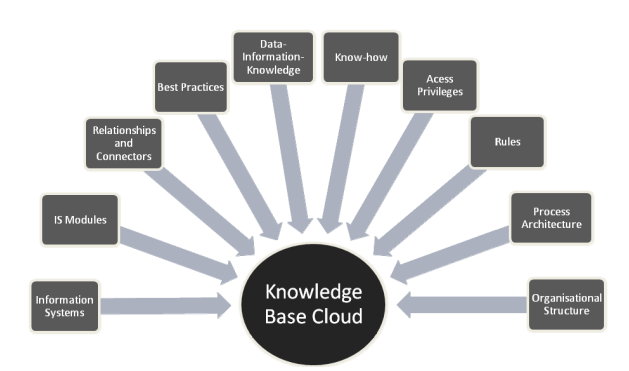
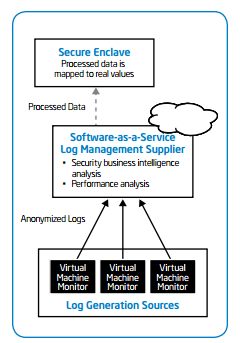
Transforming Raw Data Into Meaningful Useful Information
Transforming Raw Data Advanced multimedia devices, social media services, sensor networks, and corporate information systems create continuously huge amounts of structured and unstructured data which are called big data. Transforming [...]