You can imagine the scene: you’ve just completed that business plan and a set of accounts. Finally, it’s done and saved, ready for a final read through and to be sent out to your contact list. And right when you’re ready to click “Send”, the next thing you see on the screen is a pop-up window saying something like “Your personal files have been encrypted”. It also states that if you want them decrypted, you’ll need to pay. You quickly go to the folder containing your business plan data files, double click on the spreadsheet, but it won’t open, it’s encrypted; click on the text document, it won’t open either, it’s also encrypted. That cold fear spreads across your body as you stare at the screen, realizing that you’ve been hacked.
The above situation is becoming extremely common. The malware responsible for encrypting the files is known as ransomware, and it is arguably the most sinister type of malware to enter the cyber crime scene. If you become infected by ransomware, it is not just local files that are encrypted – files right across your network, even into remote folders, like Dropbox, can be affected. Once infected, you are then told that if you want to get those files back, you’ll have to pay the cybercriminal an amount, sometimes with many $000’s in bitcoin currency. A recent example was at the Hollywood Presbyterian Medical Center in LA, who ended up paying hackers $17,000 to have their files decrypted. Payment to the cybercriminals behind the attack is a risk, you may not get the decryption code after payment, but even the FBI, who are monitoring ransomware attacks, are currently advising to pay the ransom.
Ransomware is very successful. A McAfee report into the threat shows there has been an almost 10 fold increase in ransomware between 2014 and 2015. The reason for this increase is a reflection of its success – this is a very lucrative method of extorting money from companies of all sizes and types. One of the versions of ransomware, known as CryptoWall, which is routinely monitored by the CyberThreat Alliance, was found to have attempted attacks at almost 500,000 companies. The resultant costs to those companies being around $325 million. With monies like that coming in, cybercriminals will milk this method for a while yet.
Ransomware infections usually come in via one of two routes. Either you get phished, or an ‘exploit kit’ is used:
Phishing threats: These are the most likely methods used to get ransomware onto your PC and network. The threat comes in the form of an email, with an attachment named something like ‘fax’, ‘invoice’, ‘statement’, that sort of thing. It can be a zip, but they are cloaked as pdf or docx files too. If you open that attachment, it initiates the Malware program install and before you know it, your files are encrypted.
“It is extremely important that the users don’t open attachments from unsolicited emails, and to double-check any suspicious emails with their IT security team,” explains Ronnie Wolf, a security expert from GFI Software, and adds: “Once just one PC is infected, the malware spreads quickly through your network, so you need to act fast in order to prevent further damage.”
Exploit kit based threats: Currently, this is the less used method of propagating ransomware infections, but my guess is that it’ll increase in usage because of its effectiveness and stealth. Exploit kits, apps taking advantage of Vulnerabilities in browsers, are often used in a type of threat known as ‘malvertising’, where an online ad or video initiates a malware infection. They work by sending a user who opens a page with an infected ad to a malicious site, which contains the exploit kit.
“This redirect to the bad site is difficult to detect, it’s very fast and known as a ‘drive-by-download’. Once you’re on that site, the exploit kit looks for holes in your browser software or endpoint protection and infects your machine. it literally takes seconds,” adds Ronnie Wolf.
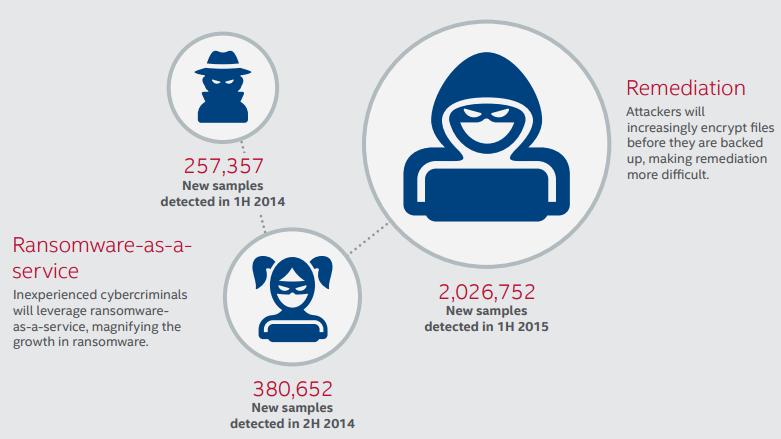
Ransomware comes out in waves or ‘families’. There have been quite a few, some more successful than others. CryptoWall is one of the most famous, but there are many others like TorrentLocker, and Locky. One worrying new movement in the world of ransomware is the creation of DIY ransomware kits or ransomware as a service. Setups like this allow even inexperienced hackers to make use of the malware to make money. The business model is as well thought out as any legitimate business, the service host taking a cut of the extorted monies. This model may well become the infection process of choice throughout the cybercriminal world and poses a major threat to all companies, of all sizes.
In the case of ransomware infections, the first thing you need to do is to cut off the source into your system from both ways in – via emails and Internet sites.
Email based infection: As I mentioned earlier, phishing is the number 1 way that ransomware infects computers. So the first step is to prevent email-borne infections. You need to have an email watch system in place that can spot email-borne threats, like malware, before it hits your inboxes. There are a number of products that can do this, such as GFI MailEssentials, which utilizes multiple anti-virus engines to control and eliminate incoming malware threats.
Internet based infection: Secondly, you need to watch Internet sites being accessed by your users to prevent the exploit kit based ransomware. This up and coming security threat vector is starting to infiltrate the most legitimate of websites, affecting even news sites and popular blogs. Anything that is online ad and video heavy is at risk of carrying ransomware. Making sure that your workforce doesn’t end up downloading malware by being redirected to an exploit kit site is an increasingly important aspect of security monitoring. Doing so manually would be a mission impossible, so products like GFI WebMonitor can help prevent exploit kits from threatening your network security.
Keeping your systems safe from the threat of ransomware will be an ongoing battle. As cybercriminals up their game and bring into play new methods of exploiting your vulnerabilities, the only way you can keep safe is to beat them at their own game and make sure you cut off their source of infection. Ransomware is a modern pandemic, causing untold losses and stress. With any cyber security threat, vigilance is the best way to deal with it. We are in an era where we have to take these threats seriously, if we don’t want to risk losing much more than just a business plan.
By Susan Morrow





