Last year’s massive data breach of Office of Personnel Management, as well as other recent cyber security incidents affecting federal agencies, underscored the urgency of bringing the federal government’s security infrastructure up to date. Although many agencies have made strides toward hardening their cyber security, outdated IT infrastructure and architecture is still common — making the federal government an easy cyber attack target.
In 2014, Congress enacted the Federal Information Technology Acquisition Reform Act (FITARA), giving CIOs significant powers in IT decisions, including new technology acquisitions. But based on an analysis of a scorecard created to measure the implementation of four key provisions of the legislation, the top 24 federal agencies received an average overall “grade” of D.
This raises the question: How well is the federal government prepared for cyber attacks?

FITARA was “the most comprehensive overhaul of government IT in 18 years,” according to a Gartner analysis. Its purpose was to reform IT procurement and management to make it more agile and efficient.
Because FITARA’s intent was to drastically cut spending on outdated, legacy technology, the expectation was that it would minimize the vulnerabilities that create the perfect storm for cyber attackers.
But a recently published audit of the Department of Homeland Security — considered to have some of the best cyber security measures among federal agencies — showed that its IT infrastructure still relies on dozens of unpatched, vulnerable databases.
The “Evaluation of DHS’s Information Security Program for Fiscal Year 2015” report, by the office of Inspector General (OIG), found a long list of other shortcomings. They included 220 “sensitive but unclassified,” “secret” and “top secret” systems with “expired authorities to operate,” which would imply that those systems were no longer regularly patched and maintained. And even many systems that were actively maintained didn’t have current security patches.
It’s worth mentioning that the entities where cyber security is especially critical were at the top of the OIG list as having the most vulnerable systems — 26 systems inside the Coast Guard, 25 at FEMA, 11 at DHS’ own headquarters, 14 at Customs and Border Protection and 10 at Transportation Security Administration. This audit shows that the government is still a long way from coming up-to-speed with its cyber attack defenses.
While the OIG audit focused on compliance related to the Federal Information Security Modernization Act (FISMA), it reflects the same concerns exposed by the recent FITARA scorecard.
In releasing the scorecard, members of the House Oversight Committee wrote, “For decades, the federal government has operated with poorly managed and outdated IT infrastructure. Cyber attacks are a real threat to this country. Federal agencies must act now.”
(Image Source: Oversight.house.gov)
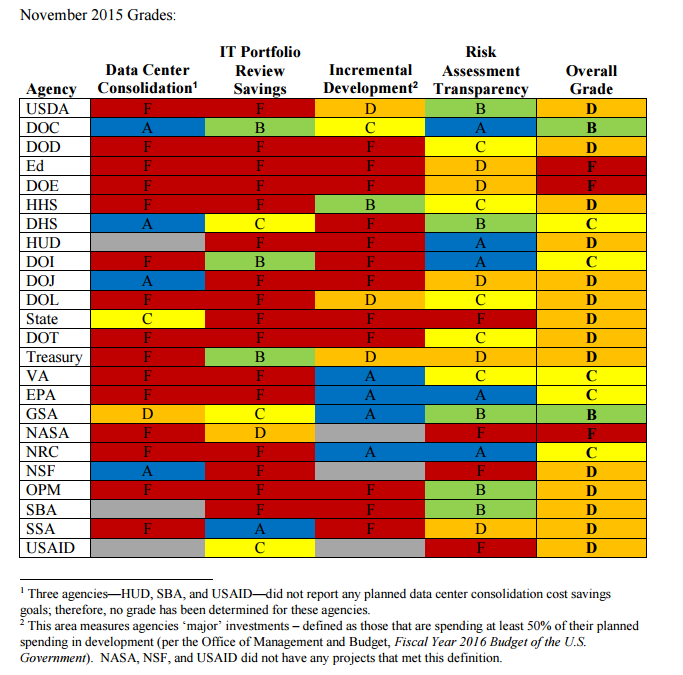
The scorecard looked at FITARA implementation progress in four areas: data center consolidation, IT portfolio review savings, risk assessment transparency and incremental development. Factors considered for the grades included implementation of best practices for risk assessment, increasing the powers of CIOs and trimming wasteful spending.
The Department of Corrections and the General Services Administration received the only Bs (there were no As), while five agencies including DHS scored Cs. Energy and Education failed, and the other 16 all came in with Ds.
In the data center category, 15 of the agencies received Fs (three of the 24 did not report consolidation), while 16 agencies had Fs in the review savings category.
The grades in these two areas were calculated based on how well the agencies saved money by reviewing their IT portfolios as well as consolidating the data centers. In fact, F. David Powner, director of GAO’s information technology management issues, said during a committee hearing that the number of federal data centers has actually grown, to 11,700, and only 275 of those are considered “core.”
In the incremental development area, the grades were based on how many IT projects that were part of major investments successfully achieved completion and delivery every six months. Again, a dozen agencies failed completely (and three others didn’t have any projects meeting the criteria).
The last area measured how well agencies managed the major IT projects’ risks. This is one category where many agencies fared much better, with only four receiving Fs while 10 receiving As and Bs.
While the entire scorecard poses a major concern, it’s especially troubling to see DHS, which is tasked with overseeing the country’s security, only managing to score a C.
The same goes for the State Department — which scored a D — considering the email server scandal former Secretary of State Hillary Clinton had been embroiled in. Not to mention the major cyber attack that had crippled State’s unclassified email system, which had to be completely shut down and couldn’t be mitigated for months.
It’s also worth calling out OPM, which received a D, since its breach compromised personal data of 21.5 million federal employees. Security experts pointed out that OPM essentially “left the barn doors open” because of its poor security measures.
Veterans Affairs’ “C” and Department of Education’s F add a layer of concern because of the Health Insurance Portability and Accountability Act (HIPAA), which was designed to protect and secure protected health information (PHI).
The VA, which runs the country’s “largest integrated healthcare system” through its Veterans Health Administration, is subject to HIPAA as a “business associate” of the VHA. The rash of cyber security breaches of healthcare providers last year was proof that bad actors are increasingly seeking out PHI because its value on the black market is much higher than financial information. The federal government should practice what it preaches, and make sure its own departments that are subject to HIPAA have strong cybersecurity defenses.
The Department of Education itself is not subject to HIPAA, but many of the public schools and institutions that it funds — and which report data back to the agency — are. The House Oversight Committee Chairman Rep. Jason Chaffetz has warned that OPM’s breach would pale in comparison to the damage that cybercriminals could inflict on the Department of Education.
“I think ultimately that’s going to be the largest data breach that we’ve ever seen in the history of our nation,” he said, regarding a breach of Education, at a Brookings Institution event.
The FITARA scorecard, of course, wasn’t intended to point fingers at the federal government for doing a poor job. Still, considering the estimated IT federal budget at $79.8 billion for fiscal year 2016 (which ends on Sept. 30, 2016), the scorecard results pose serious concerns about the nation’s cyber resilience.
As Federal CIO Tony Scott put it during the committee’s hearing, “FITARA presents a historic opportunity to reform the management of information technology across the federal government.” He also said that the work and commitment required to fully implement this law couldn’t be underestimated.
Let’s just hope that the next FITARA scorecard shows much better progress than an average of “D.”
By Sekhar Sarukkai





