In today’s litigious society, preserving your company’s data is a must if you (and your legal team) want to avoid hefty fines for data spoliation.
But what about when you move to the cloud?
Of course, you’ve probably thought of this already. You’ll have a migration strategy in place and you’ll carefully select migration vendors to help you get there. All that remains is following the plan, right?
Everything going well, your valuable data will be migrated without a hitch and will be at your fingertips just in case legal or compliance issues arise.
But what if it doesn’t? What if, when you go to pull-up company records, your data is corrupted or not there at all?
That’s when the headache starts. Your legal team starts knocking on your door, compliance officers look to point their fingers at one of your team, and you face a hefty fine for data spoliation.
Oops.
As much as I’d like to say I’m painting a dystopian picture that has very little foothold in reality… that’s just not the case.
Just ask UBS Warburg, West and Phillip Morris.
Now, I’m not an expert on all things data migration, but I do know a thing or two about the backbone of corporate communications: email.
Seemingly innocuous, email is the kind of thing many don’t tend to think much about. You send, receive, agonize over and trash thousands of emails a year. But it’s just email right? How difficult can it be to migrate it to a new cloud service?
The truth is, it’s pretty darn difficult.
Sure, there are lots of email migration vendors out there, waving their hands in the air and jumping up and down saying: “Pick me! Pick me!” (full disclosure: I work for Fookes Software and our product Aid4Mail is right there jumping and waving with the best of them). But how many of them can you really trust?
The fact is, converting email accurately is incredibly complex and we’ve seen very few vendors actually do it well.
Here are just some of the issues we’ve seen come up with poorly converted emails, all of which could result in data spoliation sanctions:
We even have an example for you:
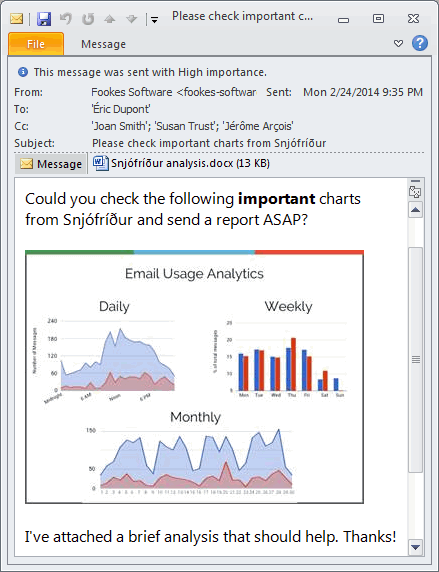
And here’s another one:
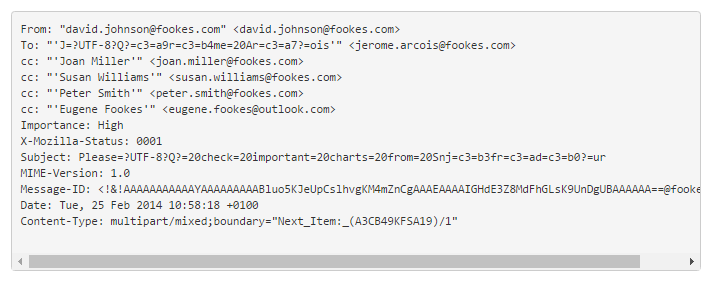
So to put this into context, let’s say you produce consumer electronics. You’ve just launched a flagship device after a few years of planning and development. Everyone’s thrilled!
BUT there’s an issue with the battery. It overheats and catches fire in certain circumstances.
A few of your customers’ houses burnt down, a couple of cars caught on fire and around 20 people suffered from burns.
One of the burn victims has leaked some inside information, and now they want to sue you for negligence. The plaintiff is saying you knew about the battery issue and chose not to do anything about so as not to jeopardize the launch.
You’re not worried, you can prove that no one knew anything about it. So, you go back into your archives to pull up all the relevant communication between the project team and your Chinese battery supplier.
That’s when you see that all the emails between the China-based purchasing manager and the battery supplier are all question marks and blank spaces.
The sent date is showing as after the received date and all the emails look like they’re unread.
This, my friends, is data spoliation. Sure it’s not your fault, but you’ll still get sanctioned.
So, what’s the moral of this cautionary tale? Test, test and test again before you choose ANY migration application to move your email to the cloud.
Taking the time now to thoroughly test the application in all scenarios before you commit will pay off in the long run.
By Katie Cullen Montgomerie
Katie is the marketing and communications manager for Fookes Software, the developers of email migration software Aid4Mail.





