There is no longer any subjectivity in this statement: security is at the top of list for all CIOs. Every meeting I’ve attended over the last three months has been dominated by the topic of security and when it’s injected into the conversation, it’s not necessarily by my team, but the customer.
Security has been a hot topic for the last three years beginning when prime time news displayed the list of Fortune 500 logos that had fallen victim to foreign hackers. As with most IT trends, the mid-sized enterprises have followed their larger counterpart’s actions driving their current interest in and need for heightened security. Though this need has been met with confusion, questions and sighs on how to achieve the goal of increasing security and thereby adherence to compliance.

Security is a combination of education with the usual people, process and technology equation. For the medium size enterprise this can be a tough equation to solve given limited resources and budget. With the demand for security engineers increasing by 74% over the last three years and 30%-40% of security projects ending up in failed implementations, demonstrating no value to the enterprise, it is easy to see why. So, how do security managers succeed with the odds seemingly stacked against them?
There are two forces crossing in the industry, which if leveraged appropriately, can help enterprises close their security gap. First, from a technology perspective we are at a point where products have matured to the point where consolidation is possible without the loss of protection. The features of many point products which have emerged over the last three years are now being rolled in as features on existing products such as firewalls or other perimeter security products. By leveraging the mature vendors that offer various security products on a single platform administration effort is lowered while integration and security intelligence is heightened.
One example of this is the concept of “sand boxing” web traffic or email traffic and watching to see if malicious activity occurs. If so, the traffic could be sanitized or blocked.
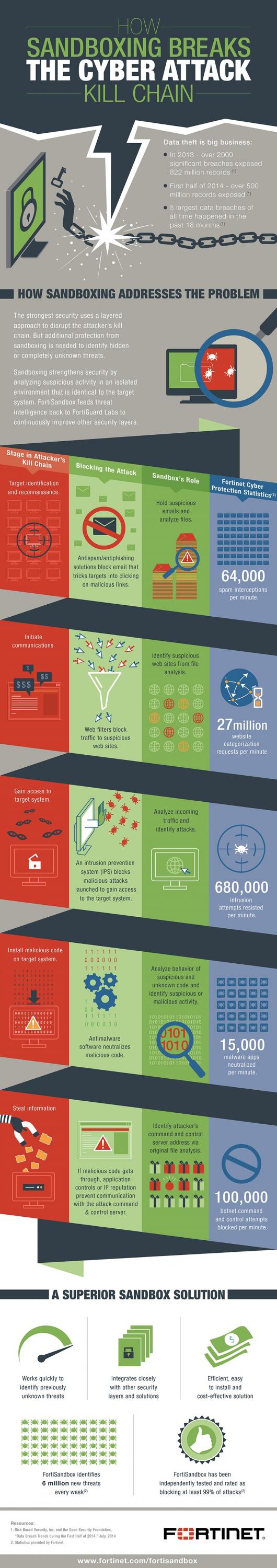
(Infographic Source: Fortinet.com)
When this technology first arrived it was introduced by market disruptors and a was a new platform to be absorbed by the security staff. Today, the same feature is now part of many firewalls and web security gateway products that are already in place. A feature to be turned on rather than a new platform to be learned. So the point to take away is look to simplify the management while gaining better integration and security intelligence by consolidating security features on a common product platform.
The second force, driven by Cloud services, is the many Cloud Enabled Managed Service Providers now offering managed security services. These providers can offer managed firewall, IPS, SIEM, web security and email security solution reducing the number of security engineers required to be staffed by the enterprise which solves the staffing shortage for them. In addition to offering the technology to provide these services, the main advantage gained with MSPs is solid process and methodology which assures these tools will provide business value and be successfully implemented.
Another offering proven to be useful is the VCISO or Virtual Security Officer. Enterprise of medium size often cannot afford a dedicated CISO but still have the need for the position. By contracting with a provider that offers a VCISO, an enterprise can gain access to a CISO skillset for a fraction of the cost of hiring one.
In closing, budget constraints and staffing issues are real barriers and have stopped many companies from achieving their security goals.
Seize the moment, assess your current security environment and look for ways to consolidate and simplify security platforms to gain the most value. Then look to fill the gaps with technology, people and process with qualified Service Providers. Pay special attention to those providers that bring the process and methodology to assure success in the technologies they represent as that is as important as the technology itself. Filling your CISO role with an on demand VCISO can address your CISO needs in an economical and efficient manner.
Marc Malizia





