Record Year For Data Breaches
The news is full of data security breaches. This week, Sputnik International reported that Hacking Team had a 400 GB database stolen and published, and last month Ars Technica discussed in detail the information breach at the U.S. Government’s office of Personnel Management. MSPmentor‘s current IT security news includes the hacking of databases at Harvard, a data breach discovered at Orlando Health, and 85,000 compromised debit and credit cards during the FireKeepers Casino data breach. Non-profit identity theft organization ITRC reported 400 data breaches this year as of June 30 and believes 2015 could top the charts for data violations.
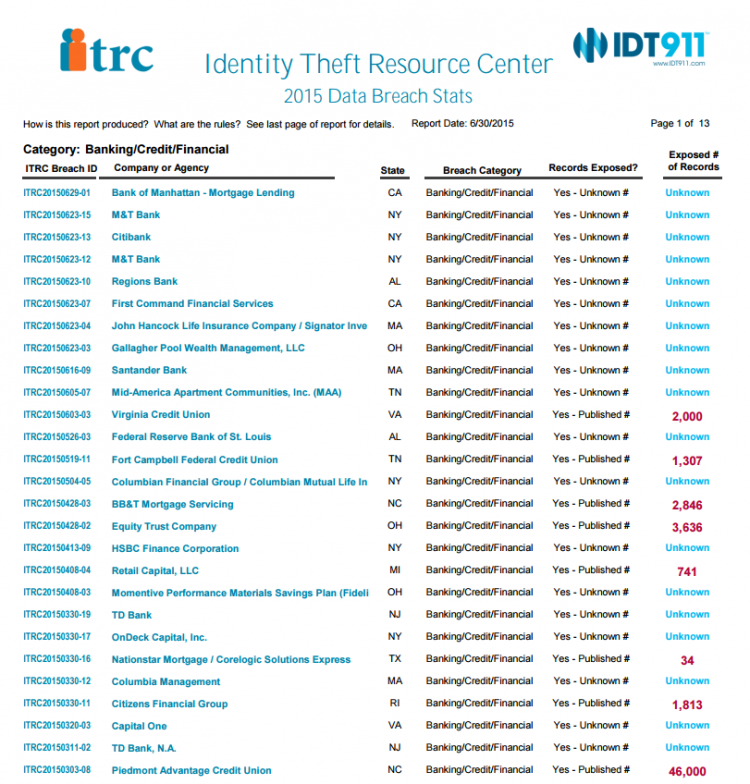
See The Full Report
As if you didn’t have more important things to worry about – so here’s a quick look at how to stay ahead.
The Risks
- Access control and authentication: are you certain only the necessary people have access to relevant data at all times?
- Terms and conditions: are the standards of your Service Providers equal to those your organization maintains? And how secure are your own standards?
- Virtualization technology: what are the security guarantees? How accessible are the services offered?
- Data privacy: strict security measures need to be in place ensuring responsible data management, and industry and regulation compliance.
Security Strategies
- Transparency: choose service providers that adhere to industry standards, provide clear service and product details, and have open lines of communication.
- Drills: be sure to test for possible security holes, and plan for breaches. Just as you would prepare for physical risks such as fires, put emergency tests and procedures in place to counter data threats.
- Backup: always have a backup. Do it now.
- Diversify: minimize your risk by spreading data over localized and cloud servers; scatter service provider usage where possible.
- Education: train yourself and your employees on security threats and defenses. Try to be proactive and keep up with the constantly-evolving environment.
- Data tracking: understanding data-centric security tools helps maintain sensitive data and ensures you’re the first to know should something go wrong.
- Policies in place: governance policies are essential and should be clearly established to safeguard data privacy. Data sensitivity classification helps apply the correct security techniques to relevant data sets.
- Encryption: never store encryption keys in the software or with your data, and be certain that strong encryption techniques are being used. Always remember that data being used is also vulnerable, so take steps to ensure secure handling.
By Jennifer Klostermann






