Digital Service Providers (DSPs) today are well placed to take advantage of next-generation technologies like Robotic Process Automation (RPA), Machine Learning, and Artificial Intelligence. As most of the smart DSPs have already implemented RPA and have been using it for a while now, they consider RPA as a one-time solution and do not look further to improve the automation potential and straight-through processing (STP) rate. The estimated STP rate in any DSP’s process is 75-85%. However, the actual realization is 30-50% due to increasing fallouts in the automation process.
As per Deloitte’s ‘Untapped advantage in your digital workforce’ report, the strategic priority of the DSPs’ operation is to focus on continuous improvement. To improve the STP rate, they are exploring various improvement techniques like occasional and analytics-driven continuous improvement, but these methods are found to be ineffective to achieve the expected rate. Based on our engagements with various DSPs, the key factors for fallouts that impact the STP are listed below.
Hence it is suggested to focus on an efficient continuous improvement strategy that could assist in identifying the automation inefficiencies, root causes of fallouts, and tracking of STP rate – all in an automated way. This article further elaborates on the strategy that can be adopted by the DSPs to move beyond RPA and greatly improve the STP rate. The three-step process that can help DSPs to reap more value from the existing RPA implementation and reduce fallouts is detailed below.
The initial steps to improve the STP rate includes smart identification of possible causes behind the fallouts and investigation of the exception path to discover inefficiencies. To derive the possible causes for fallouts, it is suggested to perform an intelligent root cause analysis that involves the extraction of transactional and performance logs from the bot. This can be carried out efficiently with the help of the process mining tools. The analysis should also be capable of automatically identifying the major fallout reasons, with further drill-down options to showcase the root cause of each fallout and where the fallouts are happening.
Once the fallouts are identified, it is essential to handle them in a smarter way. There are different reasons for fallouts, out of which the top two sample scenarios and approaches for efficient handling are provided below.
Scenario 1: Fallouts triggered due to missing or invalid inputs
Each attended RPA bot comes with a license and DSPs could not utilize the bot to its full capacity, till the time it is stuck at one transaction. Attended bots also interrupt the automation process allowing the human to intercede and make decisions. Hence, in the event of a missing input field, interactive bot solutions can be leveraged to improve the collaboration between the human and digital workforce. This increases the STP rate by turning the attended fallout scenarios into unattended scenarios.
An interactive bot solution with a human-in-loop approach can help the DSPs to create dynamic web forms in real-time using a “no-code” RPA solution. It can also help in marking the process as suspended, and the suspended task resumes in any available bot and completes the processing rather than waiting for human intervention.
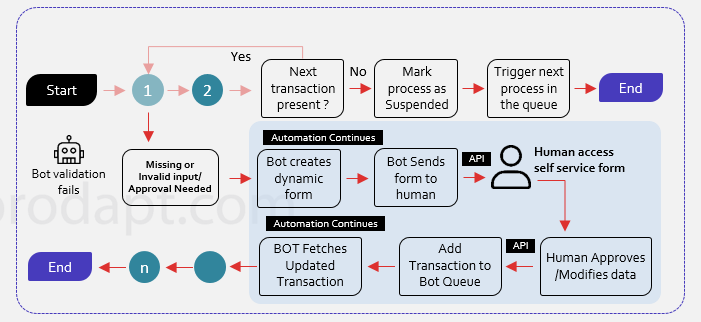
“Interactive Bot Solution with Human-in-loop approach helps to reduce the fallout handling time by 50%”
Scenario 2: Fallouts due to handwritten text and poor resolution images
Standard Optical Character Recognition (OCR) based approach possesses a serious challenge in extracting the handwritten and printed text with different font sizes and languages. This results in a high number of fallouts and the entire transaction end up being processed manually, which drastically impacts the STP rate. Hence it is recommended to integrate the RPA solution with Computer Vision, which can help in automatic processing of handwritten text and poor resolution images.
Recommendations to enhance RPA solution with Computer Vision (CV)
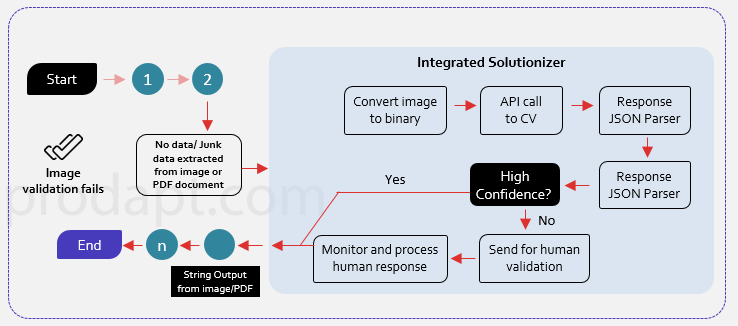
“Integrating Computer Vision (CV) with RPA reduces the development effort drastically, by using a plug and play component”
Even after achieving the desired STP rate, monitoring of the STP rate is recommended to mitigate the process changes and seasonal issues. The STP rate can be improved with the help of a continuous monitoring tool, which helps in validating the milestones and fallout percentage. Automated alert notification can be triggered from the tool to the process owners when the fallout percentage exceeds the provided limit. Also, it is suggested to define the objectives of each KPI, and continuously track the progress over time.
By leveraging the three-step process explained in this article, DSPs can set up the stage for continuous improvement in the automated process. Thus, broadening the scope of process automation enables the DSPs to achieve continuous improvement, before embarking on the next phase of the RPA automation journey and helps to accelerate the STP Rate by up to 82%
By Rajesh Khanna





