A survey conducted at Black Hat 2015 reveals that endpoint poses the greatest security to threat to cybersecurity, with 90 percent of respondents stating their organizations would be more secure if Flash was disabled.
Black Hat 2015: State of Security, released by Bromiun Inc. yesterday, also reveals that a large number of businesses find the implementation of patches for “zero-day vulnerabilities” in the software they are using (including Internet browsers and Flash) to be an enormous challenge. While most believed that the recently launched Windows 10 does improve security, a third said these improvements were not sufficient.
“Flash has become a prime target for hackers, thanks to the popularity and widespread use of the software, so it’s no surprise an overwhelming majority of those surveyed believe their organizations would be safer without Flash,” Clinton Karr, senior security strategist at Bromium told CloudTweaks today. “This has been a huge topic within the industry as we’ve seen numerous critical patches for the software over the course of this year. As hackers continue to exploit Flash users, it’s extremely important for companies to consider disabling it or to turn to new technology that doesn’t jeopardize productivity and security.”
Bromium, considered a pioneer in threat isolation technology to prevent breaches relating to data, surveyed more than 100 IT professionals at the annual Black Hat conference held in Nevada earlier this month.
The survey found that most participants were cynical though pragmatic, identifying that end users introduce the greatest security risk. A total of 55 percent selected the endpoint, while 27 percent said insider threats were the biggest problem. Only 9 percent said the cloud was the greatest risk, and 9 percent said networks.
Researchers did not find this surprising, since the human element is an obvious security risk – particularly when people use untrusted networks outside their office or home environment, including coffee shops, hotels, and airports. This human element not only increases the endpoint risk, but also the risk of cyber attack, largely because typical detection-based security solutions like antivirus simply don’t identify malicious content on the Internet or in emails.
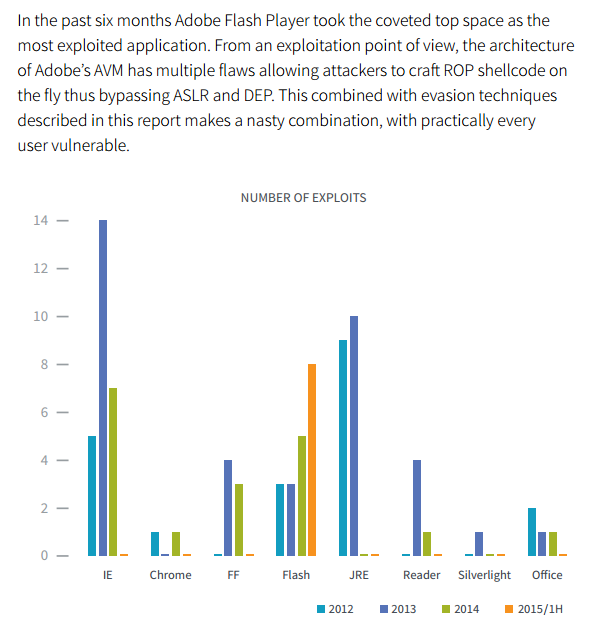
There is no doubt that IT security professionals are ultra-aware of the security threats Flash poses, with 90 percent of survey participants stating that their organization would definitely be more secure if they disabled Flash. This is in keeping with an earlier Bromium Labs report Endpoint Exploitation Trends, that found Flash had been responsible for more “exploits” than any other software during the first half of 2015. Further, Flash vulnerabilities are currently so overwhelmingly problematic that YouTube has switched from Flash to HTML5; Mozilla has temporarily blocked Flash from Firefox; and the new security chief of Facebook, Alex Stamos has called for Flash to be “killed.”
According to the Black Hat survey report, the reason there are so many Flash exploits is simply because of the popularity of the software, just as Java exploits used to be very common.
The challenge for IT security professionals is that disabling Flash is not always an option they can choose – specially since many operations teams insist that it will make the organizations less productive and even “break” some of their critical applications if it was disabled.
Of those who participated in the survey, 44 percent said productivity would be adversely affected.
Implementing patches was reported to be a major problem for many of the information security professionals who responded to the survey. Only 10 percent said they were able to implement patches for “zero-day vulnerabilities” in the first day after patches were released. Considerably more – 50 percent – could get this done within a week; 22 percent said it takes a month or more.
The greatest concern was for organizations running vulnerable versions of Flash since they could easily be compromised by exploit kits like the currently popular Angler.
While most information security professionals felt critical infrastructure in general was at the most risk of cyber attack, when asked to identify which industries were most vulnerable, 30 percent said financial services. However, ironically, 60 percent felt that financial services had the best security practices, followed by technology (27 percent.)
While 12 percent identified government as being most as risk, 17 percent named health care, and energy equally. Other industries mentioned included retail and transport, both of which were identified by less than half the respondents.
There was mixed reaction to Windows 10, with many professionals (40 percent) having zero opinion about it. Nevertheless, 23 percent said security was dramatically improved, while 33 percent said the improvement was not sufficient. Only 4 percent said that there was no improvement at all.
Since Windows 10 was released shortly before Black Hat 2015, none of the respondents had upgraded to Windows 10: only about 10 percent planned to upgrade in the next three months. A large percentage (40) had no plans to upgrade, and 31 percent said they would wait at least a year before upgrading.
Ultimately, the Bromium survey found that whilst the endpoint is currently considered to be the greatest security risk, the human element is just one element of the risk. The other major vulnerability is software, which is a trend the company continues to research on an ongoing basis.
By Penny Swift





