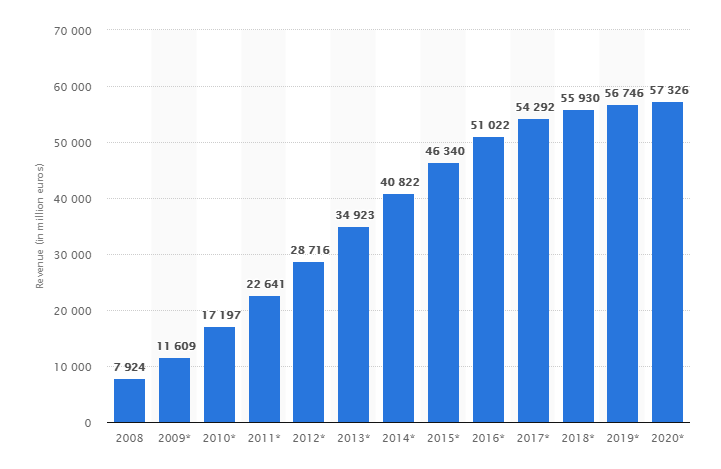
How Will AI and Automation Change the Global Economy?
The Future of AI and Automation Artificial intelligence (AI) and the automation it enables will significantly disrupt the global economy. Some people fear robots will replace most of the jobs [...]