Cloud computing technology is transforming our environment, workplaces, as well as organizations by provisioning massive quantities of computing power available to even the smallest companies on a pay-as-you-go basis. The exponential adoption of cloud is a welcome change, however, like coin having two sides, the innovations that have made cloud computing possible also have a slightly darker side. As a foremost, we send e-mails, surf the Web, exchange messages and post comments to blogs, we inevitably leave a digital trail. At every stage of the communication process, no matter how many servers it passes through, established security parameters and protocols act as a watchdog, monitoring the flow of data. This, however, depends on the security tools and preferences.
Packet inspection technology is deeply embedded in firewalls also allows organizations to make security policies for personnel, limiting them in what they can and cannot do over the network, while logging pertinent information and patterns from within contents. For cloud Service Providers, service-level agreement with their customers play an important part in providing a certain level of service and at the same time enforce an acceptable use policy. This may involve making use of packet inspection to implement certain policies that cover copyright infringements, illegal materials, and unfair use of bandwidth.
(Image Source: Escotal)
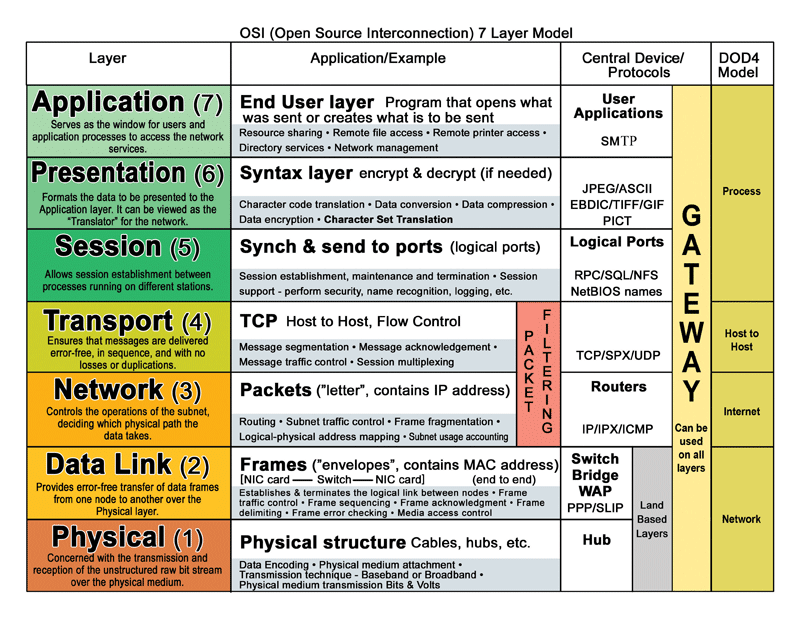
The seven layers of The Open Systems Interconnection (OSI) model; application, presentation, session, transport, network, data link, and physical act as an effort to bring software and hardware vendors along with world’s IT community on a standardized platform. In any case, before venturing into the world of packet inspection, internet protocol (IP) is used to handle routing data between the computers across a network. Essentially, IP sends data in chunks called packets, which are blocks of data that contain addressing information that lets routers and other packet switching devices keep track of information flow on the network. The main concept or purpose behind OSI reference model is to ensure that networks remain more manageable and to tackle the issue of transferring data from one computer to another. Standardization of different systems and their interconnectivity with various hardware was also one of the important objectives. Last but not the least, OSI attempts to build a generalized model for all countries around the globe to follow.
Firewalls predicated on Application-layer, for example, look deeply into network traffic, and setting different rules for network traffic with regards to specific types of data. Application firewalls were the first authentic packet inspection devices, checking the application protocols within the packets themselves, as well as probing for patterns or keywords in the data they contain. Certainly, the utilization of sizable voluminous data analytics would be an amendment on some of the systems presently utilized by corporations for data analytics purposes. As we progress into the future, the importance and usage of packet inspection in terms of software and hardware is bound to increase. The fact remains that cloud computing technology, as flexible, powerful, and automated as it may seem, is only as good as the people who utilize it—both in terms of performance and privacy.
By Syed Raza





