Cyber Physical Systems (CPS) are a nomenclature used to define the world beyond IoT devices. CPS includes the robotic and automation systems that interact with the IoT devices. Based on that changing landscape I have come to realize that CPS and by default IoT devices actually have three distinct concerns.
The three areas outside of the CPS/IoT that have great bearing are Access, Power and Data. Power in that each of the CPS devices will require some sort of power supply. Be it a human changed battery, a rechargeable battery or a direct connection to a power supply. The supply may be a wind turbine, solar power, a physical power generator or for that matter a direct connection to the power grid. The device has to be smart enough to understand its power supply. For example if it is a life supporting sensor for an elderly person the only thing that should have more importance in the home for power consumption is the heating and cooling system. It should however be smart enough to contact help and then shut off so that other critical systems are taxed or drained.
The next area is that of data. The internet of data is huge. It isn’t just the concept of big data or the concept of data analytics. It is the production, consumption, storage and movement of massive amounts of information. There are more than 10b (billion) IoT devices today and that number is growing. In fact from 2014 to 2015 alone the total number of devices deployed increased by 13% according to analysts.
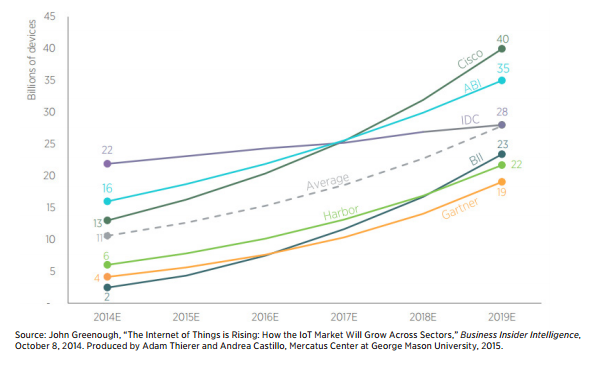
IoT devices produced 113Zb (Zeta bytes) of data in 2013. There are two interesting things about information, it is normally produced for a reason and often someone consumes it. The rate and amount of the data produced is staggering. One of the concepts that is intriguing is the broad concept.
This brings us to the last part of this puzzle Access. Access represents more than simply what is the interface or connection type you use to connect to the IoT or CPS device. Access refers to the security of the device, the data produced and as much as possible the data through the lifecycle of use. Not all data can be protected throughout its entire lifecycle. The minute part of that half-life is spent on a mobile device the reality is you can’t manage it as effectively as you would be able to otherwise. Remote wipe signals require a network connection to the device. Data on a cellular device may also cause a different problem in that they may not be refreshed at the same rate as other devices. That potentially causes risks with the data being out of date.
The three comprise the out core of what CPS will become. We could argue that the three wouldn’t be proportional rather data would be by far the largest with power most likely being the smallest. But for now we will represent them as equal conspirators. We could also argue that bandwidth will be critical going forward. We can also argue that the very IoT devices and the automation and other components that make up the broader CPS infrastructure will get smarter as well. Those two issues would certainly shape and modify the impact of the three core concerns. But as we head into the IoT futures it is important that we build systems that meet all three of the core areas.
I have to go for now I have to change the batteries in all my IoT devices.
By Scott Andersen





