Two new security tools are changing the way that companies think about security in the age of cloud computing.
Data Science continues to enjoy massive growth around the world as the adoption of cloud computing gains further traction amongst organizations. And security is never far from the heart of issues around cloud usage, as the potential costs of malicious strikes grows larger and larger due to the integrated nature of the global economy.
A recent survey of over 1600 IT professionals around the world and the state of their public cloud adoption revealed that nearly half of all organizations had at least 1 complete outage during the last year, averaging around 80 minutes in length. It may not sound like that much but the average annual losses have been estimated at just under US$4 million dollars due to outages, at an average cost of $12, 250 per minute.
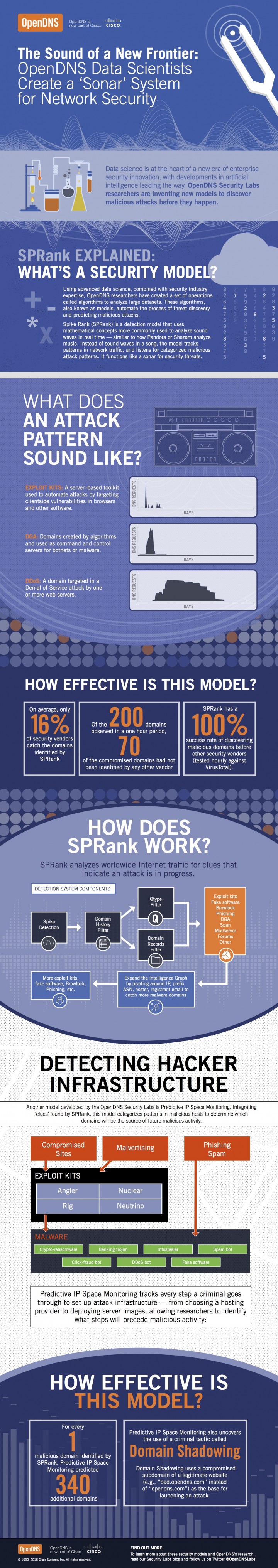
With IT departments having less control over their security due to the nature of the public cloud, there is a growing need for a new generation of security tools. Two new models from OpenDNS Security Labs are attracting much interest due to their algorithm-based approach that “automates the process of threat discovery and predicting malicious attacks”. The detection model called ‘SPRank‘ (Spike Rank) tracks “patterns in network traffic, and listens for categorized malicious attack patterns”, in a way that can be compared to how music apps Pandora or Shazaam ‘’listen’’ to musical structures to identify individual songs.
(Infographic Source: OpenDNS)
It’s a massive undertaking as SPRank is effectively analyzing worldwide Internet traffic for clues which would indicate that an attack is in progress. Initial testing has proven remarkably effective. In controlled tests with other security vendors, SPRank identified “70 compromised domains that had not been identified by any other vendor”, and on average, ”only 16% of security vendors catch the domains which are identified by SPRank”.
An even more secure next step is being called Predictive IP Space Monitoring and it takes the data generated in SPRank to a whole new level by tracking the steps a criminal goes through to set up attack infrastructure; from ‘’choosing a hosting provider to deploying server images’’. This data is invaluable in helping to predict where the next attack will be coming from.
The game of cat and mouse between criminals and the security minds dedicated to stopping them has been going on for years. With the cloud becoming such an incredibly valuable tool in the business mix of major economies, it’s no surprise that more and more sophisticated tools are being deployed to deal with more and more sophisticated threats.
By Jeremy Daniel





