Connecting Smart Homes with the Internet of Things
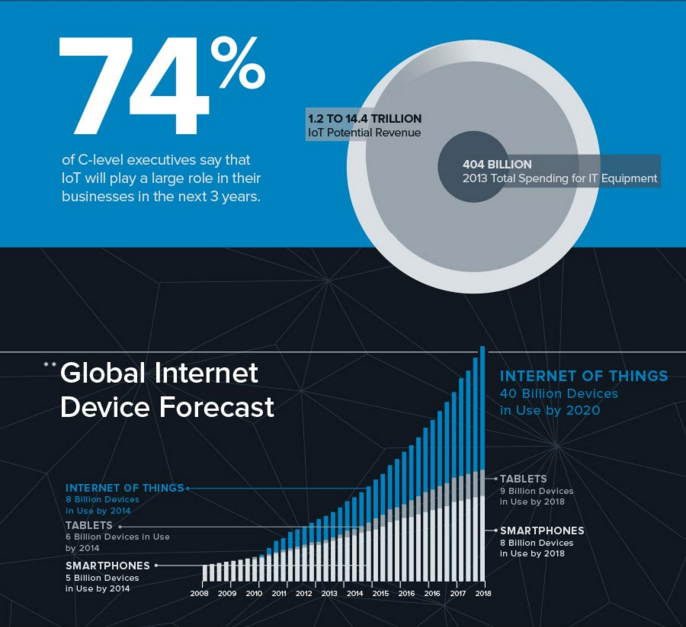
Internet of Things Wikipedia defines Internet of Things, as “the internetworking of physical devices, buildings, and other items embedded with electronics, software, sensors, actuators and network connectivity that enable these [...]