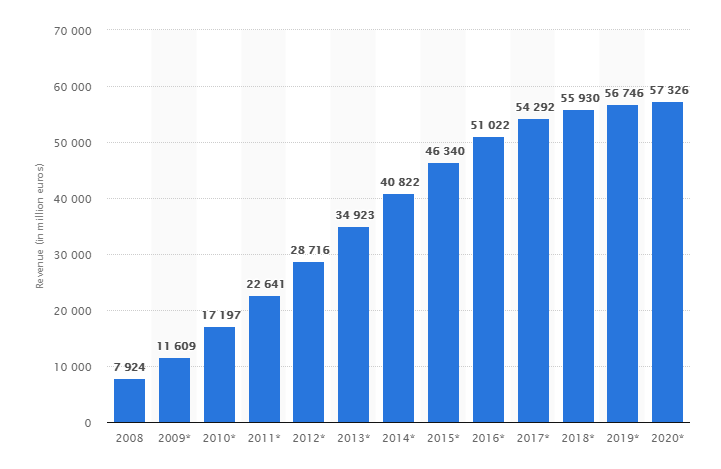
The Importance of Open Source Security
Open Source Vulnerabilities Open source software is rapidly gaining popularity with 93 percent of organizations using open source software and 78 percent performing all or part of their business operations [...]











