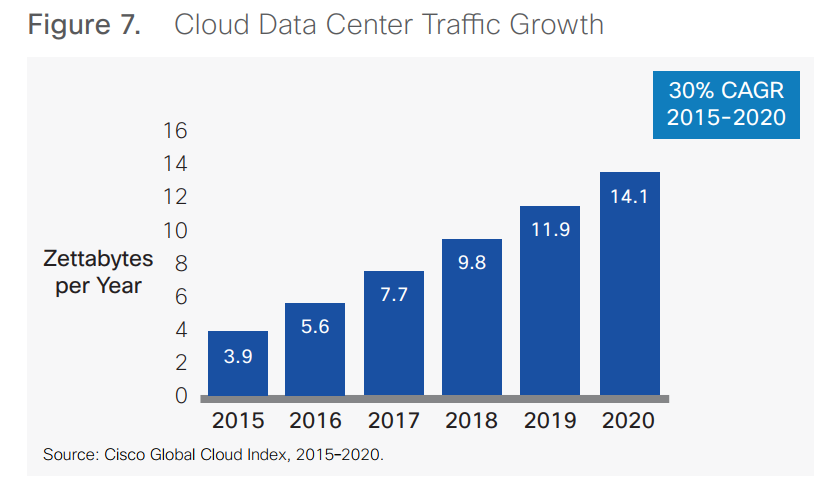
Cisco predicted in their 2016 White Paper, entitled Cisco Global Cloud Index: Forecast and Methodology 2015–2020, that by the end of 2020 annual global cloud IP traffic will reach 14.1 ZB (1.2 ZB per month), up from 3.9 ZB per year (321 EB per month) in 2015. With increasing amounts of sensitive data being stored digitally and transmitted around the world, it becomes increasingly important for companies to invest in data and content protection and governance.
In 2016 in the United States there were more than 450 data breaches in the United States that led to nearly 12.7 million records being exposed. September of last year saw Yahoo reveal that the data of at least 500 million of their user accounts had been stolen – it’s believed to be the biggest data breach from one site in history. This is not a new phenomenon, in 2012 LinkedIn suffered a major breach when 6.5 million encrypted passwords were posted on a Russian site, whilst just in May of this year, MySpace had the usernames, passwords, and email addresses of 360 million users posted on an online forum. (InformationIsBeautiful.net compiled a fantastic visualization that truly helps you gain perspective on the scale of the issue.)
This week, Egnyte launched Egnyte Protect to the general public, it’s a leading cloud based smart content collaboration and governance tool that can provide real-time analysis of all the content within an organization and present useful insights and suggestions to help administrators protect against potential data breaches. Rather than a more traditional, hardware based solution to data security, Egnyte Protect is purely digital, so requires no investment in cyber security equipment. It is the first piece of software of it’s kind and could potentially revolutionize how we look at data security.
Whilst some data breaches are due to hackers, research has found that around 80 percent of all data breaches occur because of employee negligence or error. As companies grow it can be difficult to put cyber security at the forefront of company policy, but it is critical for the security of a firm’s data to be one of the highest priorities.
Egnyte Protect continuously analyzes the entire content environment and picks out the most sensitive information, such as credit card or social security numbers. The ability to identify Vulnerabilities in real-time, alert administrators, and remedies to any issues, is a key part of what makes this product the first of it’s kind.
“As organizations are transforming their digital workplace and rapidly growing their content, we identified an urgent need for a governance solution that could provide protection across a wide range of apps and repositories,” CEO Vineet Jain and CloudTweaks contributor commented upon launch, “With Egnyte Protect we took a new approach, building a cloud-based solution that can be easily deployed and create value for organizations within minutes, versus the traditional approach which typically involved deploying additional hardware and incurring professional services costs.”
Prior to it’s full commercial release the service has been utilized by Buzzfeed. Jason Reich, director of global security at BuzzFeed, stated that, “At BuzzFeed our teams are working on a wide range of content at a fast pace, much of which includes information that is timely and sensitive in nature… It is our top priority to protect that content, its sources, and our team without interrupting their workflow. We chose to deploy Egnyte Protect because it actively monitors our content from the inside out, checking for potential issues twenty-four seven, and allowing us to rest assured knowing our content is properly protected at all times while our employees work freely.”
So Egnyte Protect has already been trialed by one of the biggest sites on the internet, a ringing endorsement for any cyber security firm. We shall have to wait to see if this is truly a revolutionary moment for cyber security.
By Josh Hamilton





