“Security is, I would say, our top priority because for all the exciting things you will be able to do with computers – organizing your lives, staying in touch with people, being creative – if we don’t solve these security problems, then people will hold back.” – Bill Gates
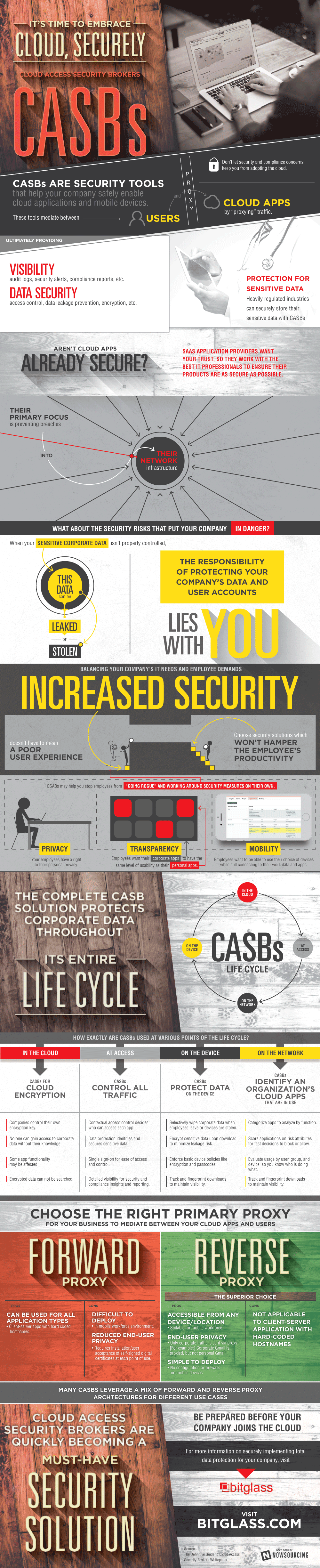
Cloud Access Security Brokers, known as CASBs, are opening a brand new window into our everyday security and safety with regard to information and high-technology trends. Increasingly, cloud-focused applications and services applied by enterprises are going to be kept much more secure with the help of CASB platforms by 2016.
Gartner Inc., has recently announced a top 10 technological advances for information security. Here they are:
1) Cloud Access Security Brokers – cloud-based points, which are used for security policy enforcement purposes, and are placed between cloud Service Providers and cloud service consumers.
2) Adaptive Access Control – a type of control with context awareness access.
3) Pervasive Sandboxing (Content Detonation) and IOC Confirmation – a great option to detect intrusions as soon as possible, and to reduce hackers’ chances to cause damage to sensitive information.
4) Endpoint Detection and Response Solutions – used to record numerous network events and endpoints, and store the information in a centralized database.
5) Big Data Security Analytics at the Heart of Next-generation Security Platforms – a fine option for storing your monitoring data to carry out retrospective analysis.
6) Machine-readable Threat Intelligence, Including Reputation Services – a form of real-time and dynamic rating to be used for the integration with intelligence feeds and external context.
7) Containment and Isolation as a Foundational Security Strategy – an excellent means to create a defense-in-depth protection for enterprise systems.
8) Software-defined Security – aims at moving the intelligence and value into software.
9) Interactive Application Security Testing – used to provide a higher level of accuracy of application security testing via the interaction of the DAST (dynamic application security testing) and SAST (static application security testing) techniques.
10) Security Gateways, Brokers and Firewalls to Deal with the Internet of Things – associated with the Internet of Things and directed towards providing security and protection for future interconnected devices, sensors and systems, which will mainly be controlled without human involvement.
Below, you can find an interesting infographic on CASBs provided by bitglass.com
By Lilit Melkonyan





