Cloud computing is a new model for managing and delivering services over the internet. It consists of a series of hardware and software resources made available on the Internet. Users can access, process, share, and store information through the Internet anytime and anywhere from any digital device. Cloud computing is flexible, highly scalable and creates virtualized resources that users can access all these resources without any specialized knowledge about the concept of cloud computing.
Cloud computing has a significant impact on teaching and learning environment. It is highly practical in education for both students and teachers. The cloud based environment supports the creation of new generation of e-learning systems. E-learning (web-based learning system) is an Internet-based learning process using internet technology to design, implement, select, manage, support, and extend learning, which will not replace traditional education method, but will greatly improve the efficiency of education.” In fact, using web-based learning system has revolutionized educational organizations and has affected teaching and learning contexts in universities and educational institutions all over the world. In traditional web-based learning model, educational institutions invest a huge amount of money on hardware and software applications, infrastructure, maintenance and the appropriate training of staff to enable them to use technology effectively. However, in cloud based e-learning model, educational institutions without any infrastructure investments can get powerful software with lower or no up-front costs and fewer management headaches in the classroom. The development of e-Learning services within the cloud computing environment enables users to access diverse software applications, share data, collaborate more easily, and keep their data safely in the infrastructure. Moreover, it can lower expenses, reduce energy consumption, and help organizations with limited IT resources to deploy and maintain needed software in a timely manner.
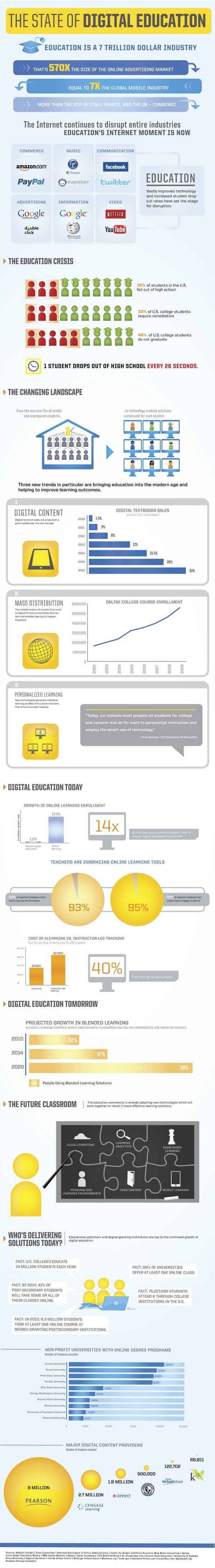
Nowadays, some educational institutions provide private cloud services for their staff and students as well as external people for collaboration purposes. They can access various applications, services, and tools wherever and whenever they want. Students and teachers can conduct formal lessons even without a standard indoor classroom because cloud services allow them to share their information with anyone, anywhere, and at any time. Hence, learner-staff and learner-learner interactions as well as the learning experiences of both learners and staff will be enhanced. Therefore, cloud based-learning can be an efficient and effective system to help students obtain the 21st century skills and prepare them to succeed in the global information society.
Shifting e-learning in the cloud creates new security challenges. Main security concerns are about confidentiality, integrity and availability. Microsoft has provided instructions for IT managers to enhance the security in cloud based e-learning.
They are as follows:
By Mojgan Afshari





