The majority of cloud consumers don’t understand what cloud is let alone what the implications of transacting in the cloud or of having their data and digital assets stored in the cloud. As a result most consumers are their own worst enemy when it comes to putting themselves at risk in the cloud. The ramifications of not understanding the risks can result in anything from consumer data exposure or loss of digital assets, to online reputation damage or worse still, incurring the same for their children. The good news is with a few tweaks consumers can better protect themselves.
Most explanations of cloud are geared at technical business users and very few are aimed at consumers. In fact, Katie Couric’s very recent The Cloud Explained is one of the very few pieces that I have seen that describes cloud in its simplest incarnation as a network of computers and in a way that most non-tech, savvy consumers can easily digest. I strongly encourage consumers to find a starting point on the web that they can easily digest and over time to gain as much knowledge as they can of the cloud services they use.
Cloud is something that become an increasing part of our reality and may have sprawled into a number of different, though very useful services. In fact, we have reached the inflection point where it would be difficult to opt out of having some aspect of one’s life in the cloud. Some consumers may have been initially conscripted into a cloud service without their explicit consent. It may have happened, for example, as their utility company moved its infrastructure to the cloud, or through their doctor’s office now using online appointment settings or through their mobile phone synching settings, even for those who may not necessarily opt to have their information backed up to the cloud. Then there are those who have opted to use cloud storage services knowingly. It may have started with backing mobile phone or computer storage settings to the cloud for assets like songs, photos, videos and documents or even using online applications and sharing tools such as Facebook. However, consumers started out in the cloud it’s probably a good time to mentally audit their cloud services to understand which services are storing, transacting or have access to their data or other digital assets.
The proliferation of cloud services has resulted in many cloud providers, especially storage providers who have differentiated their services on security. For those using cloud services to store photos, documents and other personal assets there are providers who offer encryption services or those that allow for a layer of encryption to be easily added. Such a layer of security could protect against personal digital assets being hacked into or even accessed accidentally by others.
Many consumers find managing passwords a nightmare and despite the well publicized dangers associated with using “password” or sequences of letters and numbers, too many consumers often resort to just that. Consumers need to find something that is memorable to them that others would find extremely difficult to guess. A password phrase like “IstartedskatingwhenIwas15” might be difficult for both friends and hackers to guess but personal enough for the consumer to remember. Consumers also often don’t understand the risks of sharing passwords with family and friends but they need to treat their passwords as a penultimate secret. It is careless password management or lack of a strong password that create the biggest vector for hackers looking for credit card data or other sensitive personal information.
Where possible consumers should also connect using two-factor authentication to cloud services.
Included is an image provided by https://twofactorauth.org which offers a nice list of sites currently offering 2FA.
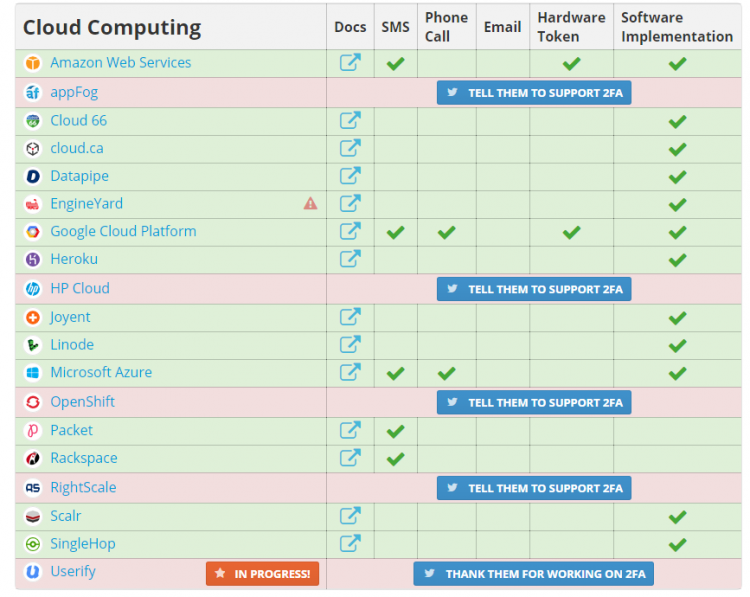
Two-factor authentication provides stronger identification of users by requiring two different identity components. A good everyday example is the identification banks require for withdrawing money from a cash machine – the correct combination of a bankcard and a personal identification number (PIN).
Most consumers don’t associate social media sharing tools as a cloud service but it is. Oversharing on social media has also become a problem also for businesses who often find that workers blur the lines between their work and their private lives. My guidance to consumers is to only share on social media what they don’t mind sharing about themselves publicly. This advice even goes for photos for which one’s settings may be only family and friends, but over time through other people’s shares may be more broadly circulated.
Cloud is our new digital reality and for the most part the convenience benefits outweigh the risks. The tweaks that I have suggested above are a starting point and by no means a comprehensive list. Finally, remember that different consumers will have different thresholds for data security and privacy so there isn’t a single blueprint that applies equally to everyone.
By Evelyn de Souza





