C-suite executives have woken up to the threat posed by data theft, denial-of-service attacks and vulnerable systems. In 2015, for example, a series of high-profile cases illustrated the degree to which such attacks can damage a company’s reputation, brand and, ultimately, profits. Where businesses once undervalued cybersecurity, considering it the domain of CIOs and IT departments, it’s now squarely at the top of the agenda. Recognising the threat is one thing. The challenge for organizations is to find ways of understanding the risks and constructing robust systems. In this article, I want to look at how a risk-first approach to IT security and shrewd recruitment can boost a business’s immune system.
As companies continue to digitize their operations, the potential of information security breaches to damage trust and their competitive position increases. Information security risks are multiple and manifold. They could, for example, involve companies that rely on information as a means of generating value, such as banks or energy suppliers who must address a wide range of threats.

Equally, any company that holds large quantities of customer information runs a risk. This risk is particularly acute for SMEs, for whom the financial costs of information security can be prohibitive. In the Digital Economy, information is an asset that creates value for organizations; but this value is what makes it vulnerable.
Identifying these risks evidently requires expertise and coordination. Many businesses no longer see information security as simply something to do with IT. Rather, IT security is now bound up with wider risk management policies. But old habits, and ingrained divisions, can still be an obstacle for organizations. This goes for IT departments as well as management. In the past, IT departments habitually addressed security challenges by starting with technology and costing before moving on to consider the potential risk of an investment. In 2016, however, security has moved to front of
people’s thinking. Investing in the right IT systems now means first identifying the risk and then finding the devices and technology.
One area where firms have been slower to respond, however, is recruitment. The shift in the landscape has opened up a sizable skills gap, with organizations competing to recruit and retain employees with the necessary skills and experience. While good news for employees who can easily
find opportunities in the public and private sectors, this has caused problems for CISOs tasked with sourcing and training the people who can both identify and take steps to mitigate the cybersecurity risks that businesses face. In this environment, the challenge for organizations is to find ways to open up career paths and build expertise into a business, while still keeping costs down. In a survey carried out by Deloitte, 59% of CISOs identified the inadequate availability of cybersecurity professionals as a barrier to information security, with many turning to outsourcing to fill the gap.
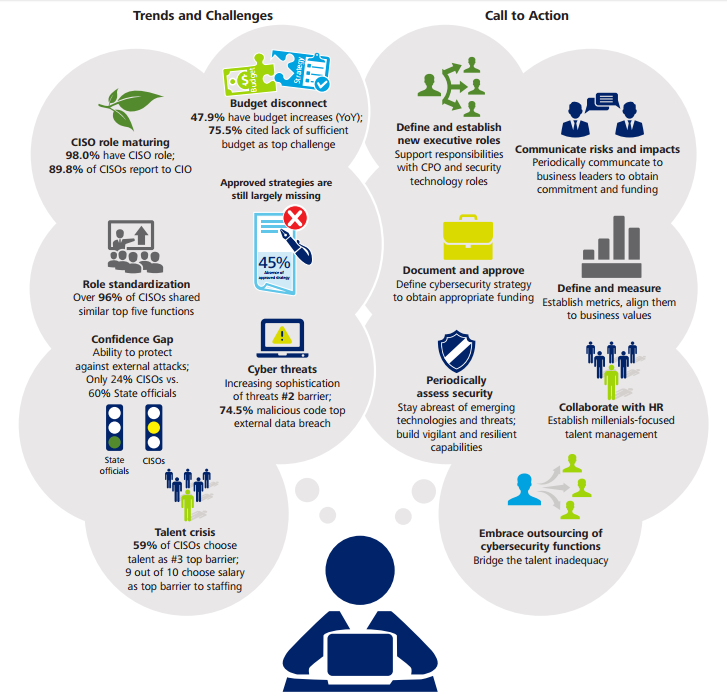
To my mind, this barrier serves to reinforce the importance of taking holistic approach to information security. IT departments must communicate effectively with management and HR departments to ensure that risks are identified and addressed, and that the organization has the right people for the job. As digitization continues apace, getting this process right is only going to become more important.
By George Foot





