Much of the enthusiasm and discussion about cloud technology focuses on its dynamic and innovative structure, and with each passing day a new technique or resource bursts onto the scene with promises of greater functionality and speed for all. But this causes great trepidation and reluctance among those charged with ensuring safe and secure environments, especially in highly regulated industries such as financial services. Banks, credit card companies and other financial institutions are teased by the promise of lower operating costs and dynamic scalability, and of course are painfully aware that their clients, suppliers and competitors are quickly adopting this new approach, leaving them to look like dinosaurs in the process.
The problem lays not so much in the resistance to change but instead in a lack of complete and cohesive guidelines from regional or local authorities to counteract the ever-present compliance and security issues.
Gartland & Mellina Group (GMG), a strategic management consulting firm based in New York and with clients worldwide, is now seeking to assist in resolving this conundrum with the release of its white paper, entitled Navigating Through the Cloud in Financial Services, one of four papers that comprise its new Thought Leadership Series on Technology Adoption in Financial Services.
Starting with a statement (supported by data) that shows just how much financial services are lagging behind in cloud adoption, it then highlights the clear fact that “financial services firms must navigate a range of deployment & service models that vary in the level of cloud ownership responsibilities and security control.”
One specific area that the GMG white paper focuses on is that of compliance, which they identify as a “double-edged sword in the financial services industry.” This is due to regulatory requirements under Dodd Frank regulation that require securities firms “to hold significantly more data for reporting mandates, which compounds the compliance risk derived from the data privacy and control demands imposed under the Gramm–Leach–Bliley and the Sarbanes–Oxley Acts.” This means that cloud migration will increase reporting demands.
Added to this is the fact that authorities such as the Federal Reserve and SEC have not yet firmed up their position on cloud data migration, leaving little in the way of standards and guidance.
The paper points out that the industry is not without is sources for policies and procedures, in fact there are quite a number of authorities that financial institutions must deal with. The Federal Financial Institutions Examination Council (FFIEC), for example, released a joint statement by the FDIC and the Federal Reserve and others, which provides guidelines for cloud migration strategy, while payment card information will be guided by the Payment Card Industry Data Security Standard (PCIDSS), which identifies additional requirements for joint responsibility between CSPs and their clients.
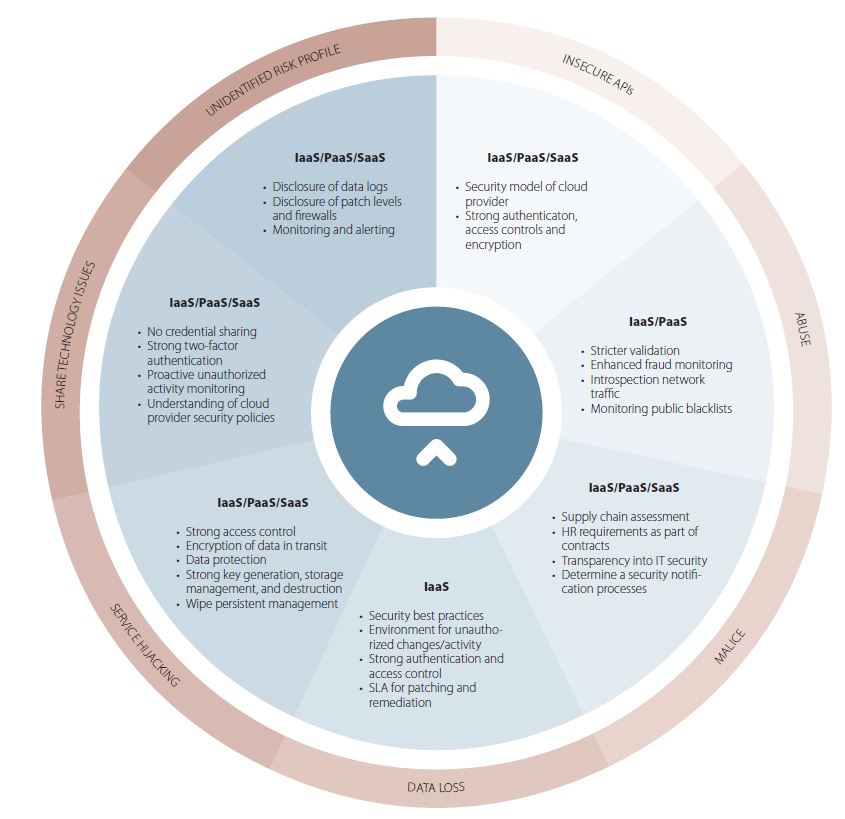
Issues dealing with geography and international commerce are highlighted in the paper, as well as the numerous types of threats and attacks that a cloud-based system must withstand.
Far from being a gloom and doom scenario, the GMG white paper presents a number of viable options and opportunities for financial institutions and their IT specialists to consider when contemplating a move to the cloud.
Robert Rowland, Director in GMG’s Financial Services Strategy and Solutions Practice states, “Due to regulations, security concerns and consolidation, the financial industry is faced with challenges in advancing their technology solutions. We understand that taking that step forward isn’t easy. But we wanted to provide firms with practical insights that would not only compel them to modernize their business practices, but that would also help them approach it in an effective way from a business perspective. Considering these insights will not only benefit their bottom line, but also increase the value they add for their clients.”
By Steve Prentice





