Cyberattacks and information breaches are happening every day, from influencing the outcomes of elections to bringing down businesses to massive data breaches of personal information. In fact, every 39 seconds a company in the U.S. is hacked and one in three people are affected.
And the activity is only growing.
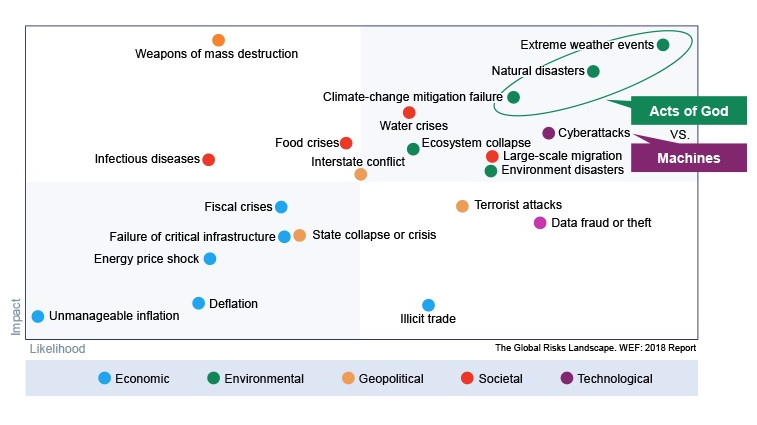
Each year, the World Economic Forum releases its Global Risks Report to identify and analyze the most pressing risks that the world faces. In the 2018 report, those surveyed were most concerned about environmental and cyberthreats over the next decade, along with geopolitical tensions. In their view, future risk will be created by either “Acts of God” or machines.
A Zero-Trust Environment
From stolen Intellectual Property (IP) to personal accounts being compromised to ransomware WannaCry, businesses must navigate a zero-trust world. Operating in increasingly litigious environments, organizations in all industries will need to continue to architect their systems and the data they collect in secure and compliant ways to protect themselves and maintain competitive advantage.
A telecommunications company was breached by a nation-state when hackers stole the company’s design documents. The company ultimately went out of business, in part because the stolen documents were shared with a key competitor. This is an example of cyber-espionage, with an attack originating from competitors or nation-states trying to steal business plans, trade secrets or IP — and it could happen to any company.
Malware is another example of a cyberbreach. A state-owned oil company was attacked through a phishing email scam that infected tens of thousands of workstations. As much as 75% of the infrastructure in the company was affected and it shut the company down for two months.
Not only are companies in danger, people’s lives can be at risk. WannaCry, the biggest ransomware attack in history, infected 300,000 computers across more than 150 countries. WannaCry’s impact was particularly pronounced at hospitals in the U.K., where more than 19,000 appointments were cancelled and computers at 600 emergency departments were locked down.
But not all breaches are a result of cyber-espionage or hacking. Many are inadvertent results of insider privilege and misuse. There have been many examples over the past decade of these types of cyberbreaches, where personal credentials and sometimes money are stolen. The Intelligent and Connected Enterprise will have to be vigilant against the creative, clever and targeted arsenal of hackers today or risk having its business disrupted.
Technologies like AI will make cyberthreats more targeted and creative. Take image recognition, for example, used for identity theft. Over the past five years, AI has improved from correctly categorizing images with 70% accuracy to 98% (near perfect categorization), which exceeds the human benchmark of 95%.
From the bad, there is the downright strange.
Our social media data determines our social status, or at least a portion of it. What happens when your social data can no longer be trusted as an accurate representation of yourself as a “good citizen” in society?
In Shanghai, for example, a government-backed company has legally collected data on every citizen. Honest Shanghai, a rating app for citizens in Shanghai, is one of many social credit systems run by local governments. It is part of China’s goal to establish a nationwide social credit system by 2020.
Scores are very good, good, or bad. Those with a very good score enjoy more Government services or perks, like discounted flights or lower interest rates for loans.
I, for one, am skeptical. If the government is watching everyone else, who is watching the government?
And on a stranger note, to illustrate how data can truly be manipulated by technology, researchers from the University of Washington perfected a facial recognition algorithm and a mouth movement algorithm to model how someone speaks. These AI deepfakes are now as simple as typing whatever you want your subject to say.
In another example, Emma Gonzalez, Parkland shooting survivor, fell victim to the same kind of media manipulation when fake news published a tampered image of her tearing up the U.S. Constitution on social media sites. Single tweets have the power to wipe out billions in capitalized worth. The Intelligent and Connected Enterprise will look beyond protecting the systems in its control to monitoring its presence in the wider, online (social) community.
In this era of fake news, what are your thoughts on AI applications that manipulate (like deepfakes)? In what ways can technology like this help the enterprise?
By Mark Barrenechea





