The presence and value of Cloud tools have seeped into virtually every industry, and the medical profession is certainly no exception. However, because of the special rules regarding patient privacy, specifically those found in HIPAA, people handling patient information must follow specific guidelines that in many cases, are violated by standard cloud services. Of course many services claim HIPAA compliance in order to attract healthcare clients, however, an approved “HIPAA certification” doesn’t exist for cloud services. Therefore, it is important for people working in the medical industry to be aware of the rules and options when utilizing the Cloud for their business.
All medical professionals (and most people who’ve been to the doctor) are familiar with HIPAA, but to lay a foundation for this article, here is a little background. Congress passed the health Insurance Portability and Accountability Act back in 1996. You have HIPAA to thank for the enforcement of privacy standards (Infographic below by Cardigm) that protect your personal health records (as well as health insurance portability, though the focus of this article will be the former). HIPAA makes provisions against industry fraud, imposes nationwide standards for the electronic management of records, and consequently ensures that confidential information will be handled in the appropriate manner.
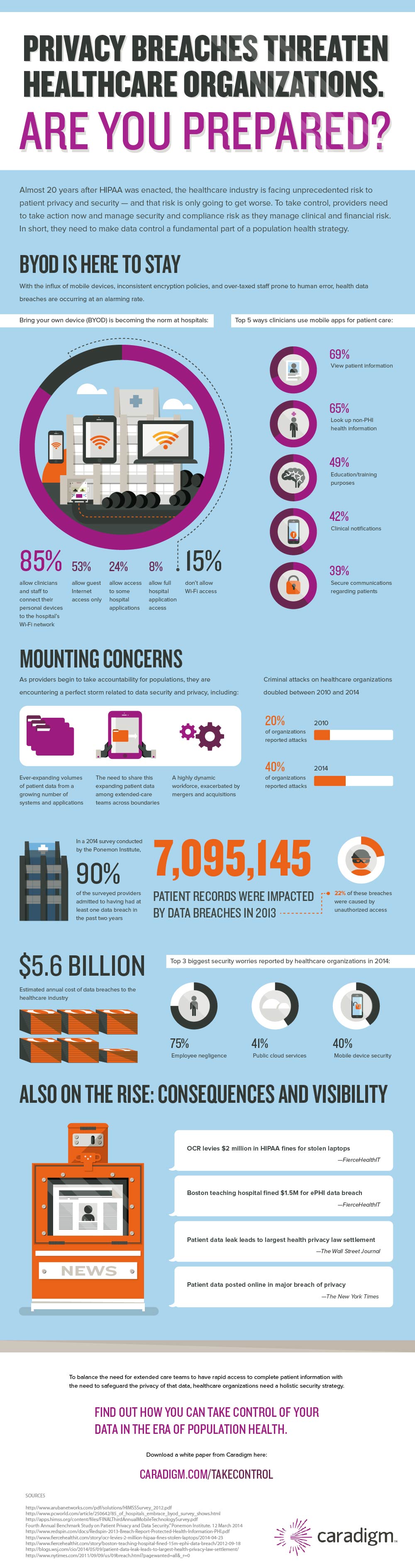
However, technology has come a long way since the act’s initial passage 20 years ago. As a result, it’s now far easier to commit a HIPAA violation than you might think. Businesses working in or with the medical industry must take particular care when it comes to the cloud to avoid the hefty fines that come with such violations. When planning processes and acquiring tools to adhere to HIPAA rules, additional steps often need to be taken to ensure that security is not sacrificed for the sake of the cloud’s convenience.
The primary difficulty of integrating private information with the cloud is that most major cloud services (e.g. Dropbox) are not managed by medical professionals and they reserve the right to access files on hosted on their servers. Therefore, any Instance in which these third parties have access to confidential client information would constitute a violation of HIPAA.
There are a few potential solutions to this issue, the first being a Business Associate Agreement (BAA). In this case, the third-party service enters an agreement allowing them to act as the business associate of a medical professional, thus protecting client info and meeting HIPAA standards. Unfortunately, this can potentially increase the provider’s liability and mean penalties for them should a breach occur, which means they’re less likely to submit to such an agreement. (Apple, for example, refuses to sign the BAA that would make iCloud HIPAA-compliant.)
Here are some cloud services that will sign Business Associate Agreements:
If a BAA isn’t available, another option is utilization of a third-party encryption app. These services encrypt files before they are uploaded to the cloud, rendering them unreadable by the cloud service provider. A little research can quickly turn up alternative encryption solutions to products you may already be using, such as CloudLock for Google Apps for Work. Another option is to invest in an entirely separate service, such as Tresorit, which provides encryption as well as additional features, such as the option to “unsend” or revoke access to mistakenly sent data. Encryption also protects against instances of hacking and lost devices (i.e. laptop, phone), which can be potential threats to client security.
Another option is to use a service that offers a HIPAA setting, which essentially encrypts the files in the way a third party application might and will typically remove other features that violate HIPAA like sending files through email. However, without a signed BAA from the vendor, any mishandling of the information would still be a HIPAA violation.
Transmitting consumer information via email is a violation of HIPPA, which is why faxing is still very common in the medical industry. While online fax services (e.g. eFax) utilize cloud portals where faxes can be retrieved, they typically also email a copy to the recipient. This constitutes a violation of HIPAA. However, medical professionals can use online fax services that offer special features (often referred to as a HIPAA conduit) like file encryption and fax notification via email only. As mentioned above, a HIPAA conduit setting alone is not as strong of a liability protection as a signed BAA.
In the conversation surrounding HIPAA compliance, it’s crucial to retain as much information as you can about the status and location of confidential information. As putting any data into the cloud means losing a degree of control, those interested in avoiding violations should know the identity of every person that has access to the information, where the service provider is located, and the exact nature and content of the data itself. The responsibility to ensure patient privacy is ultimately borne by the medical professional. If this includes using the cloud—and in this day and age, it probably does—be sure to plan accordingly.
By Leo Welder





