For over 20 years, organizations have been attempting to secure their networks and protect their data. However, have any of their efforts really improved security? Today we hear journalists and industry experts talk about the erosion of the perimeter. Some say it’s squishy, others say it’s spongy, and yet another claims it crunchy. Are they trying to say the perimeter is changing, or that the perimeter no longer exists?
In the context of the devices that allow humans to look at data, that perimeter is changing dramatically. From the workstations and laptops, to handheld computing devices, trying to define a security perimeter in this perspective can be challenging. Mobility has changed the client-side perimeter overnight. However, does the concept of mobility mean that perimeters can no longer exist?
Regardless of where data resides, anytime data is accessed, it is done through a perimeter. The world has benefited from wireless technologies that enabled mobility for years. But is there such a thing as the “virtual wire”? Anytime data enters a server, or is uploaded to or downloaded from a server, it will eventually traverse a piece of wire. That wire may be made of copper, or that wire may be made of fiber optics. Either way it’s still a piece of wire where both good guys and bad guys access data. That piece of wire needs to be protected at all costs.
The most secure method of protecting data on a server is to remove the wire that allows clients to access it. However, we all know what happens when you remove the wire. Short of that, how does one go about protecting that piece of wire? It all begins with a comprehensive, in-depth defense approach. Hackers today are after the data and will go to almost any length to get it. That piece of wire is where most attackers break in.
Years ago, organizations realized that their firewalls were nothing more than speed bumps to the seasoned hacker. Organizations began deploying end-point protection, intrusion detection systems, intrusion preventions systems, web applications firewalls, sandboxes, and the list goes on and on; all in an attempt to protect that piece of wire, and the data that traverses it. One of the main impediments to deploying these point solutions (often manufactured by different vendors) is their failure to interoperate. No single vendor had a complete, end-to-end solution.
Today, organizations understand the evolutionary dilemma of deploying disparate technologies. Instead, most organizations desire an ecosystem of solutions and technologies that interoperate, are fully aware of each other, communicate with each other, and defend that piece of wire to the fullest. They’re looking for a one-stop-shop that can completely defend the perimeters that still exist, and it all begins with the fully aware, hybrid-cloud approach as shown in the picture below.
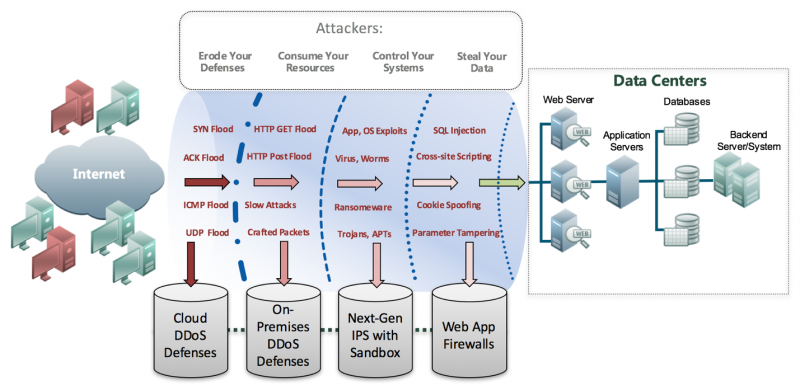
On the far left, both good (green) and malicious (red) clients are shown. On the far right shows a perimeter that exists when accessing data within a datacenter (or even within a cloud). What you put in between those two entities makes all the difference in the world.
As shown above, attackers erode your defenses, consume your resources, control your systems, and steal your data. In addition, attackers use a host of different attacks shown in red to achieve their goals.
In the fully aware, hybrid-cloud approach, the first line of defense begins with Cloud DDoS Defenses as shown on the bottom left. These defenses ensure that your organization is never taken offline due to a large, volumetric DDoS attack. But more importantly, they play a vital role ensuring all other defenses are not affected by a DDoS attack. All types of flooding attacks are simply eliminated by the Cloud DDoS Defenses.
On-Premises DDoS Defenses is the second line of defense. These defenses are deployed to ensure that low and slow, short-duration, and/or partial saturation attacks never consume your resources – including your security team. On-Premises DDoS Defenses must work in concert with the Cloud DDoS Defenses, ensuring that all unwanted denial of service (and other traffic types) are dropped with no further downstream inspection.
The third line of defense includes Next-Gen IPS with Sandbox. These systems are designed to eliminate Malware intended to compromise and control your devices. These defenses look deep inside payloads to determine the intent of the traffic that makes it through the Cloud and On-Premises Defenses. Known malware is eliminated by the IPS. Unknown malware is eliminated by the Sandbox. Working in concert, both known and unknown malware, which are the sources of many advanced persistent threat attacks, are eliminated.
Web Application Firewalls (WAF) are the final line of perimeter defense. WAFs ensure that all client traffic behaviors when accessing data, align with corporate security policies. Data is given the utmost protection. WAFs provide complete defense for the OWASP Top Ten vulnerabilities, regardless of clear-text or encrypted traffic streams, and are deployed as close to the data as possible.
One may ask where the traditional firewall falls into all of this? The defense layers described above are designed to augment your existing firewall and provide protection for threats that the firewall is not able to prevent. Simply put, the firewall is able to block unwanted TCP and UDP ports but is not capable of preventing modern advanced threats.
The hybrid-cloud approach to security is very effective. However, the best protection is provided by a defense-in-depth architecture incorporating the four lines of defense covered above. The real power of this approach is realized if the architecture also uses closed-loop threat intelligence, whereby all four lines of defense not only collect attack data, but also share that data across all defenses. In this way, all four enforcement layers have the latest information about the complete threat landscape to reduce the overall security risk for any organization.
By Stephen Gates





