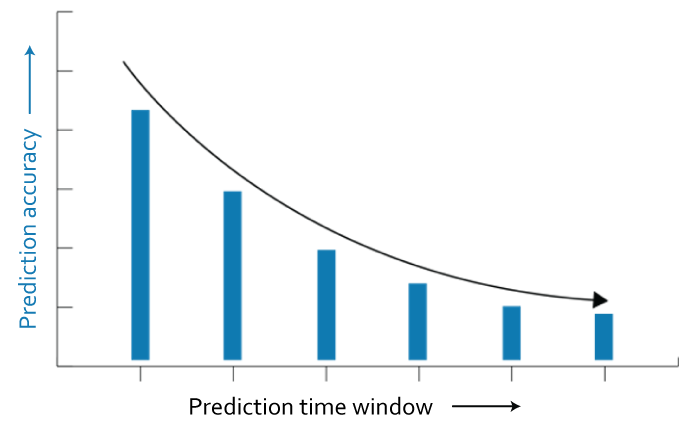
Addressing Third-Party Security Vulnerabilities
Third-Party Security Vulnerabilities Organizations and businesses often spend a lot of time worrying about internal security, both online and off. Infrastructure is often put in place with security front and [...]