Roughly one third of enterprises in North America experience troubles maintaining their cloud security due to the fast progress in cloud technologies and the complex nature of the cloud, a report by Threat Stack and the Enterprise Strategy Group reads. Other challenges include growing number and complexity of regulations, which prevents new business endeavors and slows down the pace of growth of current business operations in the cloud. Nonetheless, containerization is on the rise and hybrid environments gain popularity.
One of the greatest concerns of North American businesses is the visibility of their cloud workloads. Close to two thirds, or 62 percent, want more visibility into cloud workloads, which is getting more and more difficult provided that 28 percent of businesses will run a hybrid cloud solution within a year. According to the survey, one fifth of businesses plan to run workloads on five different cloud Service Providers.
Only one in four enterprises is relying on native security controls provided by a cloud vendor, though. Some 54 percent of respondents use a combination of third-party and native controls while 53 percent consider production database server as the most critical type of cloud workload they must secure.
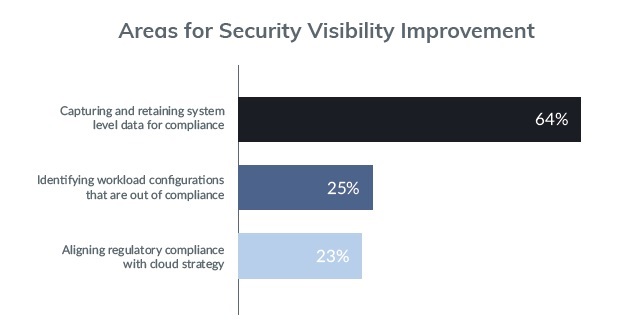
(Image Source: Threat Stack and the Enterprise Strategy Group)
Other security challenges before businesses running cloud operations is the inability of security tools to prevent misconfiguration and software Vulnerabilities. While the latter will not be fixed any time soon, cloud providers can think of better misconfiguration controls and automated protection. This is in line with respondents’ statement that security tools are unable to perform key tasks such as automation through integration of DevOps tools.
Furthermore, security tools are unable to secure visibility into system-level activity, enterprises complain. This is an alarming finding given that 31 percent of businesses cannot cope with the rapid pace of cloud developments, which means the above issues could only worsen in the next years.
More than half of businesses in North America are of opinion that security and compliance requirements slow down the sales process and their overall sales cycle. While 31 percent of all investment in cloud security is forced by the need to meet external compliance requirements, 59 percent of business say their sales process is slowing down because of such requirements and 57 percent complain about sales cycle delays.
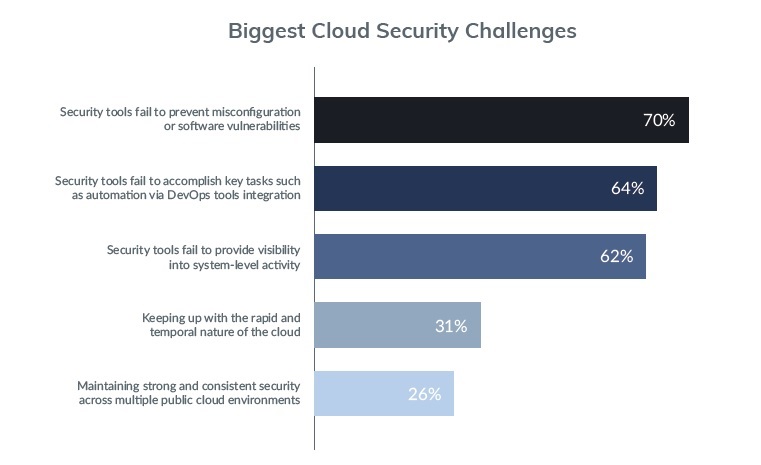
Security compliance is obviously the major driving force behind investment in cloud security. Nonetheless, 26 percent of businesses surveyed say they experience difficulties achieving the required visibility to identify misconfigurations. This translates into failure to meet compliance requirements, which slows down further their overall business development.
Another key finding is that some 42 percent of enterprises have already adopted containerized product applications, which in turn poses further cloud security risks. Containers introduce further layer of security and compliance issues provided that additional 23 percent of businesses are to deploy containerization over the next 12 months. Use of containers will double in the next 12 months with further 22 percent of enterprises beginning to test containers during the period.
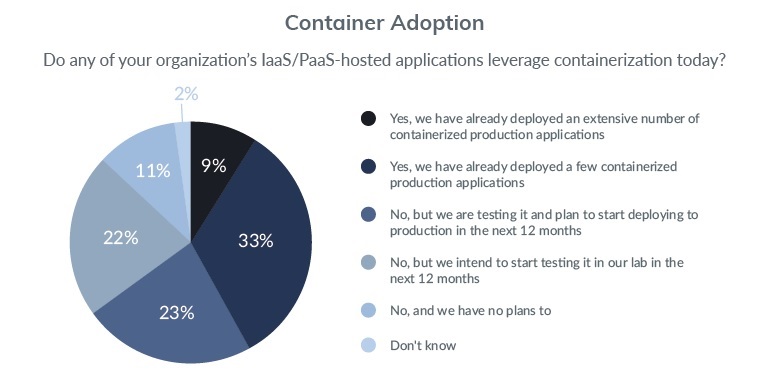
Approximately one third of businesses express concerns over the lack of access to viable security solutions for containers and another one third is worried their current cybersecurity solution does not cover containers. Actually, containers represent the single most important security challenge bearing in mind that market penetration will reach about 90 percent as early as next year.
Thus, enterprises need to adopt an integrated security strategy instead of seeking multi point solutions or taking fragmented approach toward cloud security. Implementation of comprehensive intrusion detection platforms is another viable method to cope with the security challenges posed by cloud complexity, compliance, and increasing adoption of containers.
By Kiril V. Kirilov





