The ability of cloud computing in processing, transmitting, and storing data makes it increasingly significant in the delivery of public and private services. Cloud computing as a disruptive technology with major implications for markets, economies and societies is becoming increasingly important for countries at all levels of development. However, the level of cloud adoption for organizations in developing countries looks very different from those in developed countries.
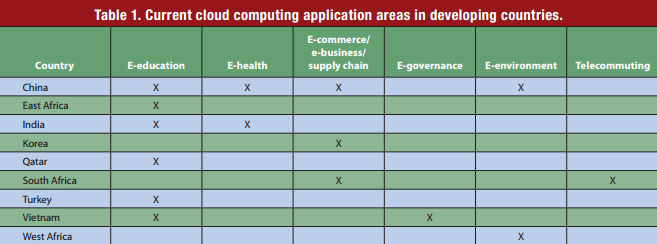
According to Kshetri’s report (2010), “the market for the cloud in developing countries is small but expanding rapidly”. Developing countries are attractive markets for cloud services and this technology has applications in a wide range of areas, including E-education, E-health, E-commerce, E-business, and supply chain. In reality, there are very few companies in developing countries which are actually using cloud computing. It would seem that cloud computing in developing countries is in its early stages.
(Image Source: IEEE Computer Society)
Many scholars believe that cloud computing has the potential to offer users in developing countries access to unique resources of computing power and storage. It is clear that the adoption of cloud computing is of great significance for businesses and organizations. Cost savings in hardware, software and personnel, as one of the main advantages of cloud computing, are most frequently cited in the literature. Cloud service customers can pay for the use of data storage capacity and application software rather than buying the hardware and software. Furthermore, software on the cloud can be easily installed, maintained, and updated. Although companies that use of cloud facilities extensively need competent personnel to manage IT functions, obtain cloud services, and manage their relationship with cloud providers; cloud computing generally leads to lower IT staff costs.
Flexible access to processing and storage capacity is another benefit of cloud computing. In addition, a global study on 400 government executives in 10 developed and developing countries indicated that cost savings (See image), the nature of government activity, administrative advantages (e.g. easier software access, rapid deployment and reduced system administration) are the most significant advantages of cloud adoption.
Recent studies in developing countries indicate that cloud adoption in these countries is low and majority of developing countries encounter significant obstacles to participate effectively in the cloud economy. Barriers affecting cloud adoption in developing countries differ significantly depending on a country’s level of development and business and communications environments. These barriers can be divided into two main categories: internal and external barriers. Attitudes towards cloud computing, concerns and anxieties among managers about data privacy and security in the cloud, the location of data and reliability of services, concerns related to the non-availability of suitable terminal devices, concerns related to the migration of data and upgradability, lack of knowledge and skills to manage cloud resources, and finally lack of awareness of what cloud computing actually involves and its implications are main internal barriers. External barriers to adoption include inadequate infrastructure (lack of reliable power and broadband connectivity), lack of adequate legal and regulatory frameworks for electronic commerce and cybersecurity, and lack of skills to make effective use of ICTs.
Like other new innovations, successful implementation of cloud computing in developing countries needs organizational change which takes time and requires new investment. Policy makers in developing countries should research and analyse the level of cloud readiness and potential implications of cloud adoption. In addition, policies should recognize the diversity of business models and services within the cloud, the diversity of customers of cloud services and the complexity of the cloud economy ecosystem. Then, an effective cloud strategy (which address the areas such as infrastructure, legal and regulatory issues, the supply side of the cloud economy ecosystem, human resources, Government cloud use and financial implications) should be designed for a successful implementation of cloud computing.
By Mojgan Afshari





