Cloud Computing and CRM
Cloud computing is the techno-business strategy of web-based access of diverse set of applications from any device and less workload on the Customer Service Representative’s (CSR) device as the software and data gets stored elsewhere. Any kind of application can be accessed through cloud, right from trivial word processing software to complex analytical engine for an enterprise. The primary benefit of cloud platform is that it allows an organization to focus only on its core competency as the complexity and overhead of managing IT applications and infrastructure will be addressed by the cloud platform vendor. Cloud based CRM enables organizations to manage customer experience via cloud in a flexible and cost effective manner. Salesforce.com, Microsoft and Oracle are major cloud based CRM vendors.
Benefits of Cloud CRM
There are a number of benefits of a cloud based CRM than an on-premise model, especially in terms of mobility, flexibility and cost.
Cloud Security and Availability:
Though many small and medium sized companies have started to adopt cloud based CRM strategy to benefit from low cost upfront and quicker implementation cycle, many large companies are still skeptical about migration to cloud due to storing sensitive data like customer details and commercial transactions in a remote database. Security concerns and fear of sudden outage are the major deterrents for cloud adoption, especially in CRM space where customer experience and trust are of prime importance. Some also ponder about migrating to private or hybrid cloud; however these alternatives are complex, tedious and costly when compared to public cloud. Consequently, the migration to cloud based CRM platform has been slow compared to the hype and expectation. According to an expert from Gartner “Despite the hype surrounding migration to the cloud, big differences in movement rates continue, depending on organisations’ size, industry, geography and specific requirements.”
The thought of storing strategic documents, customer data and commercials elsewhere cause cold feet for many CXOs while transforming to cloud. Furthermore, an outage could make data unavailable at the time of serving a customer request, performing transactions and also decision making.
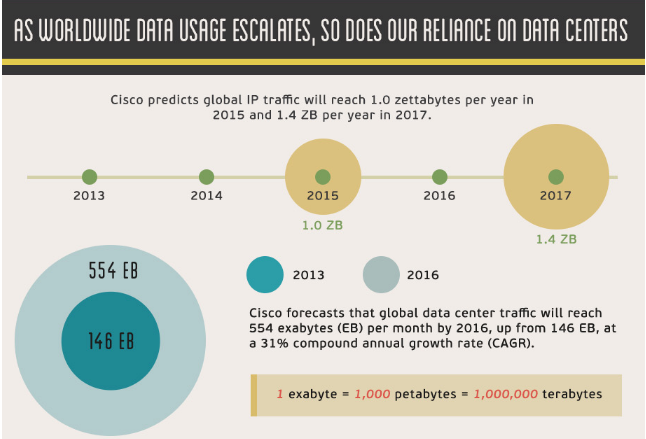
The following are the major implications for an organization in case of security breach or outage.
It is apparent that, securing the cloud platform is fundamental to eliminate the inherent risks and gain from the investments made. Through various hybrid cloud architectures are available, they tend to become costly and complex, when compared with simple cloud implementation. Understanding the process of providing a secured platform and greater collaboration within cloud vendor and organizations is the key to create a successful cloud based CRM and win customers’ trust.
Below are the possible avenues through which security can be enhanced for a Cloud based CRM system.
Monitor Vulnerability:
The key to a successful security strategy is to rigorously monitor all events and activities in the cloud ecosystem. Added, an enterprise can assign an internal security team to perform extensive penetration testing to identify Vulnerabilities, and share the “findings” with the cloud vendor. The effectiveness of the monitoring strategy should be revisited frequently both by the cloud vendor and implementing enterprises.
Deceive by Traps:
The CRM vendors can create certain “security traps” within their datacenters and cloud ecosystem. These purpose-built traps will certainly lure the probable hackers during their preliminary attempts. When anticipated security incidents happen, it could trigger an alarm for the IT security personnel to look into. Such alarms can alert both in-house security team at the enterprise and also the security team of the vendors. Later, appropriate defensive methods can be initiated to prevent the breach further and to identify the location the hackers as well.
Maintain Transparency:
The vendors can share all the relevant logs (security, audit, etc.) with the organizations on a regular basis. Also, they can educate the enterprises regarding new vulnerabilities identified and precautionary measures. Transparent and consistent approach could ensure increase in confidence and trust, especially from skeptical organizations.
Know Your Customers
The cloud CRM vendors can provide a “profiling feature” to enterprises to secure the “customer portal” used by end-users. The enterprises use the feature to perform appropriate profiling of their customers with regards to security. For example, request for references and recognized identity proofs can act as a layer of security. This will certainly deter unscrupulous elements from gaining access to CRM portal by faking as customers.
Know Your Employees:
It is an accepted fact that even employees inherent to an organization can perform security breach. The cloud vendors can provide a “predictive reporting” feature by consistently monitoring the activities of all employees. The reporting feature should maintain the activity history of an employee and automatically trigger a report to the in-house security team on any change in employee behavior with the system. For example, login failure, trying access to restricted site, etc. This will enable the security team to predict probable unwanted behavior from employees.
In summary, the above mentioned approaches will definitely help enterprises achieve greater security. Focus on each step at a time and greater collaboration with cloud vendors, will help organizations achieve higher levels of security, enhanced customer experience through better reliability and maximize benefits from cloud based CRM systems.
By Padmanabha Sivanandan





