Nowadays, many companies are changing their overall information technology strategies to embrace cloud computing in order to open up business opportunities. There are numerous definitions of cloud computing. Simply speaking, the term “cloud computing” comes from network diagrams in which cloud shapes are used to describe certain types of networks. All the computing of more than one computer via a network or the service gained from the host computer via a network is considered cloud computing. Through different types of devices such as PCs, smart phones users can access to services and computing resources in clouds. According to the National Institute of Standards and Technology (NIST), ‘‘Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction’’. Cloud computing represents a convergence of two major trends (IT efficiency and business agility) in information technology. The term IT efficiency refers to using computing resources more efficiently through highly scalable hardware and software resources. Furthermore, the business agility is the ability of a business to use computational tools rapidly, to adapt quickly and cost efficiency in response to changes in the business environment. Cloud computing can remove traditional boundaries between businesses, make the whole organization more business agile and responsive, help enterprises to scale their services, enhance industrial competitiveness, reduce the operational costs and the total cost of computing, and decreases energy consumption. It would seem that cloud computing can provide new opportunities for innovation by allowing companies to focus on business rather than be stifled by changes in technology.
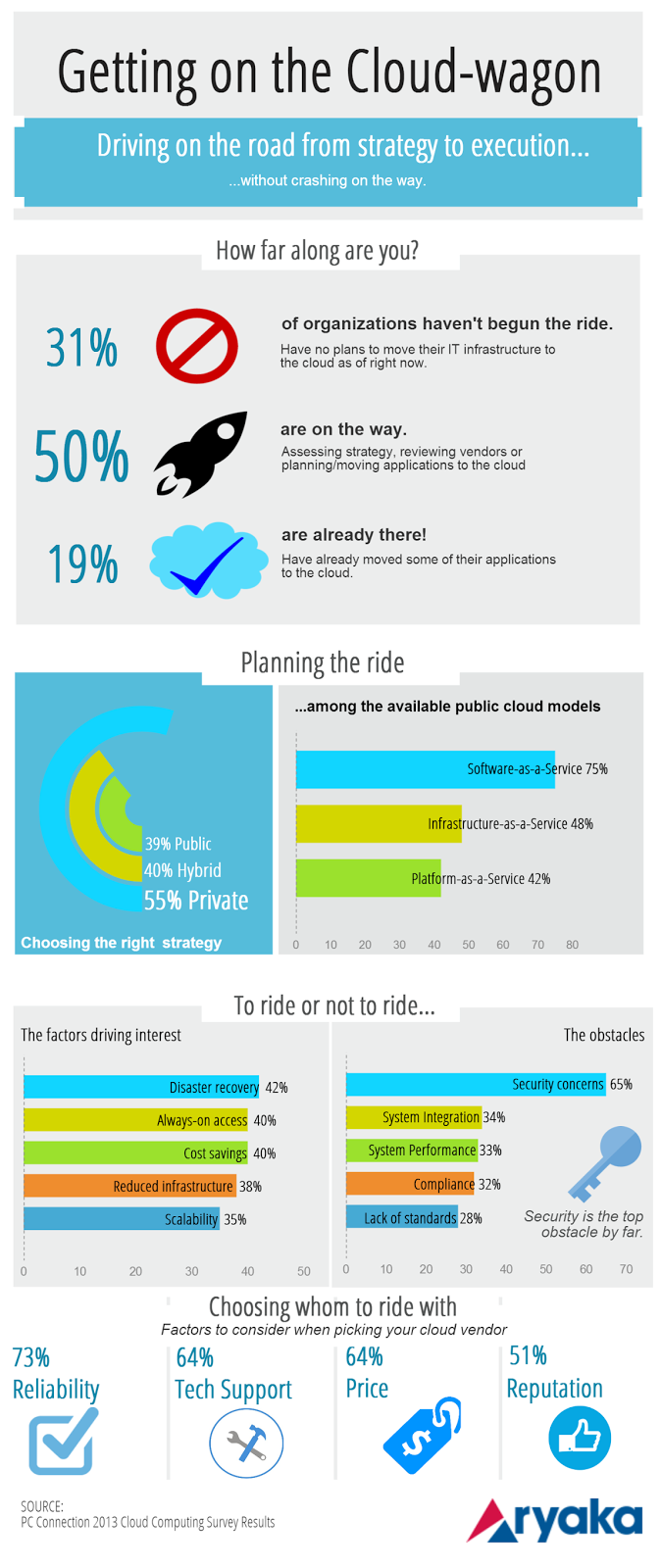
Although this new technology can help organizations to achieve business efficiencies, evidence indicates that not all companies intend to adopt cloud-based solutions. Borgman and his colleagues conducted a study on the factors influencing cloud computing adoption and found that the security and privacy, identity management standards, and the need for sharing and collaboration in today’s highly competitive world have a positive effect on using and adopting the cloud computing. In fact, a data breach is a security incident in which a company or a government agency loses sensitive, protected or confidential data. Cloud computing involves storing data and computing in a shared multi-user environment, which increases security concerns. Privacy-enhancing techniques, monitoring mechanisms, authentication, encryption, and the security of data in the cloud environment are good ways to enhance cloud security and minimize risk.
Many scholars suggested several strategies to help decision makers improve cloud security which are as follows:
1. Ensure effective governance, risk and compliance processes exist
2. Audit operational and business processes
3. Manage people, roles and identities
4. Ensure proper protection of data and information
5. Enforce privacy policies
6. Assess the security provisions for cloud applications
7. Ensure cloud networks and connections are secure
In sum, cloud computing has become ubiquitous in recent years. Studies indicated that factors such as the relative advantage of cloud computing (such as improving the quality of business operations, performing tasks more quickly, increasing productivity, cost savings, and providing new business opportunities), ease of use and convenience in using the cloud infrastructure, privacy and security, and the reliability of cloud providers can affect the adoption of cloud computing. Hence, decision makers should systematically evaluate these factors before adoption of cloud computing environment.
By Mojgan Afshari





