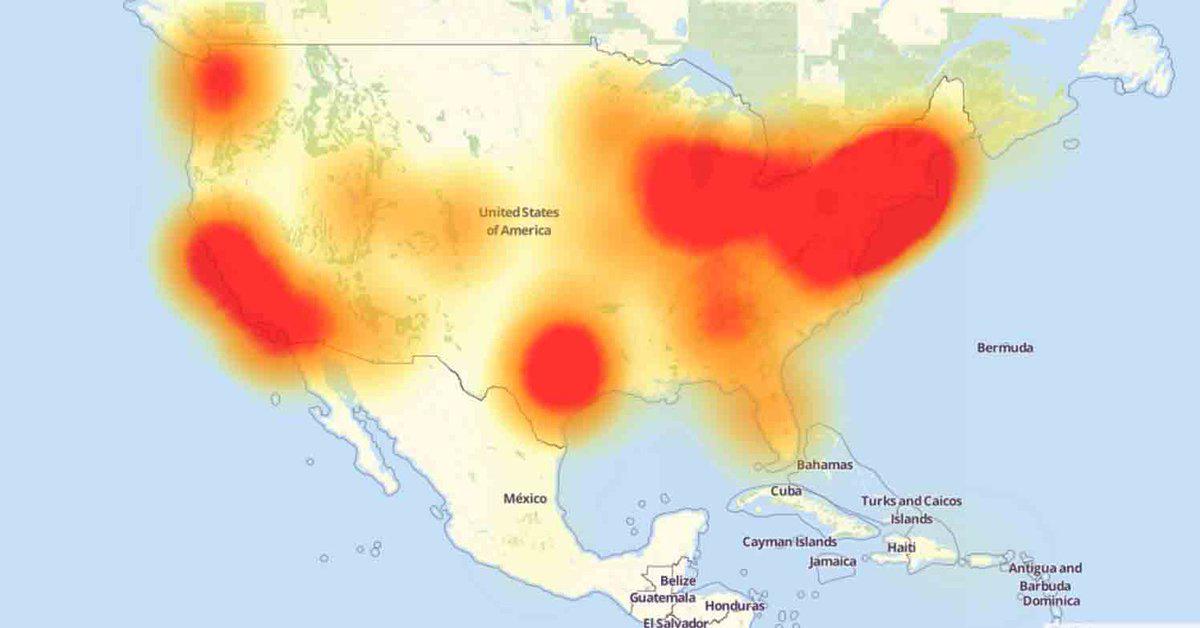
This morning at 7am ET a DDoS attack was launched at Dyn (the site is still down at the minute), an Internet infrastructure company whose headquarters are in New Hampshire. So far the attack has come in 2 waves, the first at 11.10 UTC and the second at around 16.00 UTC. So far details have been vague, though there are a number of theories starting to surface in the aftermath of the attack. The attack took down numerous websites including Twitter, Amazon, Spotify and Reddit for a period. PSN and Xbox live apps have also been affected!
11:10 UTC- We began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time.
12:45 UTC – This attack is mainly impacting US East and is impacting Managed DNS customers in this region. Our Engineers are continuing to work on mitigating this issue.
13:36 UTC – Services have been restored to normal as of 13:20 UTC.
16:06 UTC – As of 15:52 UTC, we have begun monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Our Engineers are continuing to work on mitigating this issue.
16:48 UTC – This DDoS attack may also be impacting Dyn Managed DNS advanced services with possible delays in monitoring. Our Engineers are continuing to work on mitigating this issue.
17:53 UTC – Our engineers continue to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure.
18:23 UTC – Dyn Managed DNS advanced service monitoring is currently experiencing issues. Customers may notice incorrect probe alerts on their advanced DNS services. Our engineers continue to monitor and investigate the issue.
18:52 UTC – At this time, the advanced service monitoring issue has been resolved. Our engineers are still investigating and mitigating the attacks on our infrastructure.
20:37 UTC – Our engineers continue to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure.
The attack has come only a few hours after Doug Madory, DYN researcher, presented a talk on DDoS attacks in Dallas at a meeting of the North American Network Operators Group (NANOG). Krebs on Security has also drawn links between reports of extortion threats posted on this thread, with the threats clearly referencing DDoS attacks – “If you will not pay in time, DDoS attack will start, your web-services will go down permanently. After that, price to stop will be increased to 5 BTC with further increment of 5 BTC for every day of attack.”
They do however, distance themselves from making any actual claims of extortion, “Let me be clear: I have no data to indicate that the attack on Dyn is related to extortion, to Mirai or to any of the companies or individuals Madory referenced in his talk this week in Dallas”
However, this isn’t the only theory circulating at the moment. Dillon Townsel from IBM security has tweeted:
John McAfee: ‘Iran hacked the DNC, and North Korea hacked DYN’ https://t.co/Dz0mIPRQuE pic.twitter.com/UnMvsHEJ8U
— Dillon Townsel (@DilTown) October 21, 2016
Heavy.com has reported that hacking group PoodleCorp are being blamed for the attack by Product-reviews.net because of the cryptic tweet that they posted 2 days ago, “October 21st #PoodleCorp will be putting @Battlefield in the oven”
PoodleCorp famously took down the Pokemon Go servers in July. Homeland Security and the FBI are investigating the attack and are yet to deem who was responsible.
Today’s attack is very different to the DDoS style that Anonymous rose to fame with. Instead of attacking and taking out an individual website for short periods of time, hackers took down a massive piece of the internet backbone for an entire morning, not once but twice with new reports of a potential 3rd wave. At the moment there have been no claims of ownership for the attack nor has there been any concrete evidence of who perpetrated the attack.
Dyn are well known for publishing detailed reports on attacks of this nature so we can only hope they will do the same for their own servers.
Until then you can follow any updates that Dyn are releasing here.
DDoS Attack – Update 10/24/2016
As of 22.17 UTC on October 21st Dyn declared the massive IoT attack, which had crippled large parts of the internet, to be over. However, details surrounding the attack are still emerging.
In the midst of the chaos, WikiLeaks tweeted this, “Mr. Assange is still alive and WikiLeaks is still publishing. We ask supporters to stop taking down the US internet. You proved your point.”
– suggesting that they knew who the perpetrators were. Perhaps even that they requested that attack, although this is pure speculation at this point.
A senior U.S. intelligence official spoke to NBC News, he commented that the current assessment is that this is a case of “internet vandalism”. At this point, they do not believe that it was any kind of state-sponsored or directed attack.
Hangzhou Xiongmai Technology, who specialise in DVRs and internet-connected cameras, said on Sunday that its products security Vulnerabilities inadvertently played a role in the cyberattack, citing weak default passwords in its products as the cause.
Security researchers have discovered that Malware known as Mirai was used to take advantage of these weaknesses by infecting the devices and using them to launch huge distributed denial-of service attacks. Mirai works by infecting and taking over IoT devices to create a massive connected network, which then overloads sites with requests and takes the website offline.
At this point we do not know when the identity of the hackers will become clear. Watch this page for more updates as they become available.
By Josh Hamilton





