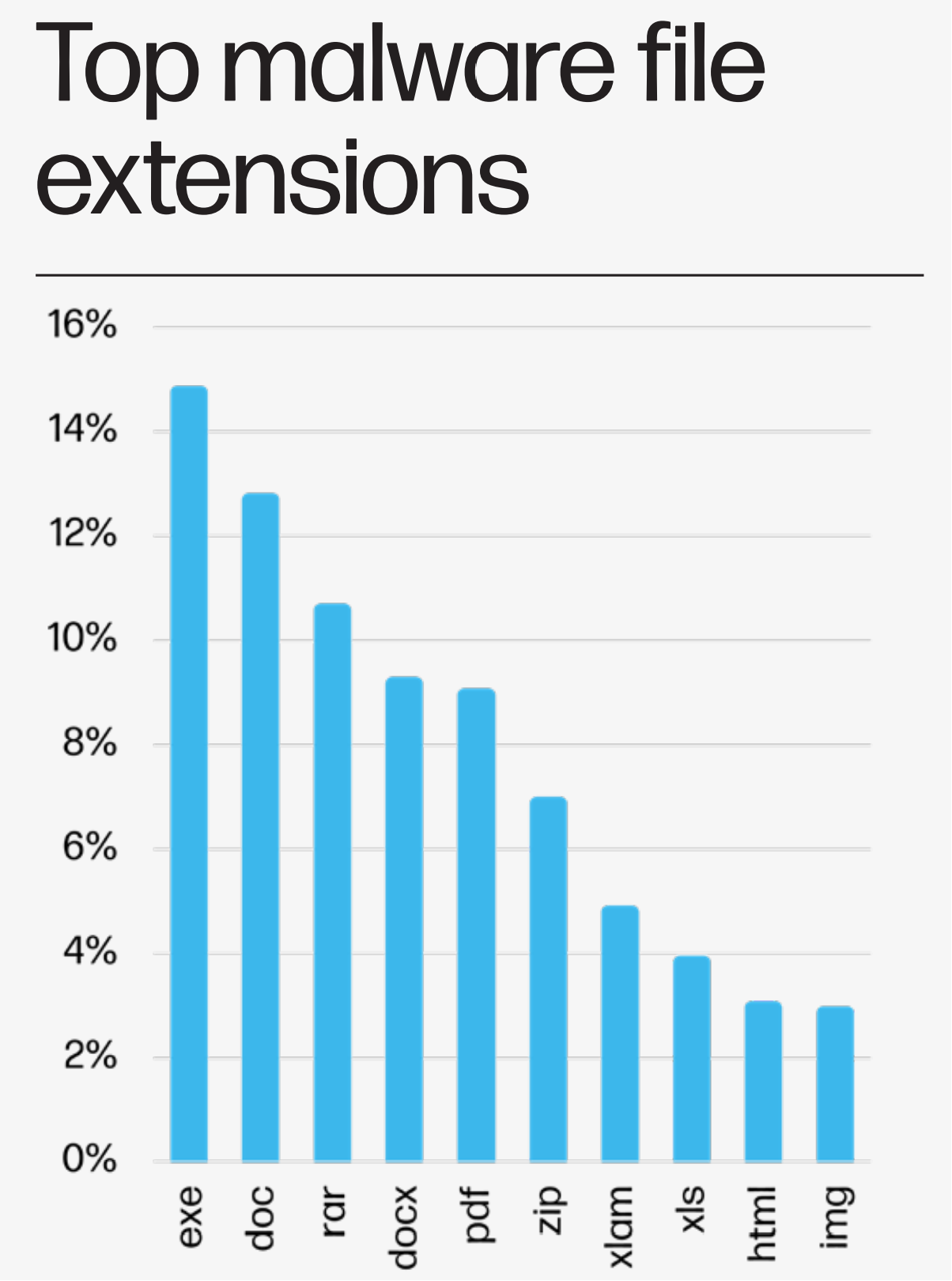
The Rise of ‘DIY Malware’: HP Highlights Growing Cyber Vulnerabilities
Cybersecurity Threats from Pre-Packaged Malware Kits In a recent analysis by HP, there’s a worrying trend in the world of cybercrime: easily accessible, pre-packaged malware kits are on the rise, [...]












