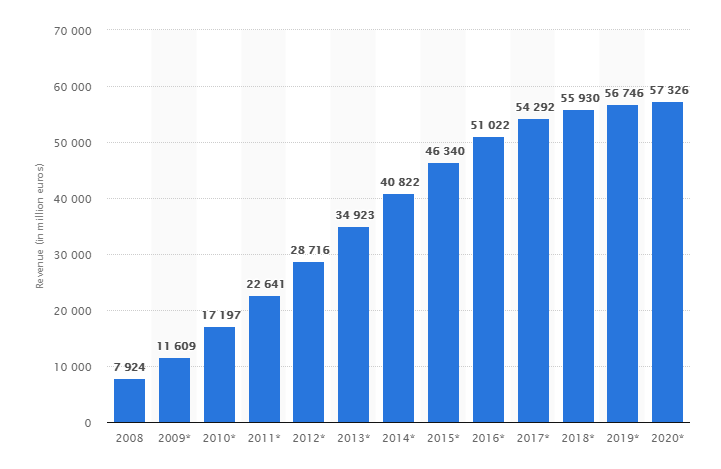
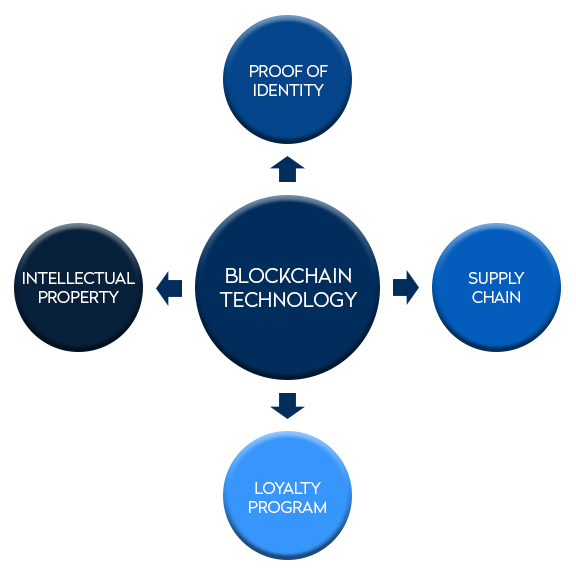
Migration Strategies and Their Impact on Security and Governance
Cloud Migration Strategies Public cloud migrations come in different shapes and sizes, but I see three major approaches. Each of these has very different technical and governance implications. Three approaches [...]