Primarily evidenced by the explosive growth several startups have implemented lifehack tweaks to help with growth hacking campaigns. One reason that startups specifically have been making use of growth hacking is the smaller budgets they contend with compelling a ‘ship and revise’ strategy. These startups will often send out their initial products early on, encourage early adopters to provide rigorous feedback, and then refine their products. Large, established organizations tend, instead, to consume hefty budgets for traditional marketing and launches, but this often means customers aren’t getting the functionality they want. And so, taking a leaf out of the startup book of marketing, most organizations could benefit from growth hacking and its accompanying devices.
Growth hacks are shortcuts or loopholes to growth, usually extremely high growth, of new products. They are low cost, often free, and rely on word of mouth. The best growth hacks take full advantage of digital and social media and go viral through satisfied users spreading the word. Data analysis, user feedback, and growth objectives are key to growth hacking, and just as effective implementation can mean tremendous success, so poor execution could end in disaster. Netflix, Twitter, Dropbox, Uber, Airbnb, Slack – all Cloud based SaaS examples of brands that have successfully hacked their growth. The list of failures is harder to dig up, but undoubtedly much longer.
Below is an infographic discovered via pierrelechelle covering Slack’s growth which has now reached over 1 million active users with no end in site.
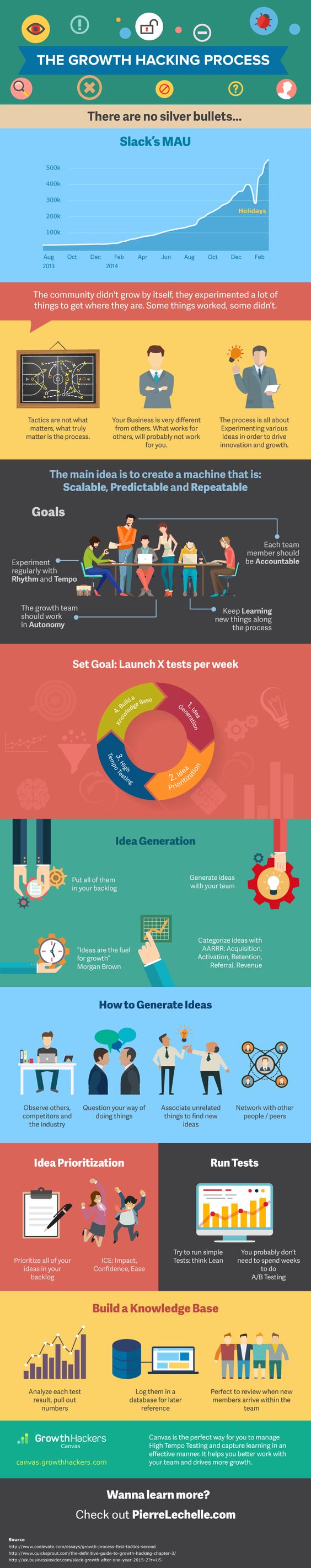
Considering its ideals of creativity and ingenuity, growth hacking can be a risky device. Though they often seem like cheap and easy solutions, many growth hacks fizzle out long before they provide the necessary boost to the business. Three core hazards stand out:
Getting the customers to your site is, of course, an essential goal, but if they’re just window shopping, your hacks aren’t successful. Without enough paying customers, no amount of positive word of mouth will do you any good, so be sure to turn visitors into committed subscribers. Website design is one quick-fix strategy for improving conversion rates, keeping navigation neat and intuitive, and including accessible copy. Make sure you’ve included one strong call to action that allows customers to spread the word via social media and ensure your sign-up is quick and easy.
If you’re not correctly measuring campaign results and then using that information to refine your efforts you’re wasting time and money. Fruitful growth hackers embrace a trial and error mindset that views failures as that paving stones to success and avidly experiment with their hacks. Track data, measure results, and answer questions; set a measurable goal and track your progress. A successful campaign provides data for Scaling up the next campaign; a ‘failed’ campaign shows you how to adapt your next one.
Creating hype is essential, but no amount of growth hacking hype can make a bad product look good. Quite the opposite. Growth hacking relies on positive consumer feedback, and if you’re delivering a product or service that disappoints, prospective users will vanish. Some suggest a 95% product investment, 5% marketing investment, ensuring your product is the best it can be, and organizations need to honestly and realistically evaluate product strengths and weaknesses so that they’re ready to work on the feedback they get. Growth hacking is valued by marketers and consumers alike because it is based on candid product communication and a loyal user base.
By Jennifer Klostermann





