Protecting networks and the data that traverses them might seem to be an impossible task these days. Whether it’s a nation-state-sponsored infiltration that seeks to tamper with industrial systems or a criminal organization planting ransomware for profit, there are fresh horror stories of breaches every day in the media. But not all is lost: a different approach to enterprise network architecture in tandem with cloud-based security services can help increase the effectiveness of existing security practices and technology.
Security functions have historically been deployed in the enterprise datacenter. This was because enterprise IT used to be self-contained; it was separated from the outside world by a barrier of protection called the firewall. The boundaries became permeable as organizations become more connected to the internet. With the growing importance of web-facing applications and the rapid growth of mobile technologies, the last decade has seen those boundaries become ever more porous.
One approach is to spend more money on the problem. Enterprises are forecasted to increase spending on security to $81.7bn this year, an 8.2% increase over 2016 according to IDC’s Worldwide Semiannual Security Spending Guide. Security hardware and software in 2017 are expected to generate $15.2 billion in sales, while endpoint security software segment will garner $10.2 billion in revenues this year, according to IDC.
And yet in the U.S. alone, there were 1,093 data breaches in 2016, a new all-time record, according to a report released by the Identity Theft Resource Center (ITRC), a non-profit consumer organization. The increased spending doesn’t seem to correlate with greater security; researchers have offered estimates that suggest that a significant portion of security spending —sometimes upwards of 30% or more– goes wasted, with technology going unused for a variety of reasons, including not being able to integrate it with existing systems and not having enough staff to use the technology on an ongoing basis.
Threats continually evolve and seem to always be increasing in scope. A new variant of Petya ransomware infected systems across Europe in June 2017, causing trouble in organizations ranging from Danish-based shipping giant AP Moller-Maersk to health care facilities in Pittsburgh, PA in the USA. An attack of a different type, the Mirai Botnet attack used compromised DVRs, IP video cameras and other devices to target Dyn, a provider of domain name system (DNS) services, in October 2016. The distributed, denial-of-service attack (DDoS) attack affected multiple DNS servers and caused interruption of services to a number of well-known sites, such as Twitter and Amazon.
Attack traffic reaching 300Gbps or more was seen over half a dozen times in 2016, more than enough to overwhelm the DDoS defenses of a single enterprise datacenter. This means more hardware (or software) concentrated in an enterprise datacenter won’t solve the security problem.
Re-architecting the enterprise network for security
To handle the scale and scope of attacks to come, more enterprises are starting to look at building a distributed network architecture (see Figure A). In essence, this architecture is characterized by:
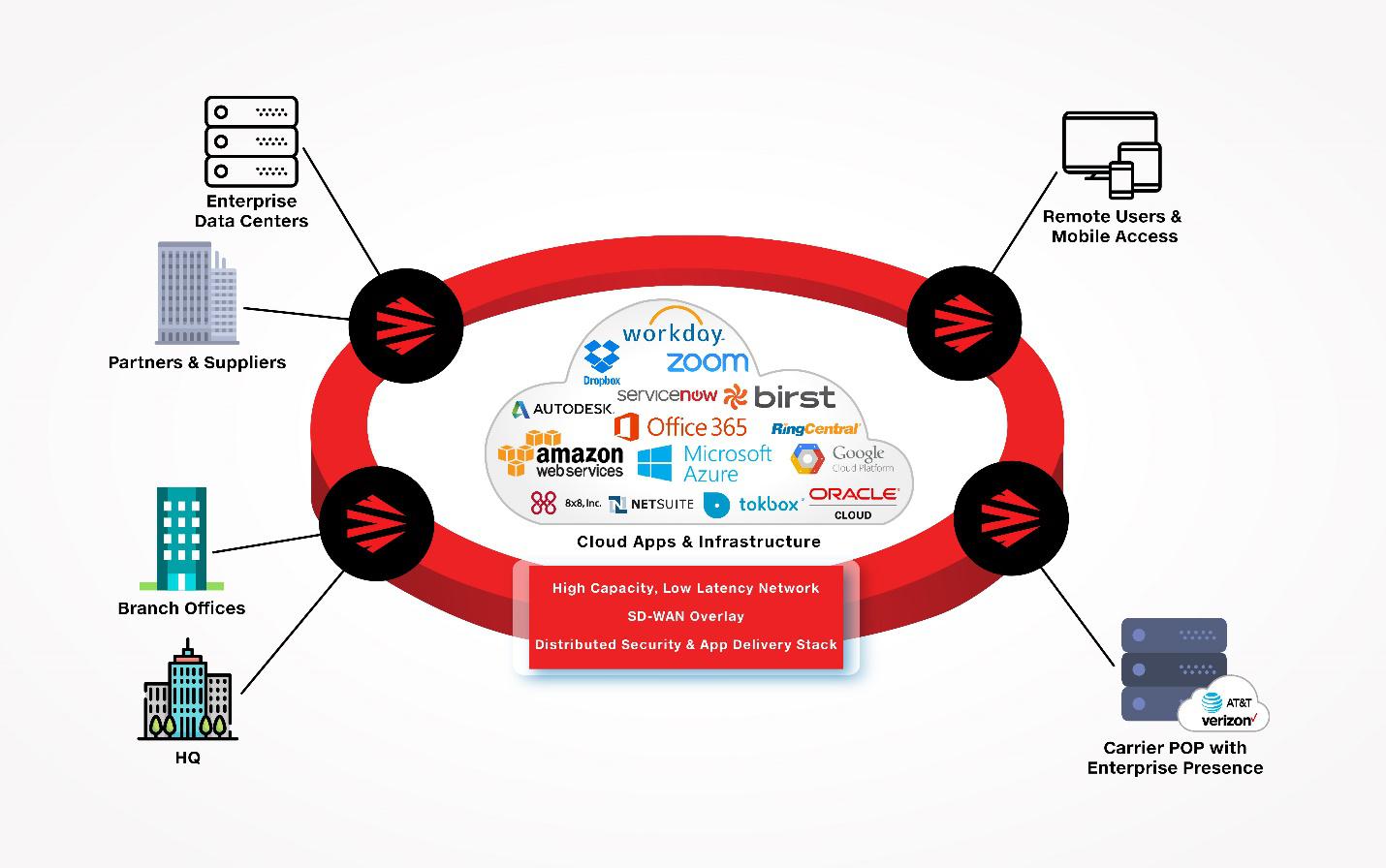
Figure A: Example of a distributed network architecture
There are a number of benefits to shifting ingress and egress traffic to the regional hubs instead of through a datacenter at the company headquarters. network security is improved by
Further enhancements to security can be gained from the distributed network architecture. How? If the enterprise has already interconnected via multi-tenant datacenters, the placement of compute and storage resources at the ‘edge’ gives an opportunity to extend security policies and process used in the enterprise datacenter closer to where users are.
The recent SANS Institute 2017 Data Protection Survey surveyed InfoSec professionals, who identified encryption of data at rest and in transit, access controls, firewall and Unified Threat Management (UTM) as the top three network related controls for data. It follows then that if the network functions are distributed as suggested above, then the security functions need to move with them.
The architecture can vary based on factors such as space and power availability and the use case as well. A large branch office might do well to have a nearby hyper=converged infrastructure (HCI) (Fig. B below left) for additional processing power to go with a layer of security functions.
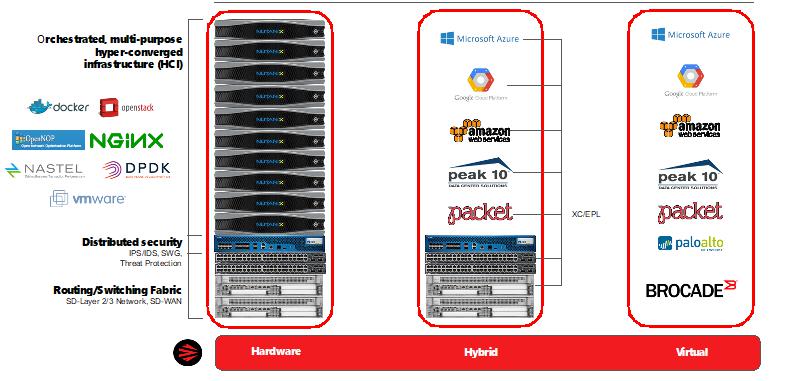
Figure B: Examples of application and security functions at distributed network nodes.
Examples of functions include (but are not limited to):
Different traffic and performance requirements might see enterprises using a mix of cloud-based services and dedicated appliances, or a fully virtual appliance approach (Fig. B above right).
Ultimately, the goal of applying a distributed network architecture increases security by enhancing the ability to follow industry best practices, while taking into account the new challenges of mobile users and distributed applications. For example, the practice of segmentation of network traffic. Being able to separate out different classes of traffic addresses needs for data protection with regulations and laws such as PCI, HIPAA, and GDPR that require separation of sensitive data.
Given that network policy enforcement becomes more challenging with growing number of endpoints-most notably mobile devices on sometimes unsecured wireless networks-doing at the network edge enables application of policy closer to the user’s first point of entry. This approach makes it more efficient to prioritize risk profiles and map those profiles to network policies. One example of this in practice might be the offloading of low-risk traffic to public internet connections before it aggregates into a big load at a central location—a location that has a high-cost MPLS for performance and security reasons. Why saturate those links with low-priority traffic? Why let that traffic mingle with more sensitive data?
There are some challenges with this model: only the largest enterprises are going to have the financial resources to invest in a global datacenter presence and staff it properly. And even for those who have the resources, will they be able to adequately cover all of the markets that they serve or have partners? The good news for the CEO and CSO is that a growing number of companies are doing the legwork for them by integrating and deploying the network and technology stack and offering it as a service.
Today’s security challenges, along with the changing nature of enterprise application development and consumption, are difficult to handle in a traditional enterprise datacenter architecture. Instead, forward-looking companies should look at how a distributed network architecture built with security services in the technology stack can help increase the effectiveness of existing security practices and technology.
By Mark Casey





