There’s no doubt on-premises deployments of mission-critical business applications provide more control over data as it resides within the four walls of an organization’s network infrastructure. However, businesses can no longer ignore the benefits of moving these applications to the cloud, including cost savings, scalability, flexibility, and modernization.
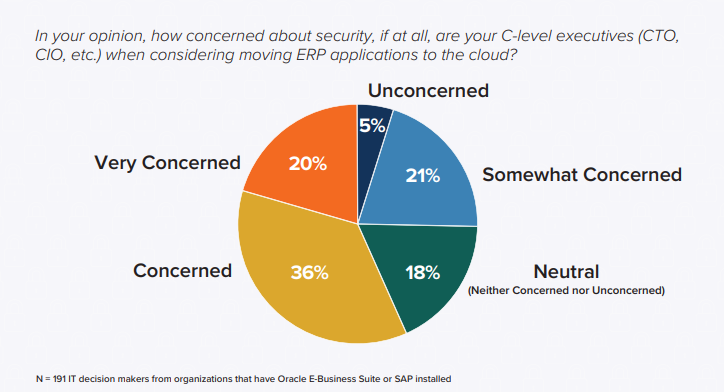
Unlike other tools that businesses use, mission-critical business applications, such as ERP, CRM, PLM, HCM, SCM, and BI, perform incredibly complex and integrated functions that keep businesses running, making the business heavily dependent on these applications. As IT teams move these essential functions and their associated sensitive data to the cloud, it’s understandable they start to feel concerns about security and compliance.
Before an enterprise makes any decisions, it’s essential to consider the top security and compliance measures that will keep applications protected and up to regulatory standards before, during, and after migration. These seven areas are great building blocks for conversations with both SaaS and IaaS cloud service providers (CSPs), mission-critical application vendors and businesses providing security technologies.
1. Data Residency and Compliance
From customer and financial information to human resources and intellectual property data, mission-critical applications house vast amounts of sensitive information. Top-of-mind regulations, such as GDPR and SOX, can dictate where the data is stored, how privacy needs to be guaranteed, and when reports and controls are due.
When choosing an application vendor or cloud service provider, compliance is paramount. But sometimes the burden of proof can fall on the business. If CSPs and application vendors can’t support the extent of your business needs, consider choosing a solution that helps automate audit tasks and addresses potential red flags. This visibility and automation can help address issues faster and continuously adhere to key regulatory standards year-round.
2. User Provisioning, Authorization, and Single Sign-On
Understanding who has what capabilities within the application is one of the biggest issues to address during and after cloud migration. Without this knowledge, employees can inadvertently cause serious security and compliance issues by exposing or sharing sensitive information they shouldn’t have access to in the first place. They also open the potential for bad actors to spoof worker logins and tap into a vast amount of critical data.
This area encompasses the management of access and critical authorizations, ensuring segregation of duties is properly enforced and other controls around user authentication, access, and authorization. For business applications, this is closer to the traditional approach to security and equally important to ensure the system is reliable to the business.
3. User Activity and Access Monitoring
Does an entry-level employee usually generate customer reports? Can a contractor always share sales data? Without understanding what baseline activity looks like within their mission-critical applications, organizations will be unable to recognize anomalous activity when it occurs.
User activity and access monitoring functionality provide visibility to help detect abnormal and malicious behavior. If you’re working with an IaaS or SaaS model, you might require customized solutions, but the need for greater visibility into your application is still the same.
4. Vulnerability Management
With a SaaS model, organizations shift patch accountability to the SaaS provider. In an IaaS model, businesses can outsource some patching to the CSP, but that generally doesn’t include patching your mission-critical applications. When it comes down to it, protection should always be a priority for the business.
Additionally, irrespective of the cloud service model (SaaS, PaaS, IaaS), organizations must also assess for security vulnerabilities in the customizations and extensions of their business applications, as those are developed by humans and may contain security vulnerabilities.
Organizations should also work collaboratively to ensure systems are up-to-date with security patches. But because security teams have trouble keeping up with patch management due to the sheer volume of updates, technology vendors can provide tools that aggregate and prioritize patches based on the vulnerability level and risk for the specific business.
5. Disaster Recovery Planning
One of the most significant benefits of moving to the cloud is that uptime responsibility is shifted to the CSP. As a business, it’s now their job to keep the mission-critical applications up and running.
However, it’s still important to understand the CSP’s plan should something go wrong. It’s also important to understand what the program is internally should there be unexpected downtime within an area of your business’s key functions.
Cloud deployments and hybrid deployments provide flexibility to incorporate better disaster recovery strategies, but that should be accounted for at the solution design phase – understanding that business applications are critical for success, and should operate with resiliency from the start.
6. Due Diligence and Service Level Agreement
Understanding and validating compliance can be difficult. Some mission-critical business application vendors and CSPs provide standards they adhere to, while others can be difficult to understand.
Companies moving to the cloud need to ask fundamental questions about the service level agreement between all the parties involved in the migration to understand potential risks. Once all the information is obtained, a risk management approach should be taken to examine the benefits against the potential pitfalls.
Finally, the most important concept to incorporate into due diligence is the approach of “trust but verify.” Even in the cases that the CSP is responsible for security controls and security-related operations, the customer is ultimately responsible for the data itself. It is key to validate that the security controls are correctly implemented. This should be checked periodically.
7. Incident Response
Since business-critical applications not only hold the most sensitive information a business has but are also the key driver in keeping the organization running, hackers are increasingly homing in on vulnerable modules for attacks.
With recent IDC data showing 64% of ERP deployments have been breached in the last 24 months, businesses need to be ready for an incident. This readiness starts with a response plan in place but should include the proper tools to identify, secure, and remediate the vulnerability when a breach occurs.
These seven points should be considered when migrating mission-critical business applications, , to the cloud. Discuss these with CSPs and application vendors and when gaps arise, search for purpose-build security tools that help deliver the increased level of protection that is needed in the cloud.
Finally, reports, guidelines, and checklists from leading independent workgroups, like the Cloud Security Alliance, can help businesses prepare as they begin the complicated journey of cloud migrations. While the journey needs careful and thoughtful planning, cloud migrations open up vast cost savings, flexibility and business continuity benefits.
By Juan Pablo Perez Etchegoyen





