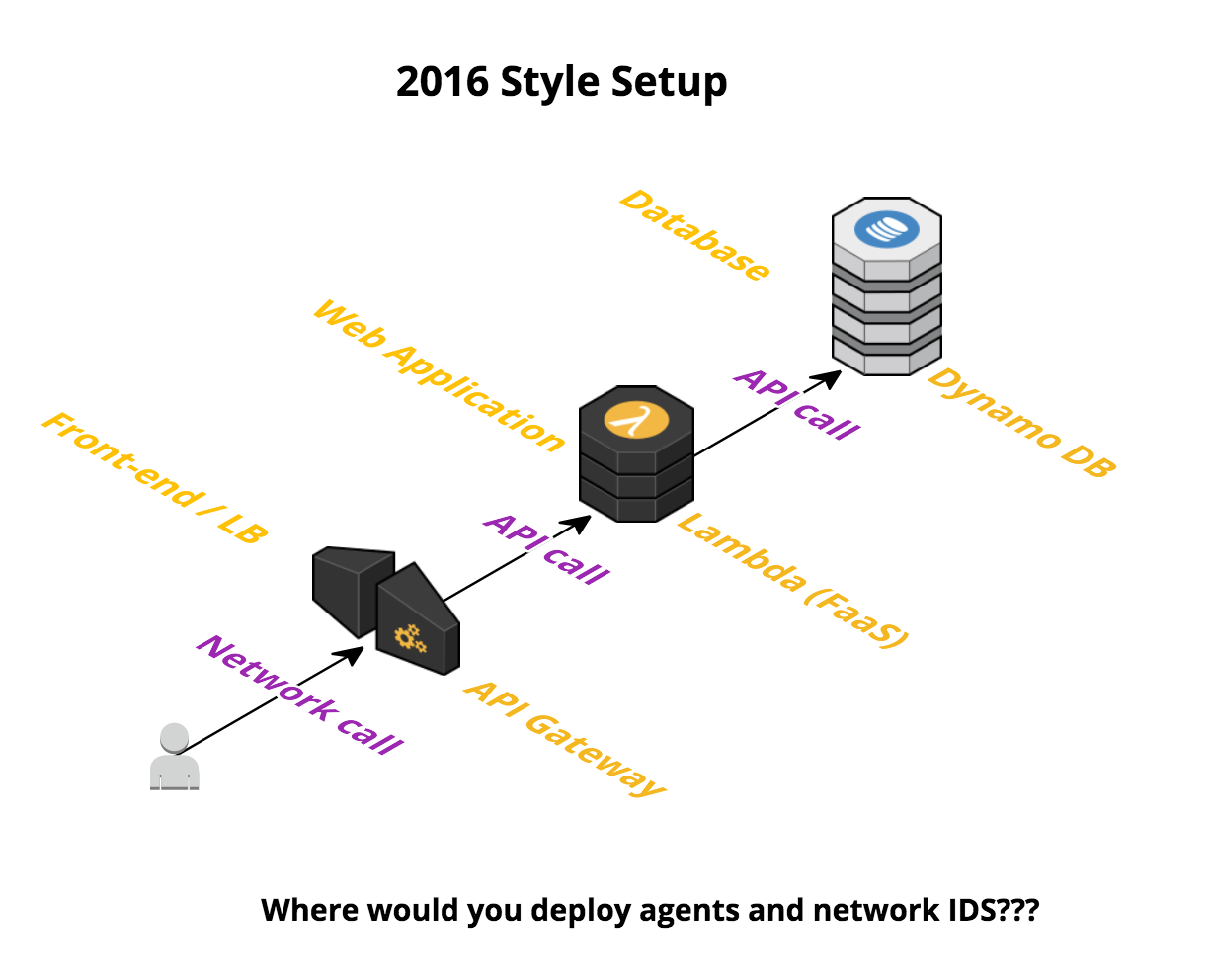
In the 2016 deployment, operations teams have only limited control over many of the building blocks of the application. From a security point of view, legacy network and host security tools are just not enough. For example, where would you install a security agent in a Lambda function? How do you get network visibility to the traffic between an API Gateway and a Lambda (serverless) backend?
To truly manage security in this brave new world, administrators need to complement network security with robust IAM management. IAM and cloud-native settings are becoming the logical glue and the main security policy to drive new cloud deployments. What is needed is a holistic approach to control, monitor, protect and govern in the cloud, which includes cloud configurations, IAM policies, cloud events and audit trails as well as traditional network and host-based security.
We are expecting to see this trend translated into cloud consumers’ practices (possibly breaking some internal silos) as well as to cloud-native security products.
By Roy Feintuch, Co-Founder / CTO, Dome9





