Microsoft Office 365 is a popular platform for individuals and organizations alike. But, recent research shows many organizations are apparently too dependent on Office 365 by using it as a backup service.
More specifically, a study polling more than 1,000 IT professionals, backup administrators or business executives, revealed that 40 percent of respondents didn’t have third-party backup services to secure their Office 365 data. That’s particularly worrisome considering 62 percent of people in the study said they use office 365 currently and 6 percent plan to in the next year.
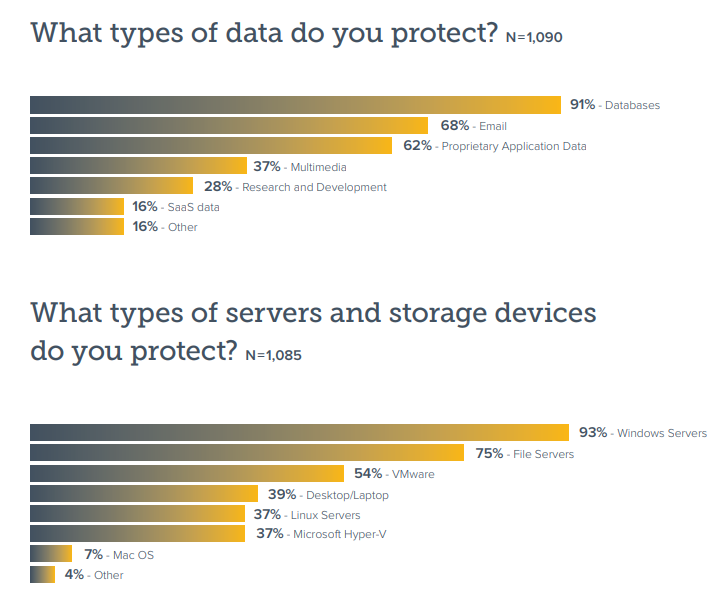
Most respondents said they use Office 365 for email, but OneDrive, OneNote and Teams were also among the services businesses used.
Regarding the 40 percent not using third-party backup services, perhaps they don’t realize that the way Microsoft 365 treats content falls far short of what an actual backup service would do to give protection.
Microsoft has a resilient software-as-a-service (SaaS) infrastructure to ensure users can access data when needed. However, the service-level agreement (SLA) does not protect information against issues including malicious intent, user error or any other activity that could destroy data.
The report from Barracuda also stressed that Microsoft 365 also likely does not meet organizational policies for handling data. As a start, it does not retain deleted data for very long or in a safe way. If a person deletes an email, it only goes to the recycle bin for a maximum of 93 days before Microsoft gets rid of it.
Within that relatively short window, an individual could realize the mistake of deleting the email and restore it. But, with SharePoint and OneDrive data, it’s not so straightforward or simple. Microsoft only keeps information related to those two services for 14 days.
And, if someone needs to retrieve it, their organization has to open a support ticket with Microsoft. Moreover, it’s not possible to recover a single deleted SharePoint or OneDrive file. Instead, the best Microsoft can do is restore an entire Instance. Using Microsoft 365 as a backup solution is problematic both because of how data stored by Microsoft gets deleted quickly and that restoring data when needed is a cumbersome task.
Even though the Barracuda study showed that most companies do backup their Microsoft 365 data to the cloud, it’s cause for concern that 40 percent do not. Interestingly, the research also showed that across all businesses in the study, 36 percent do not use cloud backup services for any data collected by the respective entity.
The report does not analyze the possible reasons for that finding, but the study at large highlights how no matter which methods companies use to back up their data, they must ensure that the steps they take align with what the organization needs, and that people at the enterprise do not have incorrect assumptions about how Microsoft treats deleted data.
Microsoft offers a top ten style list of things clients can do to keep their data secure. It’s worthwhile to go through the tips and implement them, but company leaders also need to assess the methods they use to back up data — whether on-site or in the cloud — and determine if the plans in place cater to the organization’s current and future requirements.
Leading cloud providers have tools intended to help clients manage data from Microsoft 365 and similar apps. By using those, companies retain more control over their data and avoid catastrophic losses.
Training a company’s employees to recognize potential attempts to compromise data is also crucial. The Avanan 2019 Global Phish Report examined more than 55.5 million emails, most of them associated with the Microsoft 365 platform. The report discovered that one in every 99 emails is a phishing email.
Additionally, 25 percent of phishing emails sent to Microsoft 365 accounts bypassed the Microsoft Exchange Online Protection (EOP) built-in security feature. The EOP marked the messages as clean even though they were phishing attempts.
That finding emphasizes why although using a spam screener tool is a smart preliminary step, it should not replace training that helps workers spot the warning signs of phishing. That type of email attack is certainly not the only risk that could cause Microsoft 365 users to lose data, but it’s something that should factor into overall Microsoft 365 vulnerability awareness.
The content here should serve as a strong reminder of why companies need to back up their app data to the cloud. It’s not adequate to rely on whatever an app provider does on the back end to keep data on its servers.
By Kayla Matthews





