Fintech Cybercrime Report 2017
ThreatMetrix has released its latest quarterly cybercrime report based on cybercrime attacks from October to December 2016, detailing trends across financial services and eCommerce, with a global study of traffic patterns and emerging threats.
Financial Services Key Trends
- FFIEC mobile banking payment and guidance is forcing US financial institutions to better manage risk, while PSD2 has European financial service providers agitated. Furthermore, insider threats are notorious in many prominent financial service breaches.
- Mobile usage for banking login and transacting is increasing rapidly with 55% of financial services transactions coming from mobile devices.
- 80 million attacks were detected using stolen or fake credentials.
- A 250% growth of financial service mobile transactions was noted year-on-year.
- Banks are embracing mobile growth, and 55% of financial services transactions are mobile; Many banks are offering full-service apps, however, rejection rates for transactions are high.
eCommerce Key Trends for 2016

- A higher volume of cross-border transactions is noted with the global village economy gaining strength and popularity. A severe disadvantage is an increase in online fraud.
- With a 51% increase in transactions blocked year-on-year and twice as many transactions rejected as processed, systems are working overtime to protect users from threats.
- Up to 90% of some retailers’ traffic is attributed to Bot attacks.
- 75 million transactions were rejected this quarter with rejections of 11% of account creations, 6.4% of account logins, and 5.1% of payments.
The Threat Landscape
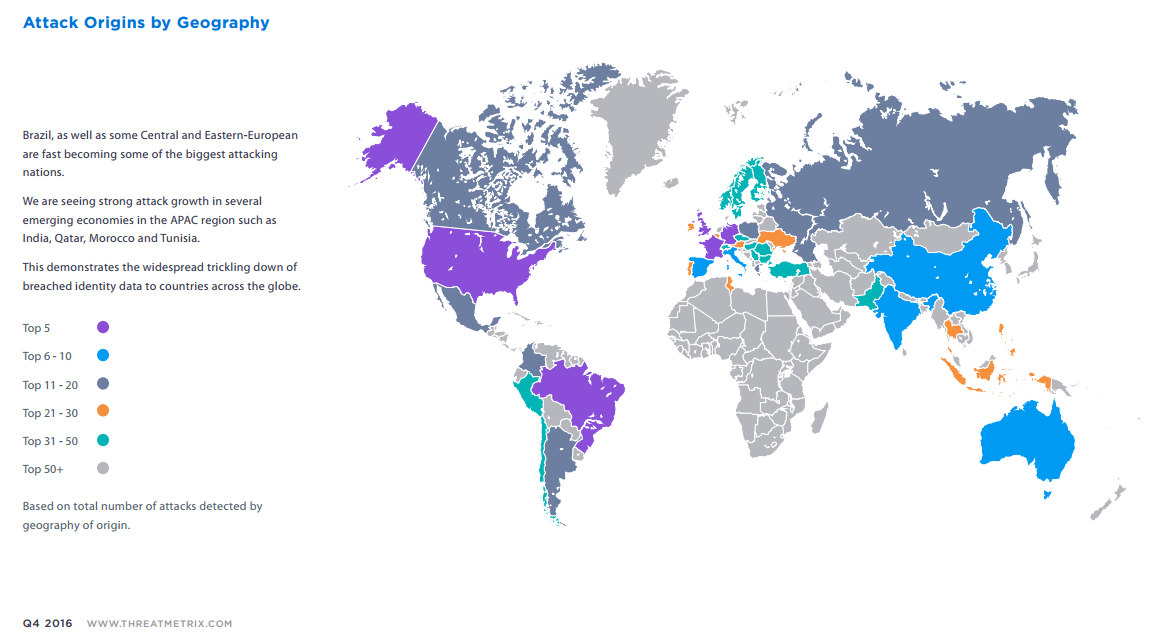
- The US, UK, Germany, France and Brazil feature in the top five attacking nations, but emerging economies such as India, Qatar, Morocco, and Tunisia are showing strong attack growth too.
- Strong attacking economies tend to attack similar economies.
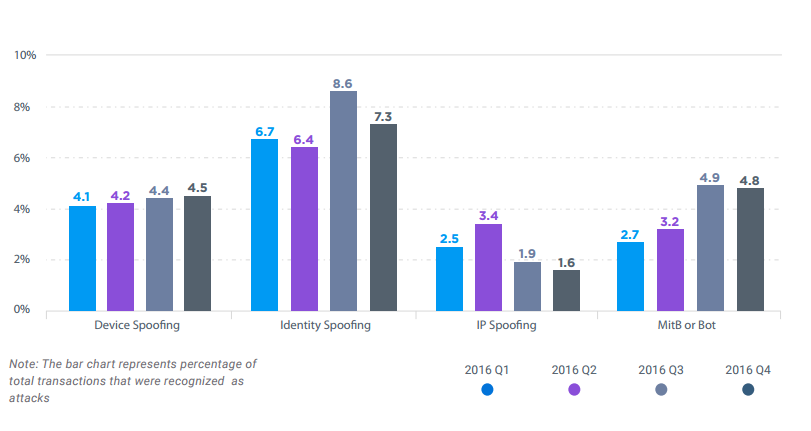
- In the last quarter, identity spoofing persisted in FinTech with a slow but steady growth in device spoofing and a slight decline in IP spoofing and Bots.
- Digital mobility of global connected users increased with a quarter of transactions cross-border.
- Device spoofing remains a top threat.
- Mobile transaction grew globally by 130% year-on-year with highlights in both developing and developed countries.
Keeping the digital world safe and secure is an increasingly difficult job; security experts are relying on holistic approaches to digital identities to differentiate fraudsters from legitimate customers, and pulling in innovative applications of behavioral analytics and Machine Learning to better identify high-risk behavior.
By Jennifer Klostermann








