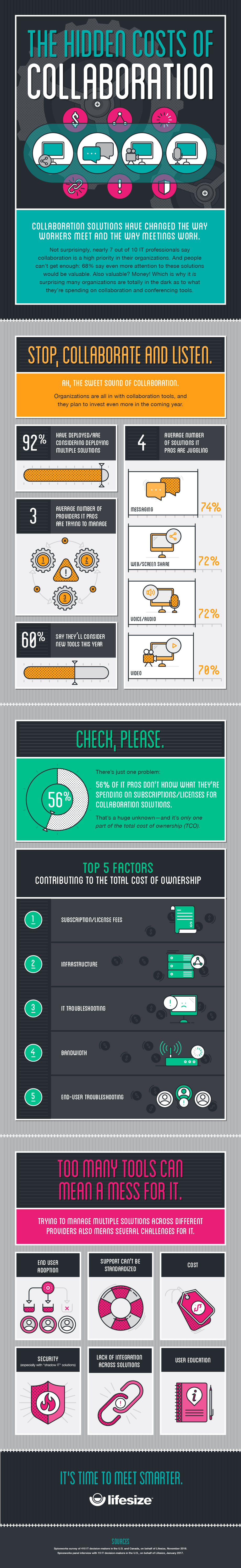
With a distributed workforce being increasingly common in today’s workplace, companies are relying more and more heavily on efficient collaboration tools and techniques. So it’s surprising to discover that over half the IT decision makers (56%) working today have no idea how much they are spending on subscriptions and licenses for collaboration and conferencing.
The survey, commissioned by Lifesize, a global innovator in video conferencing, found that companies generally employ 4.4 tools across 3 providers in a haphazard attempt to meet the demands, without realizing the increased costs, inefficiencies and service quality costs their approach delivers.
Amongst the many issues with the technology are problems with bandwidth limitations, security restrictions on file sharing, poor video quality and compatibility issues. “Managing multiple collaboration solutions from multiple vendors is complicated and chaotic and results in paying a premium for feature overlap, inconsistent experiences, slow adoption and reduced productivity,” said Craig Molloy, Lifesize CEO.
Lifesize’s investment in video collaboration technology has seen them deliver best-in-class, cloud-based video conferencing that improves quality while bringing down the total cost of ownership dramatically – a winning combination which has seen the company go from strength to strength.
By Jeremy Daniel





