Every December, security experts begin to release their predictions on what future cybersecurity challenges will look like in the coming year.
“The concept behind predictions is based on a company’s ability to express its expertise in a field both on the business and on the technology end,” said Barry Shteiman, director of security strategy with Imperva. “We used our experience and our intelligence and data analysis systems as well as ongoing research in our fields in order to understand what hackers are doing, the shifts and trends as well. Based on that, we have been able to predict time and again how the security space will shape itself towards the upcoming year.”
In a perfect world, CISOs could use predictions of companies that have hit the spot consistently – to shape their own security strategy going forward, Shteiman added. Not only in spending and budgeting, but also in overall mindset of how the business should behave and what threats to look for.
“For example, last year we predicted that 3rd party components will become one of the biggest security problems for companies in 2014,” he said, “and in fact many of the breaches that occurred and many of the critical Vulnerabilities that were discovered (Shellshock, Heartbleed, etc..) demonstrated the need to compensate with security controls where 3rd party components are being used. I believe that companies that took action based on that prediction were safer.”
In 2014, cybersecurity challenges included breaches of some of the world’s largest retailers and financial institutions, vulnerabilities found in old open source codes, security breakdowns in Apple software, and malware targeting Android devices.
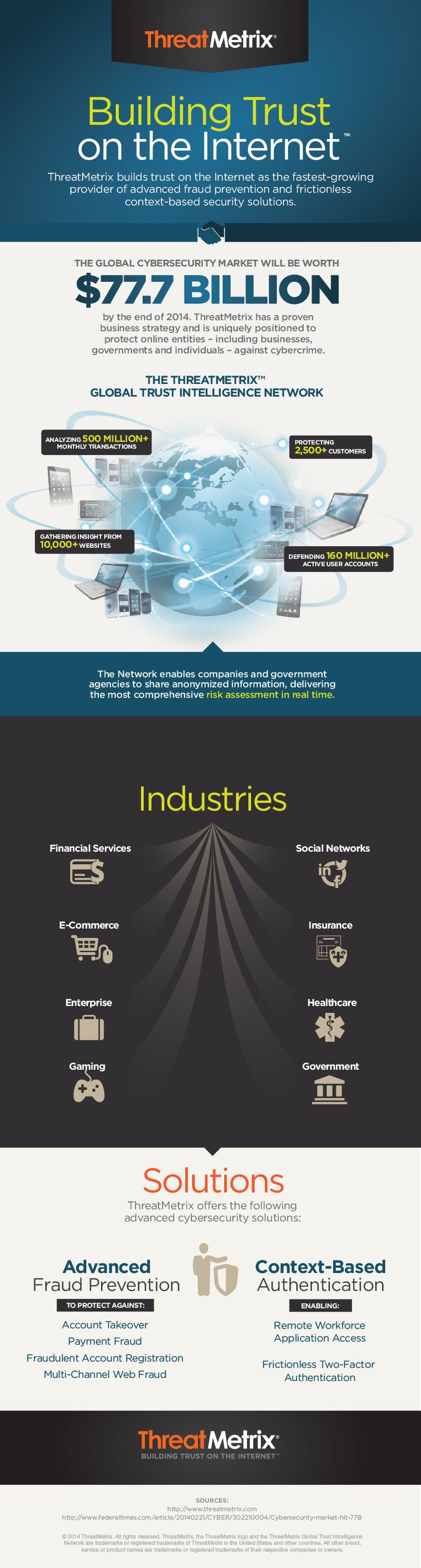
(Infographic Source: TreatMatrix.com)
Smarter Malware
Expect malware to become more evasive and use tactics that haven’t been seen before. The Destover malware used in the Sony attacks is one example of this. Also, according to researchers from Top Ten Reviews anti-malware team, expect more malware that uses novel techniques that enable it to evade automated dynamic analysis systems (AKA sandboxes). Malware creators have learned to exploit subtle user actions and environment-specific criteria that can reveal actual malware location (on a real machine as opposed to in a sandbox), or to use “delayed detonation” that takes advantage of sandbox timeout limitations.
Expect High-Profile Attacks to Continue
The LightCyber researchers also expect to see a 2014 trend continue into the new year: Well-known companies will be targeted by cybercriminals. One shift we may see, however, is big-box retailers won’t be grabbing the headlines. Expect to see attacks on corporations in other industries such as financial, healthcare, defense, and media. But at the same time, small businesses should not be lulled by these high-profile attacks. Cybercriminals will go after any company that has valuable information, no matter how large or small.
New Payment Options May Not Be as Secure as Advertised
Mobile wallets and payment options like Apple Pay are being touted as the “secure” way to pay without using cash. But we shouldn’t get lulled into thinking they are totally safe. One mobile payment option, CurrentC, has already been hacked, and, said Chris Petersen, CTO and co-founder of LogRhythm, Apple’s cloud security problems could make things very interesting.
Things Are Going to Get Worse before They Get Better
Despite the almost weekly “Famous Company Suffers Data Breach” stories and the rising number of IT professionals reporting their company had also dealt with a cyberattack, businesses and consumers alike continue to be complacent about good security practices. They’ve let things slide, didn’t keep up with the times, and invested their time and attention in other pursuits. “The result is that uncountable thousands of organizations are frighteningly vulnerable to having their systems hacked and their data stolen,” said Benjamin Caudill, Founder and Principle Consultant at Rhino Security Labs. “Many of them don’t realize it yet, but the cyber-crime community is starting to. This means that we’ll probably see an acceleration of the same trends we saw in 2014: more breaches, bigger breaches, and the ever-wider reach of cybercriminal activity.”
But Security Budgets Will Grow
There is some optimism, though. Security budgets are expected to increase in 2015, and that will include upgrades to the security infrastructure. Businesses will invest more in cloud security options, according to an IBM report. LogRhythm’s Petersen added that companies will also invest more in cybersecurity insurance.
By Jeremy Page





