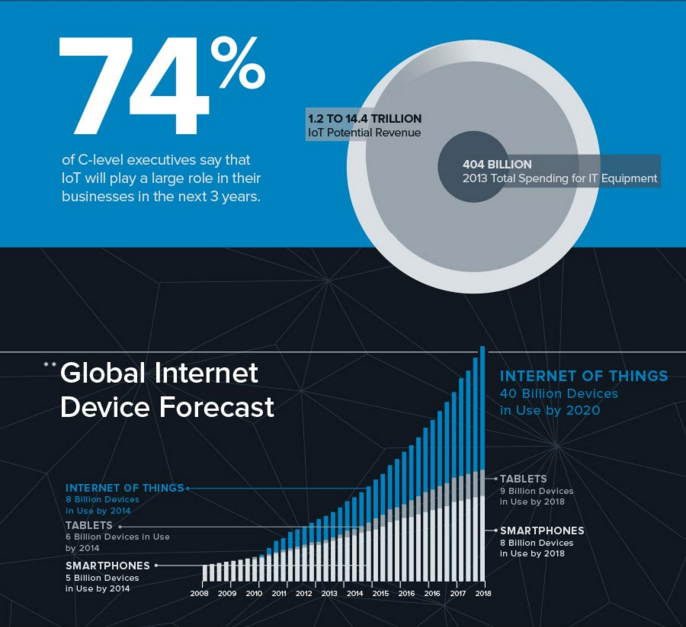
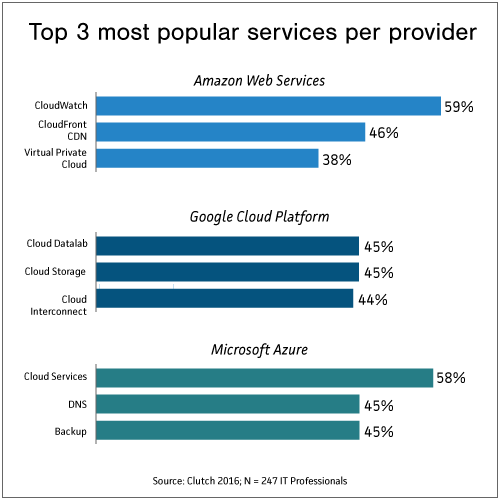
The Everlasting Cybersecurity Conundrum
Cybersecurity Conundrum Technologies put forward that attempt to block and ensnare cyber-criminals and the more infamous advances of said cyber-criminals searching for new loopholes and implementing fresh attacks. Unfortunately, just as [...]