We have a compiled a small list of interesting free security tools and resources as part of our ongoing effort to provide many of the best curated discoveries to our readership. Please continue to visit CloudTweaks as we will be providing several new and updated lists. You can also visit our archived articles covering server, network security scanning as well as performance monitoring tools.
Real time visualization of worldwide cyber attacks showing both the attacking and target country, as well as the malware used for the specific attack. The website also counts the total number of daily cyber attacks worldwide. Visitors can view which are the most attacked countries and where from these attacks originate.

Malware detection flow visualization that uses Kaspersky data to show cyber threats discovered worldwide. It also displays botnet activity. Visitors can view cyber threat stats for a selected country.
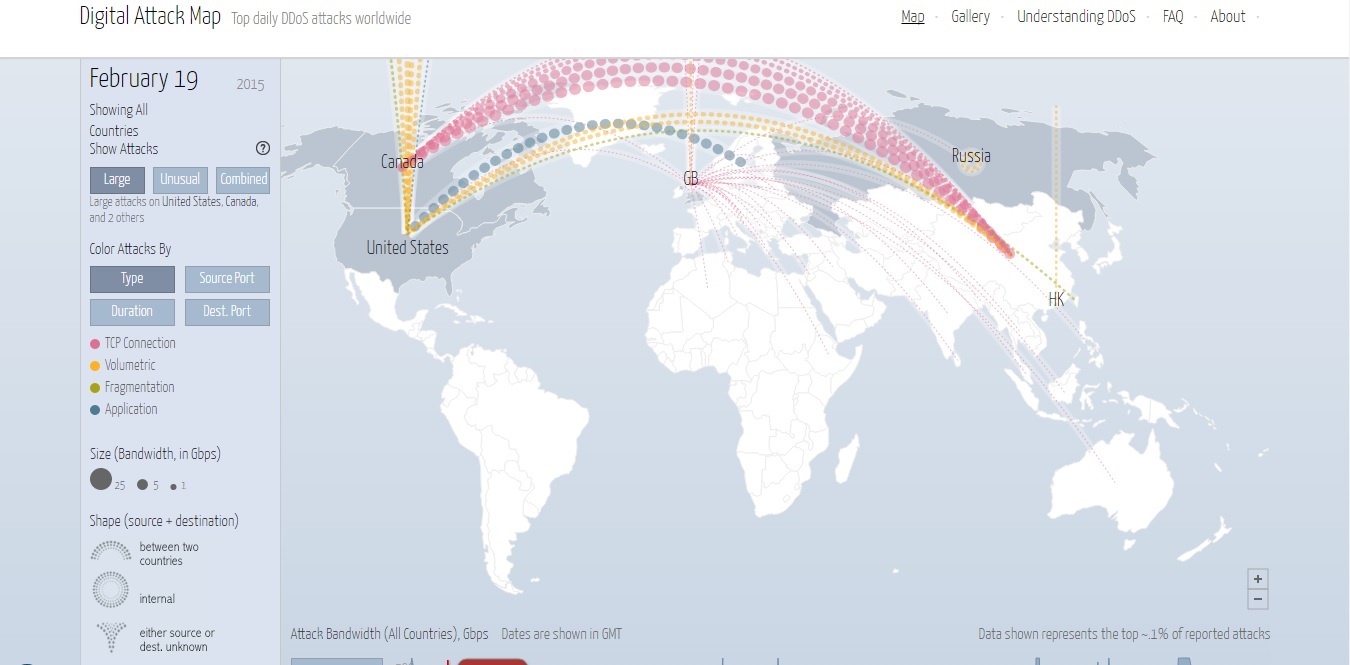
Displays daily statistics on the large and unusual DDoS attacks all over the world. Visitors can view which countries are experiencing unusual high traffic of cyber attacks for a given day and sort attacks by type, duration, source port, and destination port. Real time and pause mode.
Shows detected global cyber attacks in real time. Visitors can view the attacking and the target IP addresses. The website displays the type of malware used, including unknown malware.
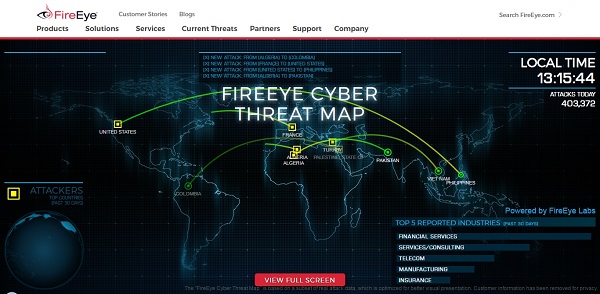
Real time visualization of global cyber attacks. Displays the total number of detected daily attacks as well as the five most attacked industries for the past 30 days. The service lists detected attacks in real time and shows attacking and target country.
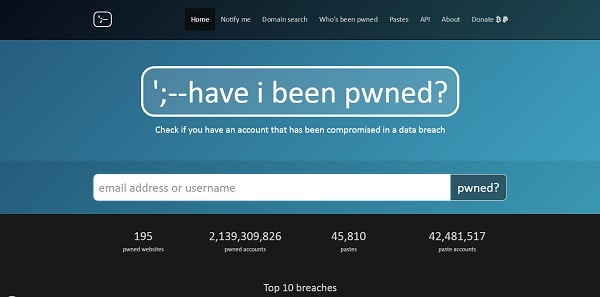
Visitors can check if they have an online account that was compromised in a data breach. Visitors can enter an email address or username to be checked and then get a list of possibly compromised accounts with information what type of data was compromised in the specific hacking attack.
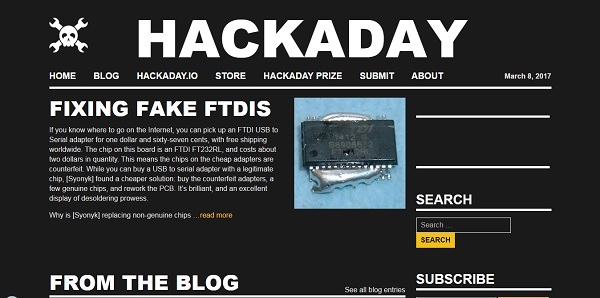
Hardware and software tips for advanced users who want to tweak their hardware or take advantage of cheap source hardware that can be upgraded to perform advanced functions. Visitors can find useful tips and tricks about various hardware topics.
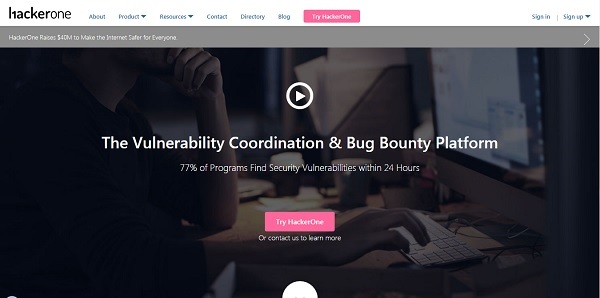
Bug bounty and vulnerability disclosure platform that also hosts a large community of white-hat hackers. Visitors can explore a list of hacker activity and bug bounties awarded. Clicking on a vulnerability report displays info about the severity of a possible bug and its eligibility for a bug bounty.

Displays information about the top weekly online service outages. Visitors can check which companies are currently experiencing downtime issues or select a company from their list. Info about past outages is available.
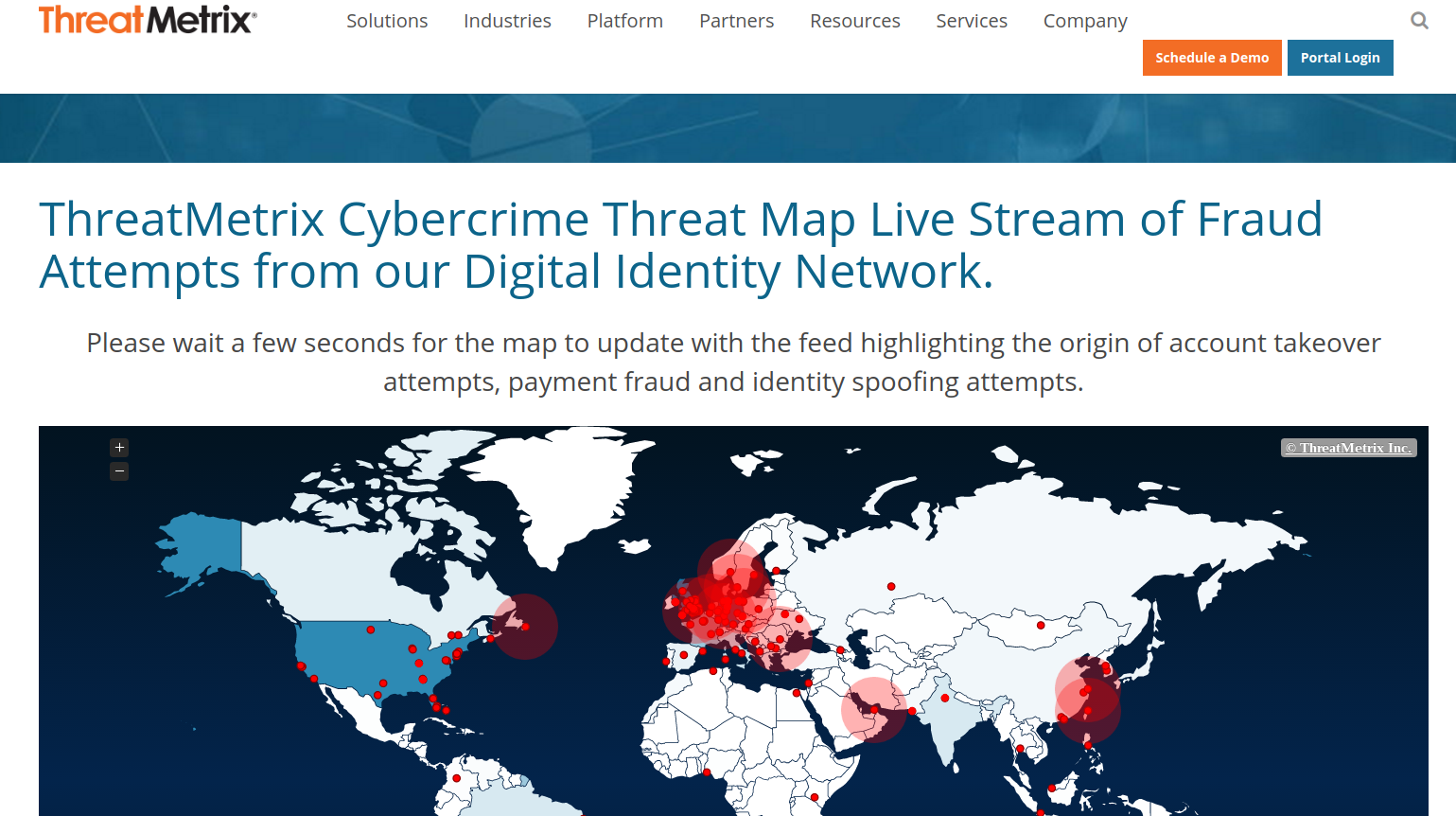
Threat Metrix provides a fairly unquie fraud detection map. It offers a feed highlighting the origin of account takeover attempts, payment fraud and identity spoofing attempts around the world.
By Kiril V Kirilov





