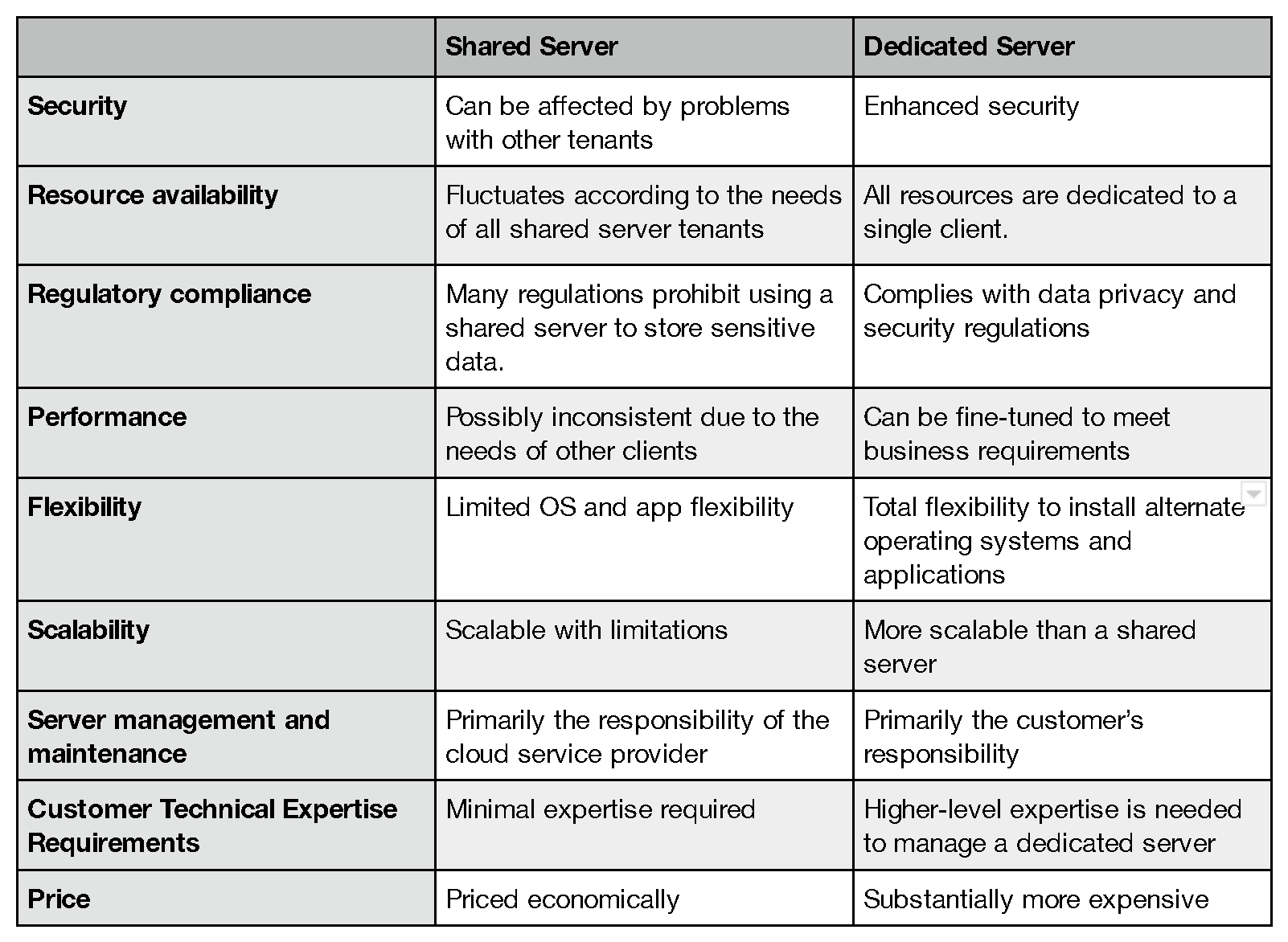
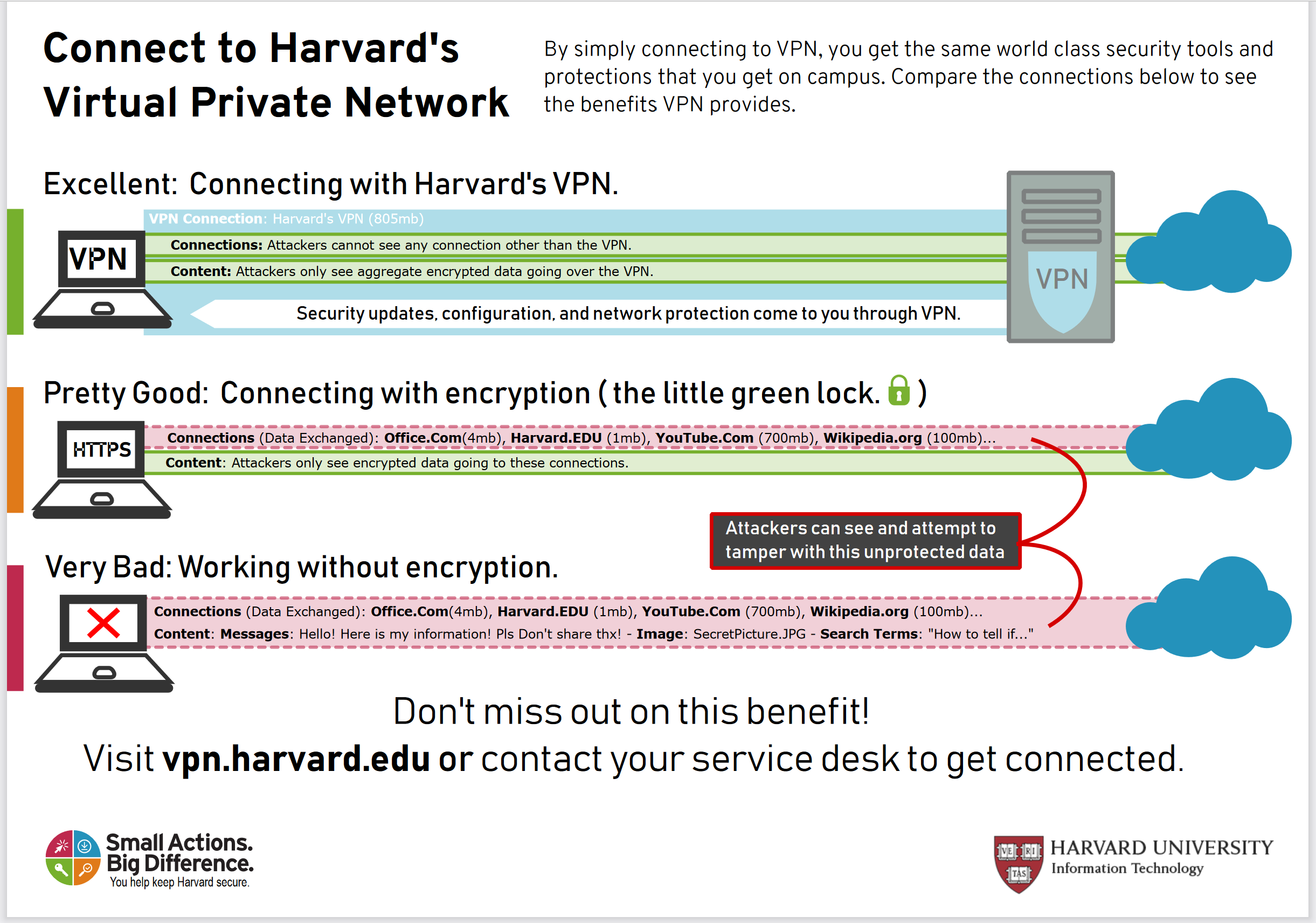
Useful Cloud Security Tools For Your Business
Cloud Security Tools Cloud providing vendors need to embed cloud security tools within their infrastructure. They should not emphasize keeping high uptime at the expense of security. Cloud computing has [...]