Cloud adoption continues to grow, which is evident from the fact that annual 2016 revenues for cloud vendors were “within touching distance” of $150 billion. Gartner also predicts that, a corporate ‘no-cloud’ policy will be as rare by 2020 as a ‘no-Internet’ policy is today. However, a ‘’cloud-ready’ security and compliance program is the need of the hour, to manage the risks and the complexities due to cloud adoption. This will enable organizations to face cloud challenges which, according to RightScale’s 2016 State of the Cloud Report include compliance with regulations, a lack of resources and expertise, governance and control and security. Although a challenge mainstay, confidence in cloud security is nonetheless rising; SkyHigh Networks points out that 65 percent of IT leaders think the cloud is as secure, or more secure, than on-premises software.
To maximize the benefits of cloud deployments while mitigating the risks, companies need to prioritize a cohesive approach to governance, risk management and compliance (GRC). A cloud governance framework can automate cloud security, risk, and compliance workflows, enable stakeholder reporting and visibility, and ensure best practices and standards for cloud compliance.
With that in mind, here are five recommendations for ensuring a proper governance, risk and compliance framework for cloud assets and operations:
An essential first step is to understand the scope of cloud services in use within the organization and gain visibility into the whole cloud environment. IT and infrastructure managers need to have a complete picture of the processes running on cloud deployments, the underlying assets and their ownership within the organization both from an IT and business standpoint. While they may seem intuitive, alarmingly, the 1H 2016 Shadow Data Report states that organizations use 841 cloud apps on average – an astonishing 20 times more than they thought they did. Organizations also need a well-defined policy to deploy, manage and run the cloud applications and categorize the sensitivity of the data held to ensure that requisite controls are in place to manage the data.
Businesses always have the thought of losing control on application and infrastructure while deploying an application on the cloud. Assessing and creating a working relationship with the cloud provider based on a mutually agreed framework is very important. The organizations must select a cloud provider who can demonstrate validation of controls including network security, physical datacenter security as well as a standard audit framework conforming to applicable regulatory standards.
Gartner recommends that organizations need to address several key issues when selecting a cloud hosting provider, which include access privileges, regulatory compliance, data provenance, data segregation, data recovery and business continuity.
To gain a complete understanding of the CSP environment, organizations should also ensure that there is no ‘insufficient due diligence’, which Cloud Security Alliance (CSA) rates as one of the ‘notorious nine cloud computing top threats, and establish a due-diligence framework to monitor the cloud service provider performance on a continuous basis.
Organizations should understand the importance for an effective governance function within the cloud environment. The cloud assets, cloud services, business objectives, business processes, policies must be documented, along with their operational relationships. These processes and policies must be accountable, clearly assigned and consistently understood throughout the business.
Also, it is of utmost importance to establish accountability when customer information is intertwined with that of the cloud service provider. This includes logical separation of your data sets from those of the other customers / users, defining SLAs on both sides and categorizing the services consumed.
Inevitably, there are risks with cloud environments as there are with all storage and retrieval systems, both electronic and manual. Businesses must understand the cloud threat landscape, effectively evaluate and mitigate risks and protect themselves and their interested parties from exposure.
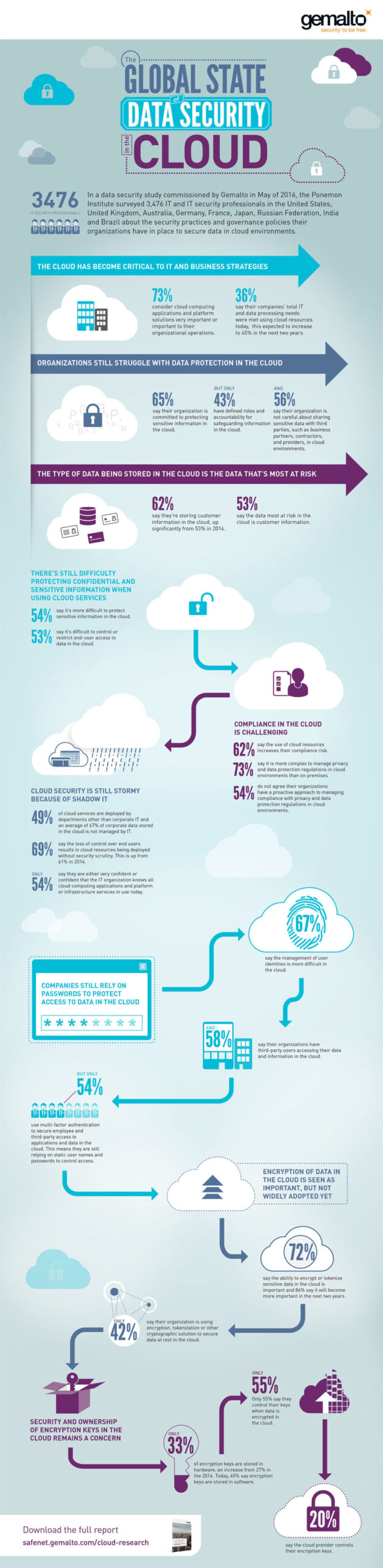
The likelihood of threats rarely lessens, but threats do change in nature and for this reason companies should be continually alert and abreast of latest developments. SkyHigh Networks revealed, in its Q4 2016 Cloud Adoption and Risk Report that the average company experiences over 23 cloud-related security incidents each month. Yet, despite this, a different study – the 2016 Global Cloud Data Security Study from Gemalto and the Ponemon Institute – discovered that 54 percent of respondents didn’t agree that their companies have a proactive approach to managing security and complying with privacy / data protection regulations for the cloud. Therefore, it is imperative that organizations prepare for security threats to the cloud before becoming a victim.
Businesses should assess cloud compliance with regard to security, privacy practices and policies. Among the most well-known risk and control frameworks are best practices is the Cloud Security Alliance (CSA)’s GRC stack, which provides a toolkit to assess private and public clouds against industry standard best practices and compliance requirements.
Others include the CSA’s ‘Treacherous Twelve’ Cloud Computing Top Threats, ISACA’s cybersecurity Threats and Controls, the National Institute for Standards and Technology (NIST)’s Framework for Improving Critical Infrastructure Cybersecurity, ISO/IEC 27017, ISO/IEC 27018 and the Center for Internet Security (CIS)’s Critical Security Controls.
Leveraging industry standards provides a level of assurance that best practices are followed both by the organization and by cloud Service Providers.
Businesses can achieve enhanced information security, compliance and risk management as well as reliability, operational control and transparency with effective implementation and extension of the GRC framework to their cloud assets and operations. Adhering to best practices and standards will deliver informed decision-making and ongoing management, placing the business in a better position to reduce risk and realize the benefits of the cloud in enhancing business performance.
By Vibhav Agarwal





