Savision’s Version 7.5 of Live Maps Unity
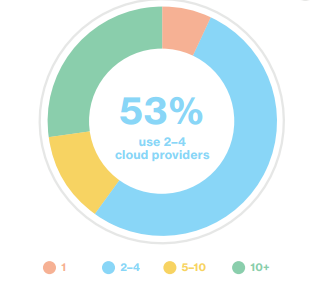
Live Maps Unity Declared the number one Microsoft System Center, VMware and Hyper-V ISV Partner in the world, Savision’s key solution Live Maps Unity monitors organizations’ performance and service health, [...]