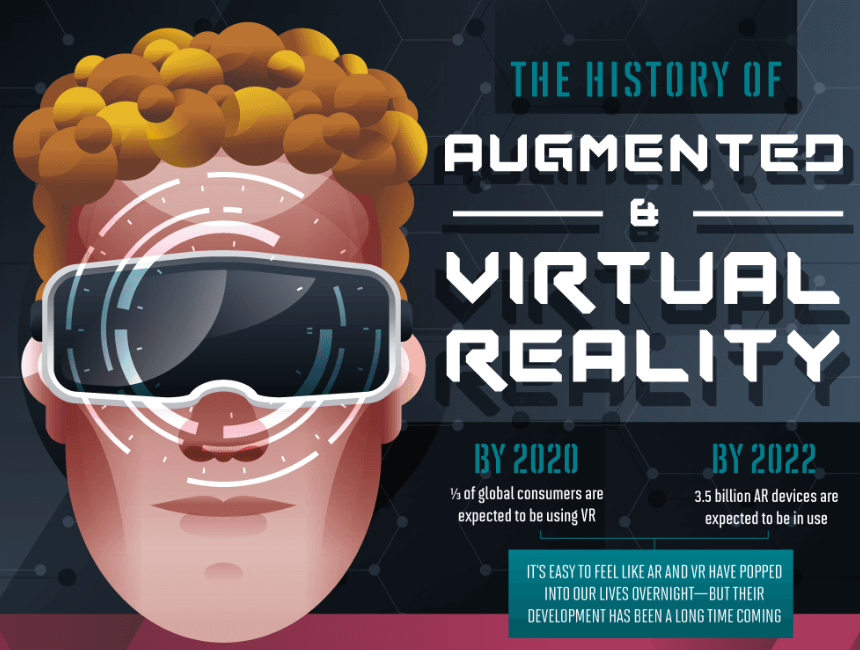
Ways in Which AI is Changing Marketing Strategies for Businesses
AI Is Changing Marketing Strategies Artificial intelligence is computerized intelligence that simulates human behavior through computer apps, software and through other channels. These apps include the Facebook share dialog that [...]